ATTACKING ACTIVE DIRECTORY | THE SCENARIO
Purpose
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It provides a centralized location for network administration and security, allowing administrators to manage and authenticate resources and users on a network.
It is widely used in the industry and therefore important for security professionals to have an understand of how attacks are made and how to detect them.
Scenario
Client ‘c2dragon’ has hired us to perform a penetration test on their Active Directory network. The objective of this penetration test is to find potential critical vulnerabilities on the AD server.
Another objective, however, is to test the resilience of the SOC team that is monitoring the situation. Vulnerabilities have been purposely been implemented on the AD server to test the readiness of the SOC team in the event of an attack/malicious behavior. Attacks should be detected via the Splunk SIEM and presented in an easily digestible format.
Implementation
In order for this scenario to play out, it must first be created with the following steps:
- Building the Network
- Installing and Configuring the Software
- Configuring Active Directory
- Creating the Vulnerabilities
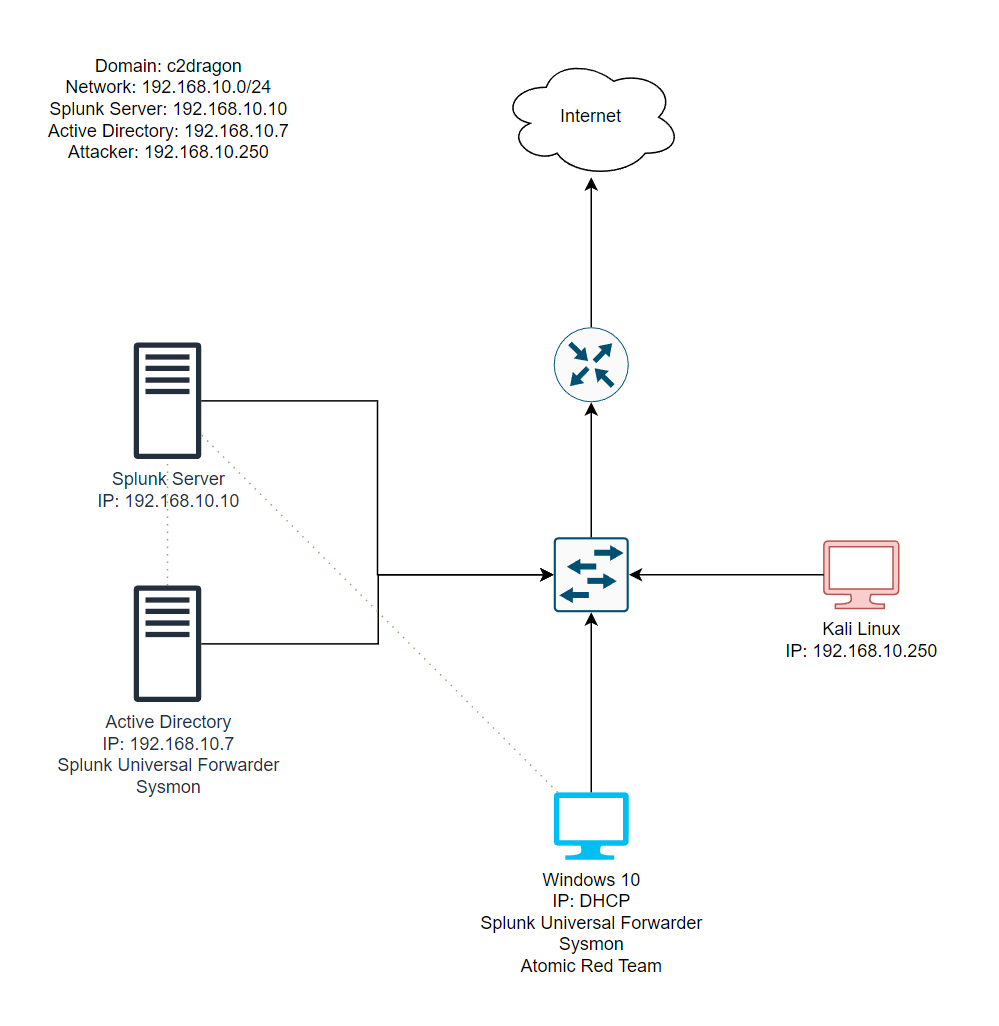
An Active Directory server and Splunk server will be placed on the same network, along with a Windows 10 machine to capture the data. A Kali Linux machine will be used as the attacker machine for the penetration test and will be placed on the same network as well.
Exploitation
After creating the network, installing the software, and implementing the vulnerabilities, the penetration test portion of the scenario begins.
Exploitation of the found vulnerabilities will be demonstrated in the form of a penetration test report.
Detection
Detecting the attacks as soon as possible is the goal of the SOC analyst team.
Splunk will be the SIEM of choice. And detections are to be presented in a digestible format.