ATTACKING ACTIVE DIRECTORY | CONFIGURING VULNERABILITIES
Objective
There are many different types of vulnerabilities we can explore when attacking Active Directory. This can range from anywhere from cleartext passwords to ‘pass the hash’ attacks.
On the target machine, one of the vulnerabilities is already in place. User John Doe, is using a weak password of ‘password123!’. Not only that, but Jane Doe is reusing the same password. Perhaps they are a married couple sharing passwords.
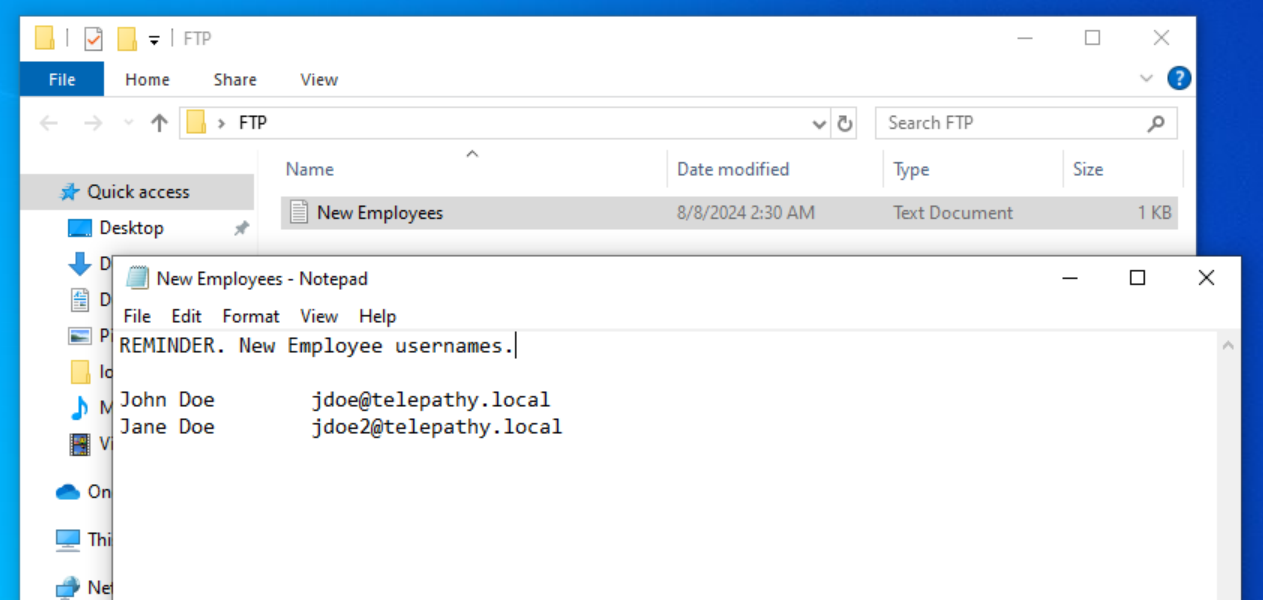
Anyways, RDP and FTP will also be enabled on the machine. RDP will give GUI access to the target machine and FTP will hold a sensitive file containing the usernames to the 2 previously mentioned users.
On the Domain Controller, we will set up a Kerberoastable account. This will be a service account that will supply the SPN encrypted password to the attacker via the Kerberos vulnerability. The password will be weak as well.
Implementation
Weak Credentials
This part has already been set up in the previous blog. When adding user John Doe and Jane Doe, they were created using a weak password. Any weak password will do. They currently share the weak password of ‘password123!’
Setting up RDP
We will enable RDP on the ‘TARGET-PC’.
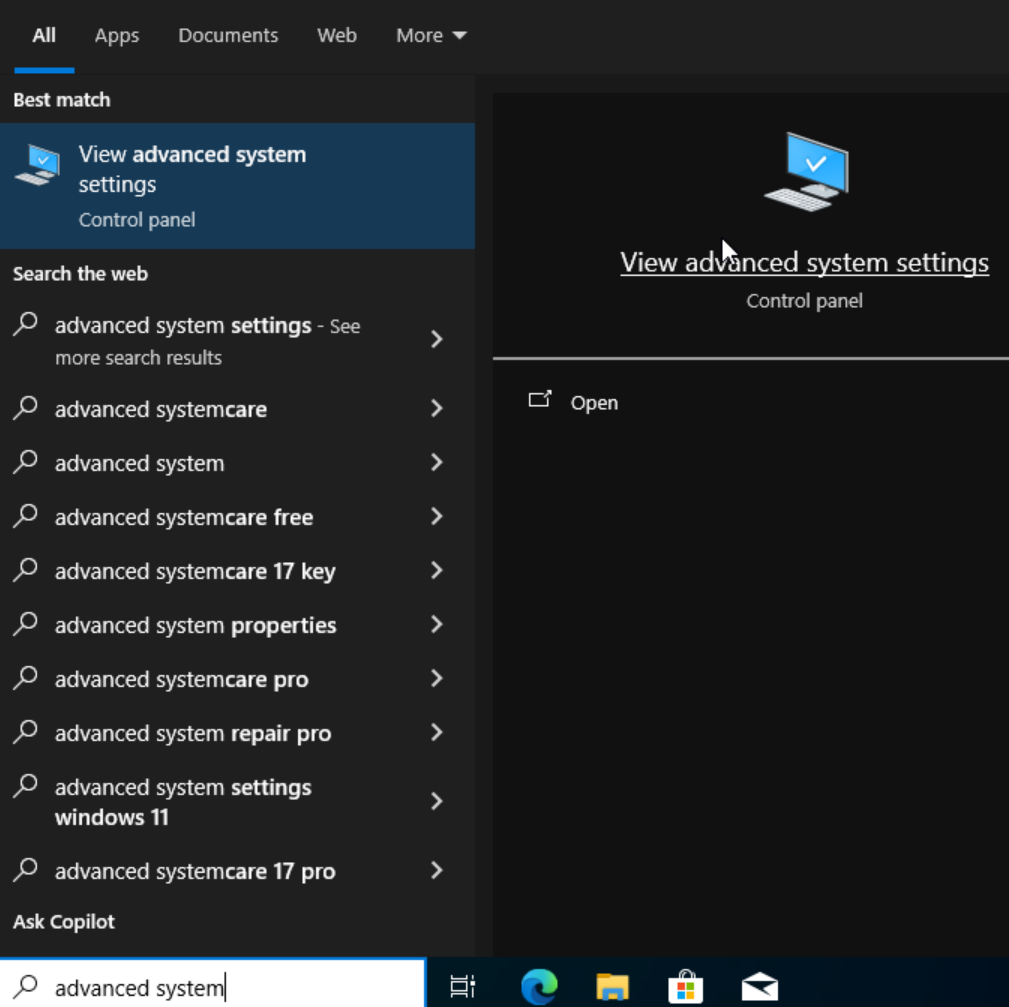
To enable RDP, search for ‘advanced system settings’ in the start menu.
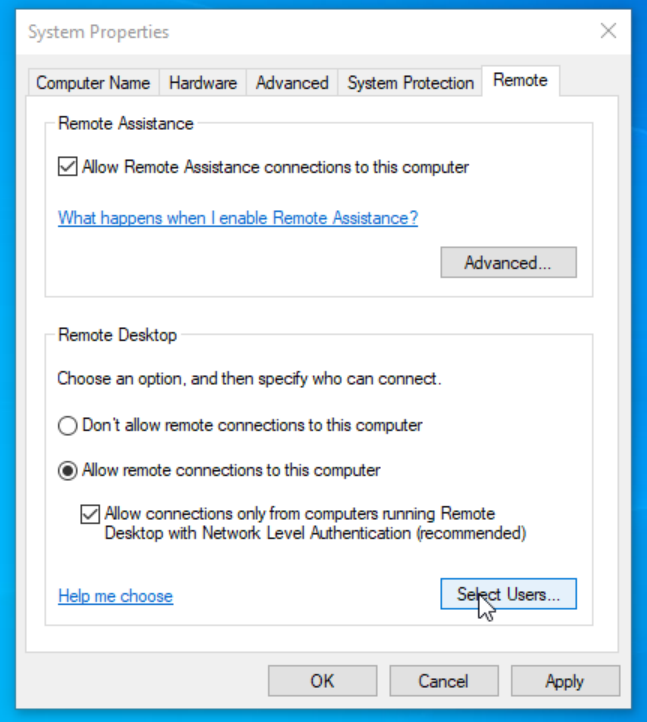
Check the circle that says ‘Allow remote connections to this computer’, then click on ‘Select Users’.
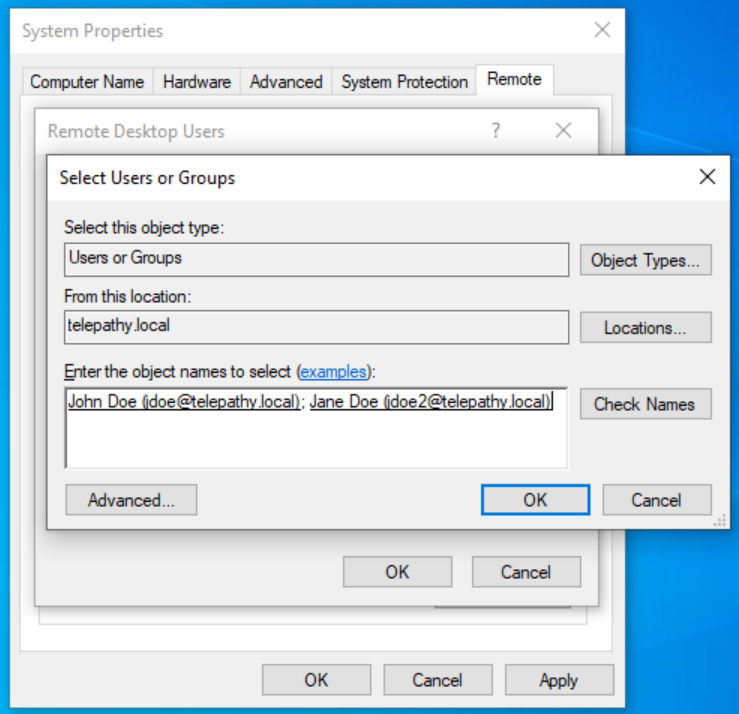
Click ‘Add’.
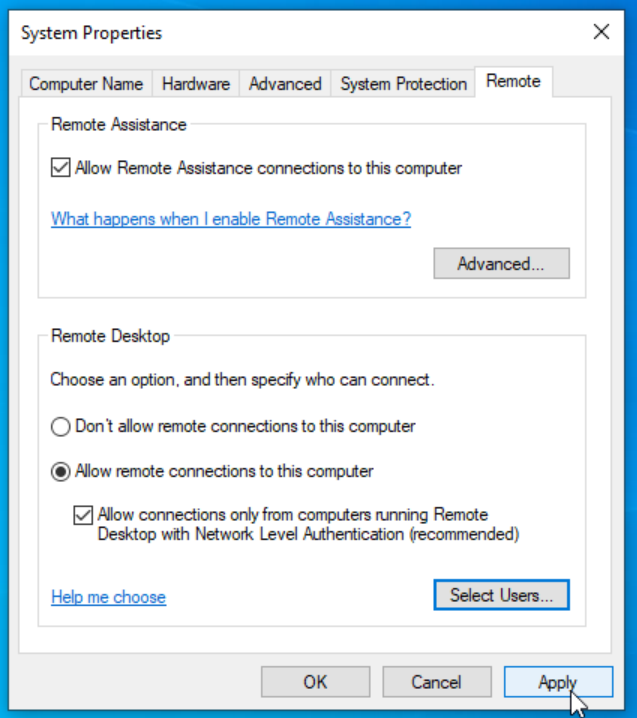
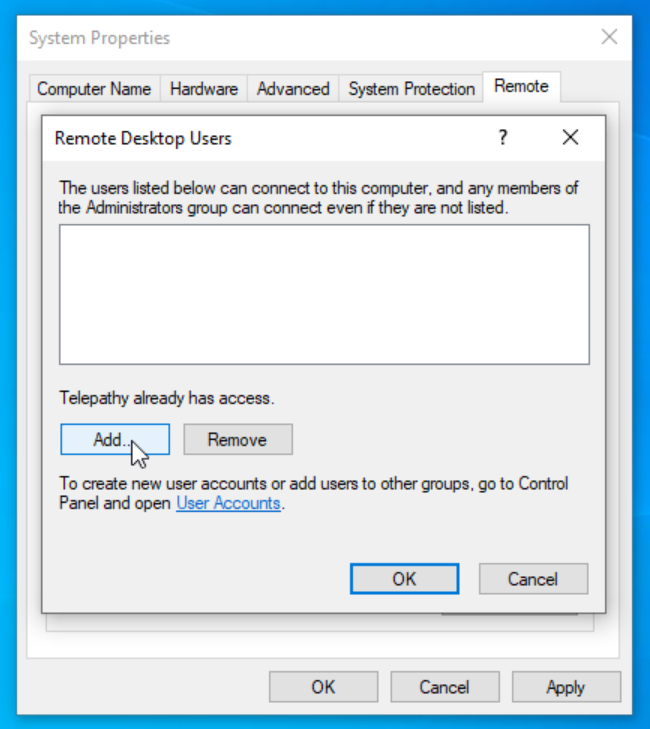 Sign in as administrator when prompted and add John Doe and Jane Doe. Click ‘Okay’ then ‘Apply’.
Sign in as administrator when prompted and add John Doe and Jane Doe. Click ‘Okay’ then ‘Apply’.
Restart the computer.
Setting up FTP
Install the FTP server.
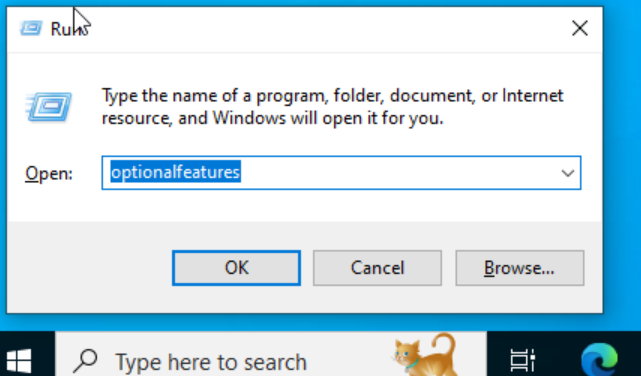
Press the Windows button + R. Type “optionalfeatures”.
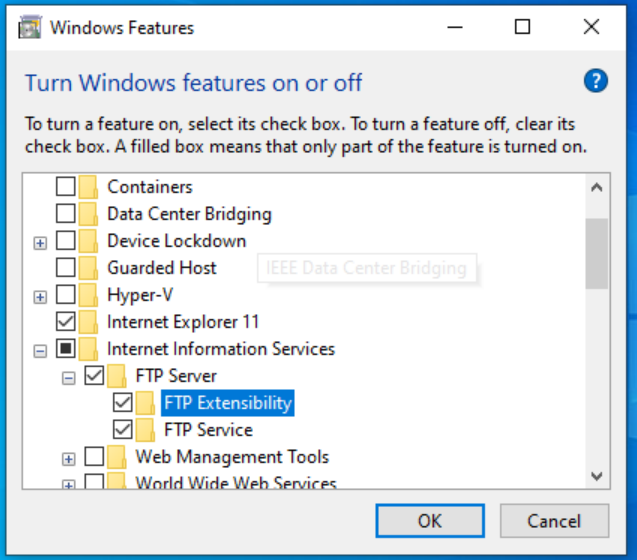
Check the “Internet Information Services box”. Check everything in FTP Server and World Wide Web Services. Web Management Tools check “IIS Management Scripts and Tools” and “IIS Management Console.”
Create an FTP directory and create a text document holding the sensitive usernames. Move the folder into the desired directory.
Press the Windows button + R. Type “inetmgr”.
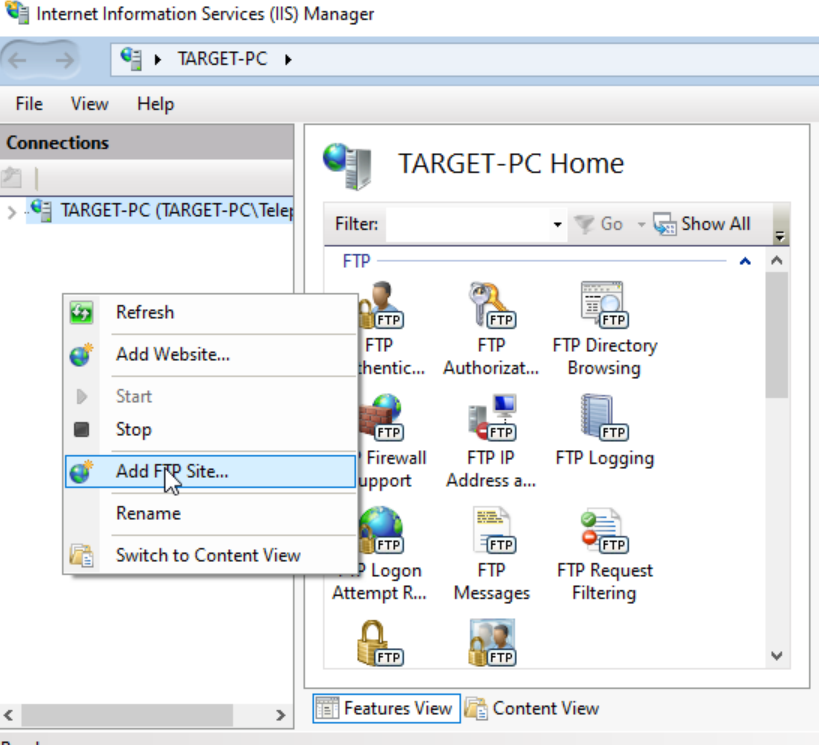
Right click on the sites on the left hand side and ‘Add FTP Site’.
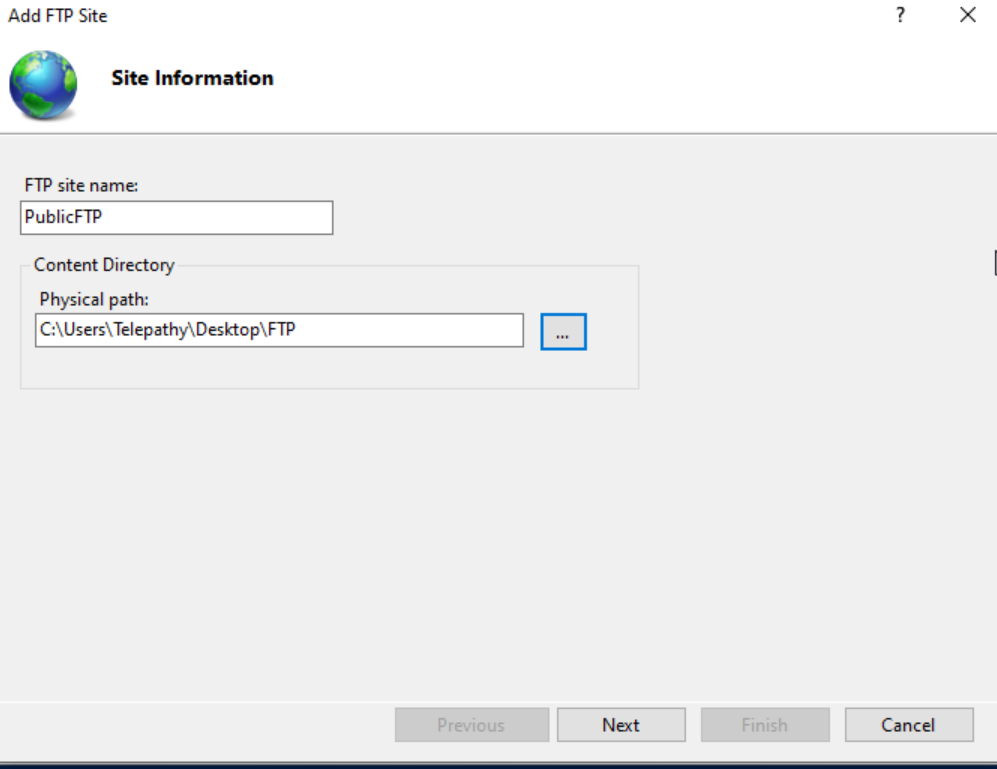
Name it and point to the directory of the FTP folder.
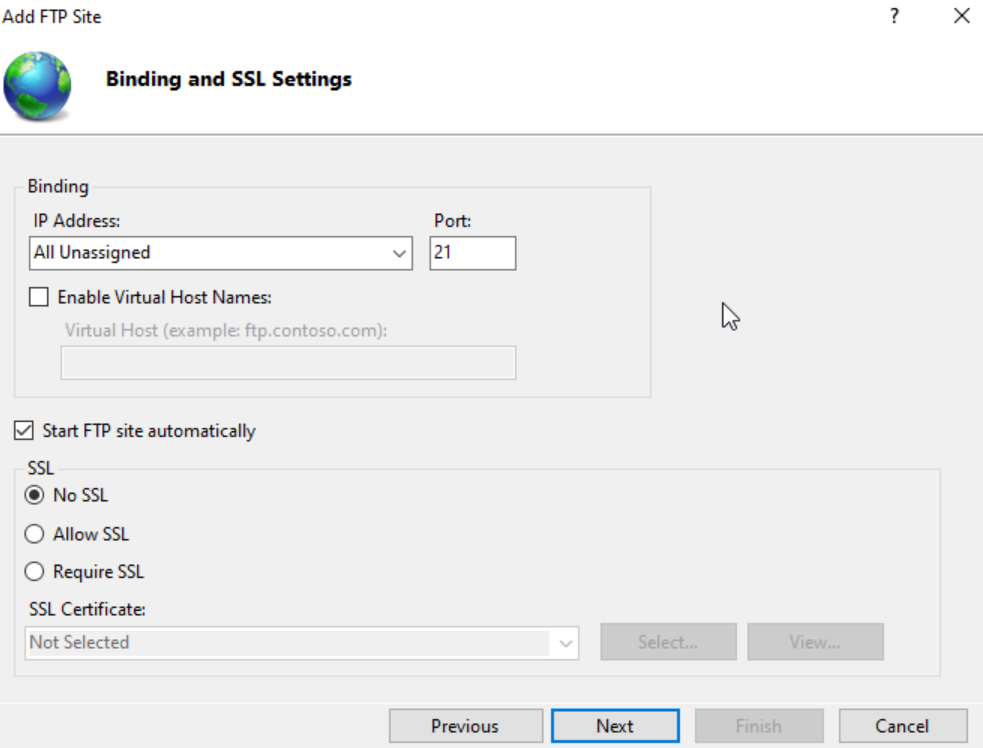
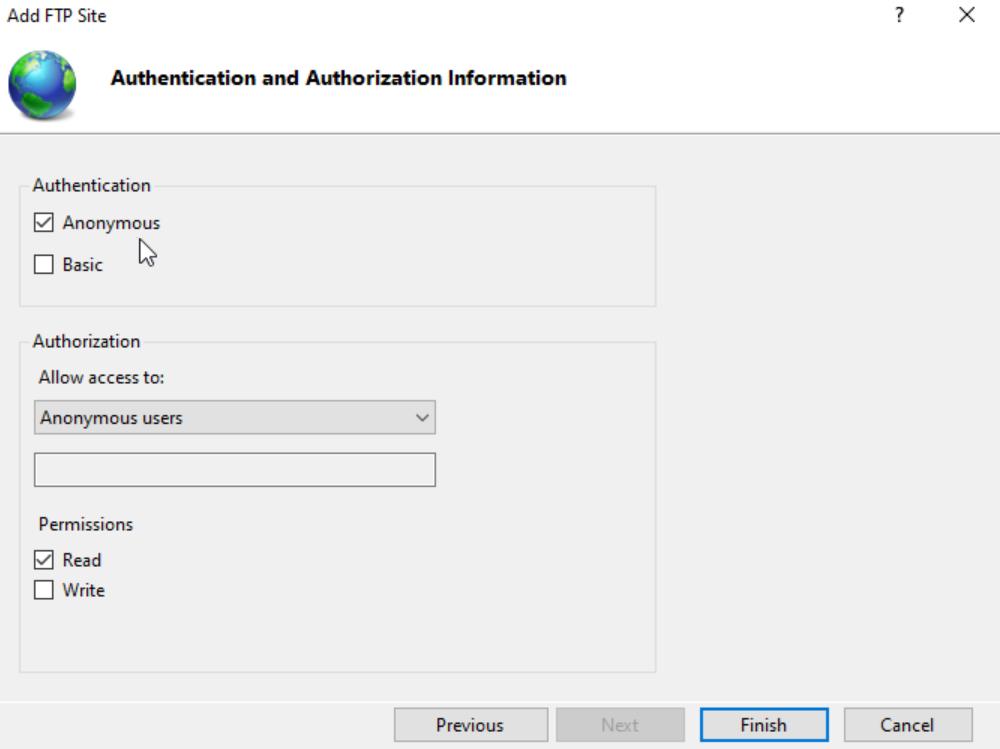
Change the SSL settings to ‘No SSL’.
Allow anonymous access with read permissions.
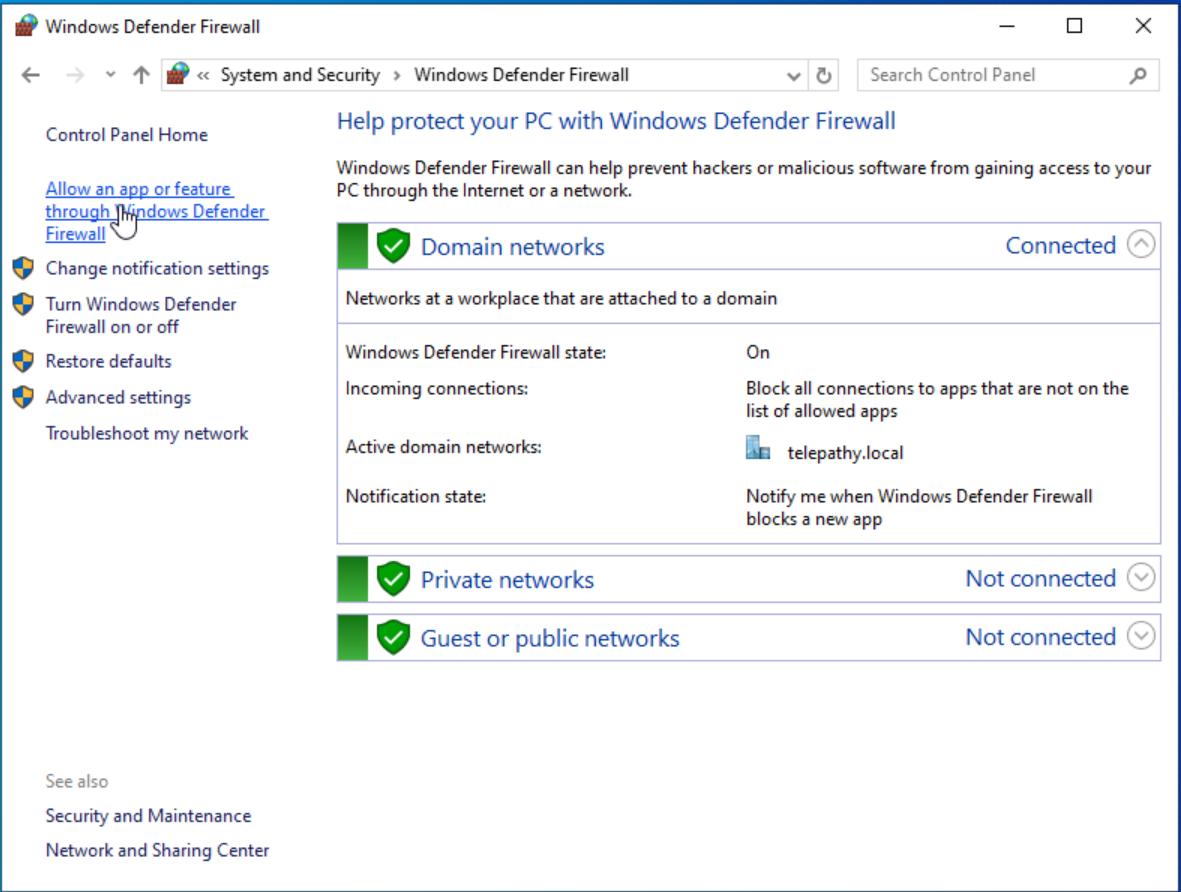
Change the fire wall settings. Open up ‘Windows Defender Firewall’ from the start menu and navigate to ‘Allow an app or feature’.
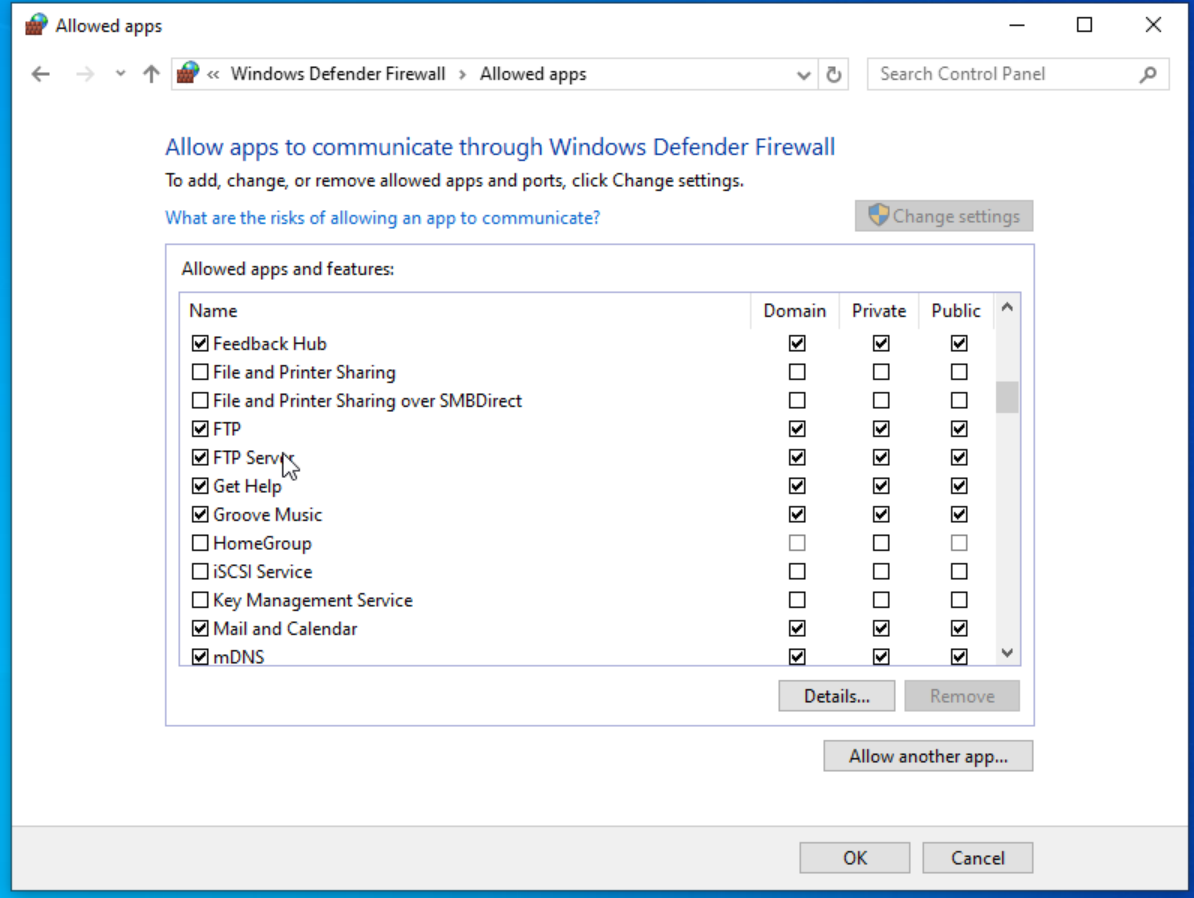
Change setting and check off FTP server for Domain, Public, Private.
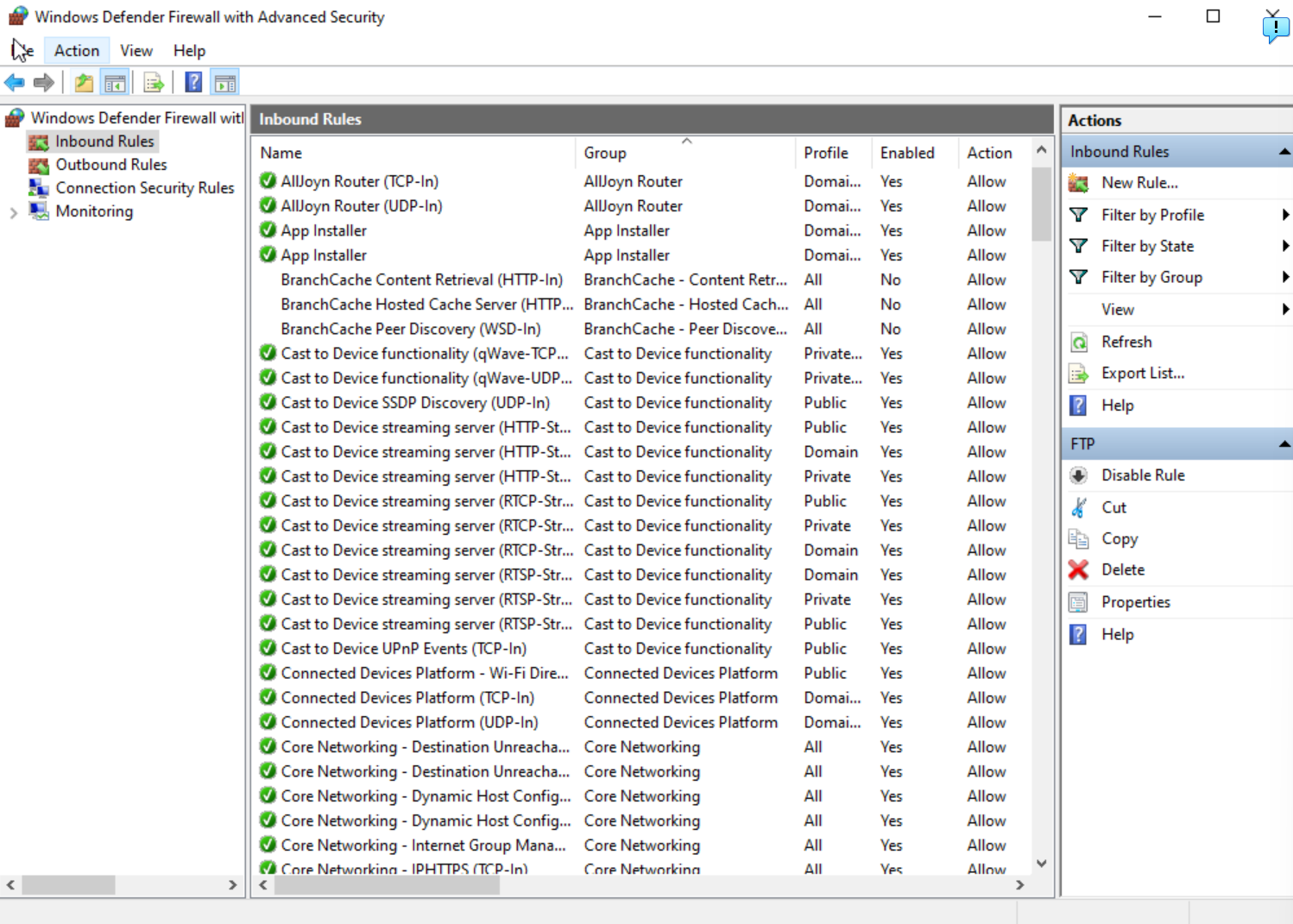
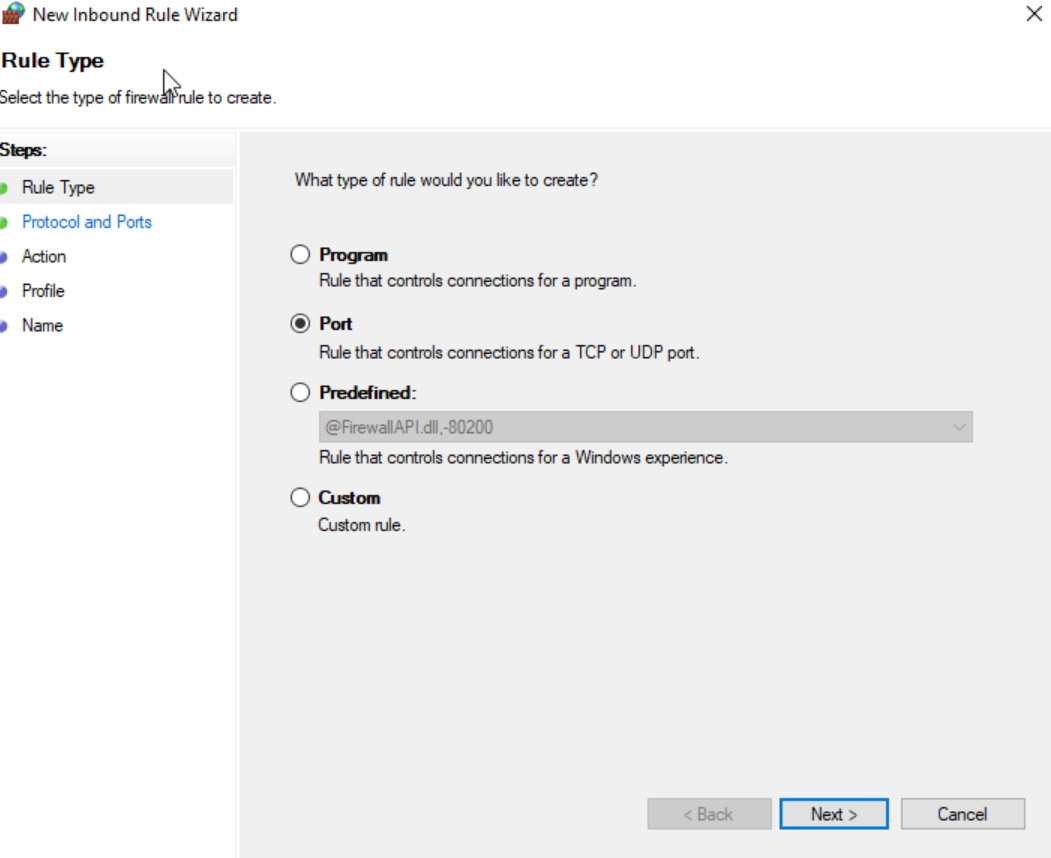
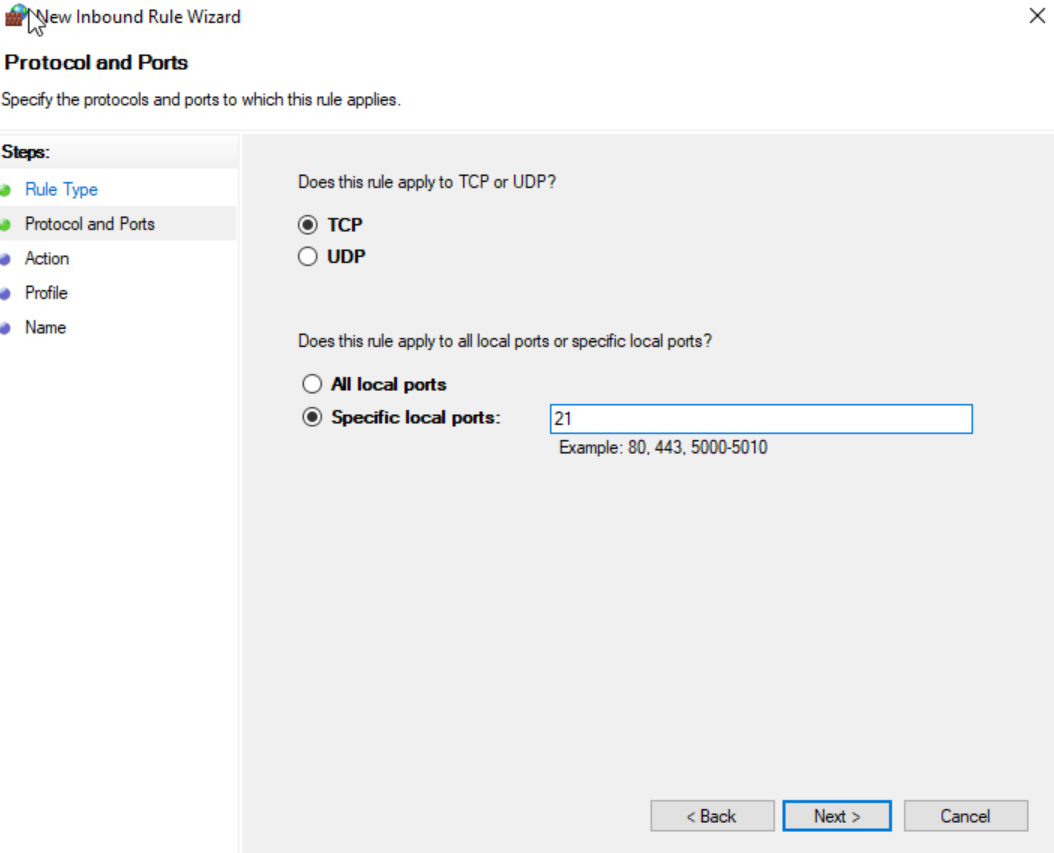
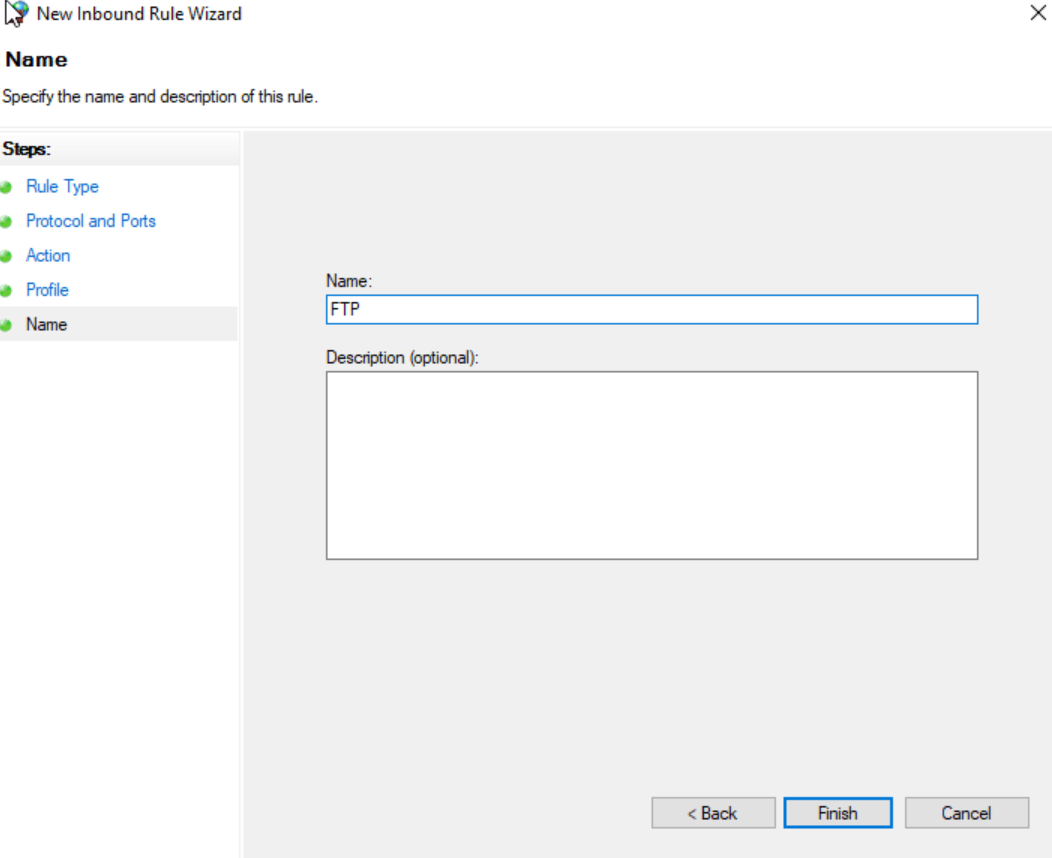
Back in ‘Windows Defender Firewall’, go to advanced settings. Click on ‘Inbound Rules’ then ‘New Rule.. ‘ and add a new root to allow inbound port 21 traffic.
We will also turn off Windows Defender for this demonstration which is done by going to ‘Windows Security’ then ‘Antivirus detection’ then turn it off.
Setting up a Kerberoastable Account
There are a few different ways to set up a Kerberoastable Account. One method is using the GUI. For this demonstration, I will be adding the account via the PowerShell command line.
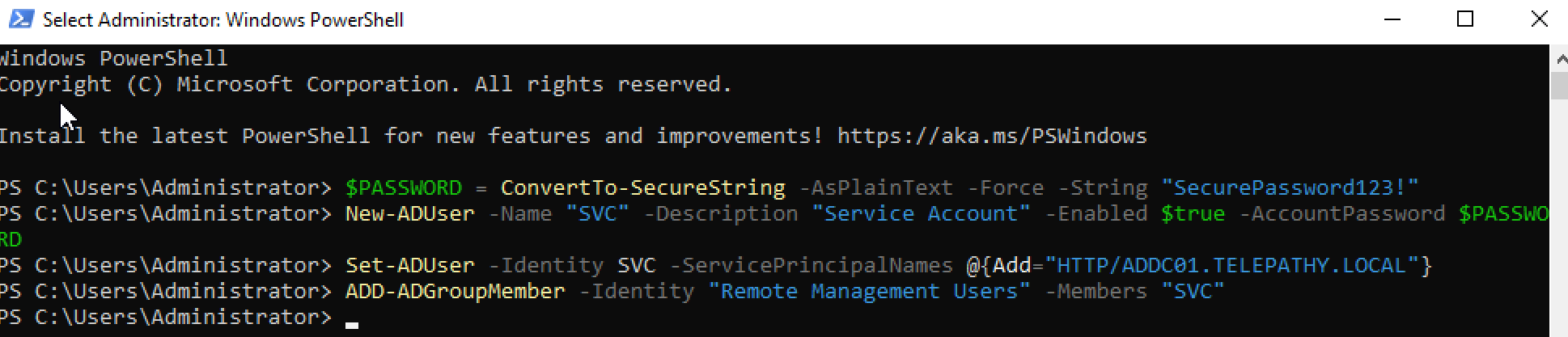
Open up a PowerShell command prompt as administrator on the Domain Controller. Create a Kerberoastable service account using the following set of commands:
1
$PASSWORD = ConvertTo-SecureString -AsPlainText -Force -String "SecurePassword123!"
1
New-ADUser -Name "SVC" -Description "Service Account" -Enabled $true -AccountPassword $PASSWORD
1
Set-ADUser -Identity SVC -ServicePrincipalNames @{Add="HTTP/ADDC01.TELEPATHY.LOCAL"}
1
ADD-ADGroupMember -Identity "Remote Management Users" -Members "SVC"
We have now configured the vulnerabilities. The environment is now ready to be exploited.