ATTACKING ACTIVE DIRECTORY | DETECTING ATTACKS WITH SPLUNK
Purpose
Now that the penetration test is finished, we will be able to utilize the logs generated to analyze the attack. The 2 main attacks that generated telemetry were the RDP brute-forcing attack and the Kerberoast attack launched using ‘jdoe’s account.
Splunk/SPL
Initial Investigation
Start by navigating to the Splunk server on one of the network computers.
1
192.168.10.10:8000
Login with the credentials and go to Splunk’s search platform.
Change the time to ‘All time’.
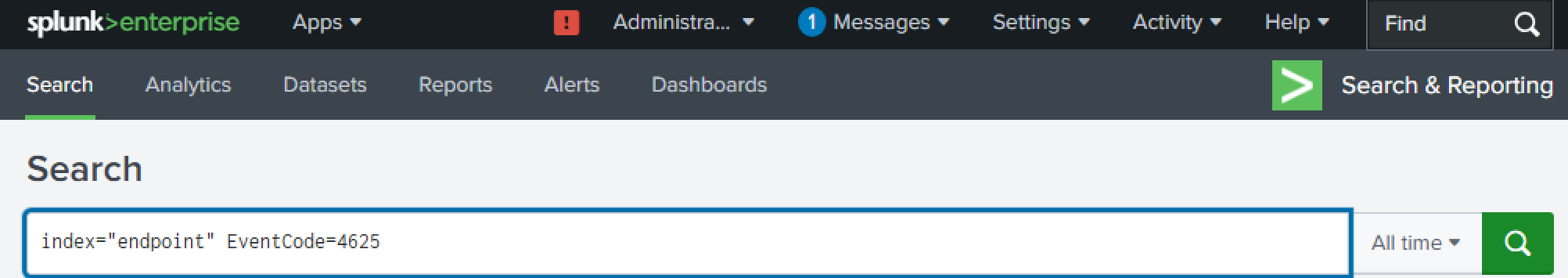
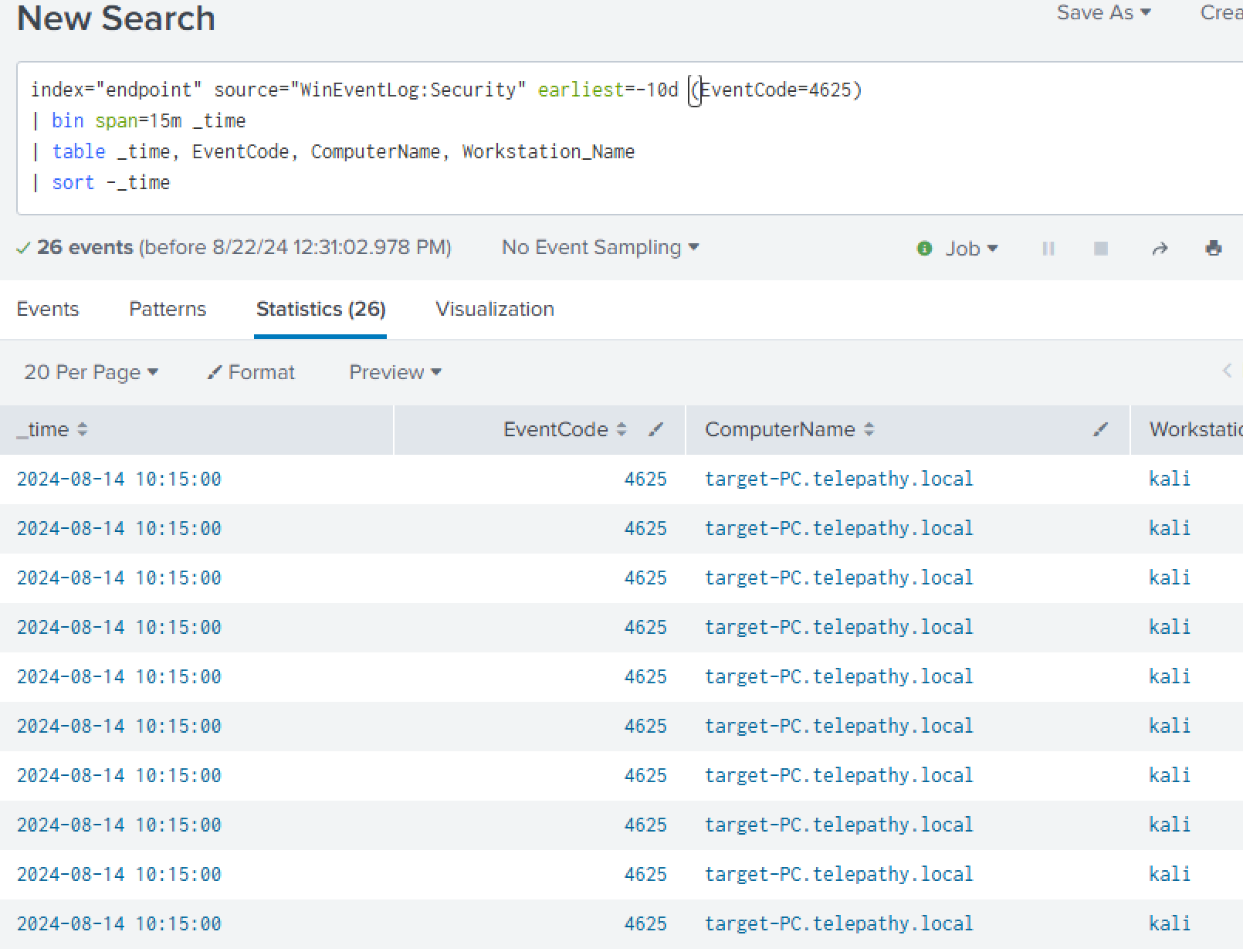
We will now begin by investigating the login attempts. Event Code 4625 is the event that is generated by Windows Event Logs when there is a failed login attempt made. We will set the index to ‘endpoint’ (The one we configured when setting up Splunk).
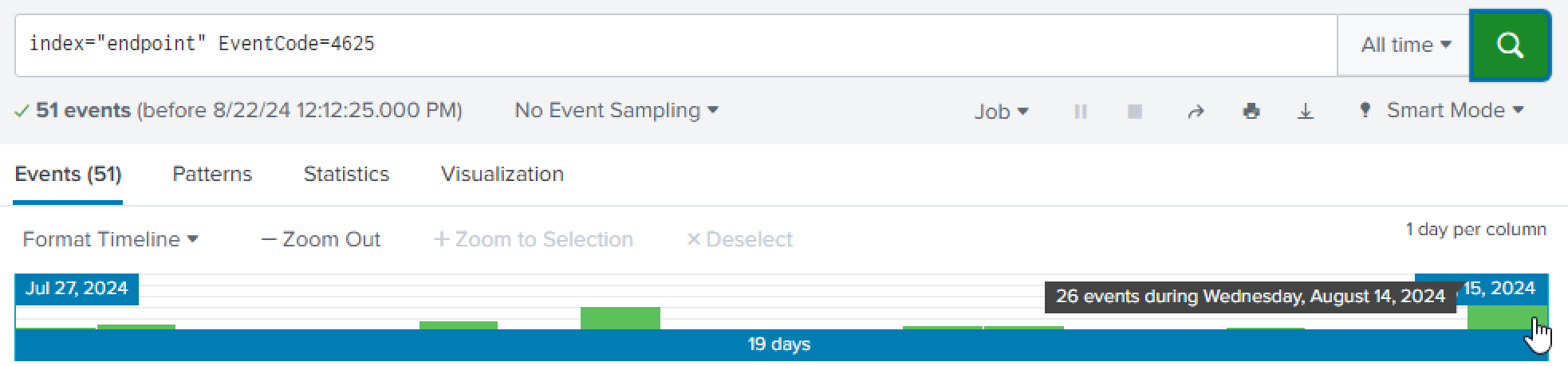
Looking at the events there seems to be a large number, 26, of events for 4625 on August 14.
Brute-force Login Attempts
We will further analyze this utilizing SPL.
Dissecting the query from above:
‘bin’ splices the time into manageable segments. In this case 15 minutes.
1
| bin span=15m_time
‘table’ generates a table with the specified fields. In this case the ‘EventCode’, ‘ComputerName’, and ‘Workstation_Name’ fields.
_time will display when the event occurred. (Since we’re using ‘bin’ it will be in increments of 15 minutes)
‘EventCode’ will display the event code which will only be 4625 in this query.
‘ComputerName’ will display the computer name which will be either ‘target-PC’ or ‘ADDC01’.
‘Workstation_Name’ will display the computer trying to authenticate.
1
table _time, EventCode, ComputerName, Workstation_Name
‘Sort’ will sort the data. In this case we specify by time.
1
sort -_time
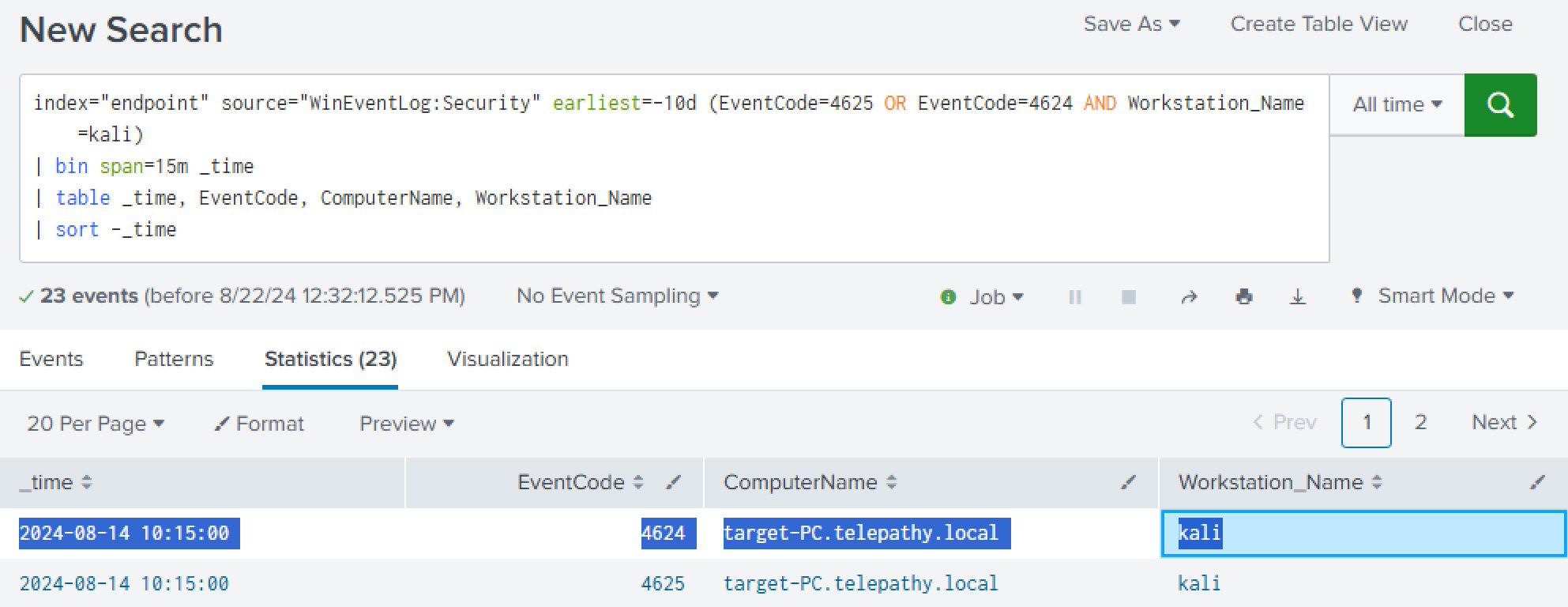
Adding to the query above, we can see successful login events with ‘EventCode=4624’. We will also specify that the workstation needs to be ‘kali’.
1
(EventCode=4625 OR EventCode=4624 AND Workstation_Name=kali)
Unfortunately it looks like the suspected Kali Attacker Machine successfully logged into the ‘target-PC’ as shown in the table results.
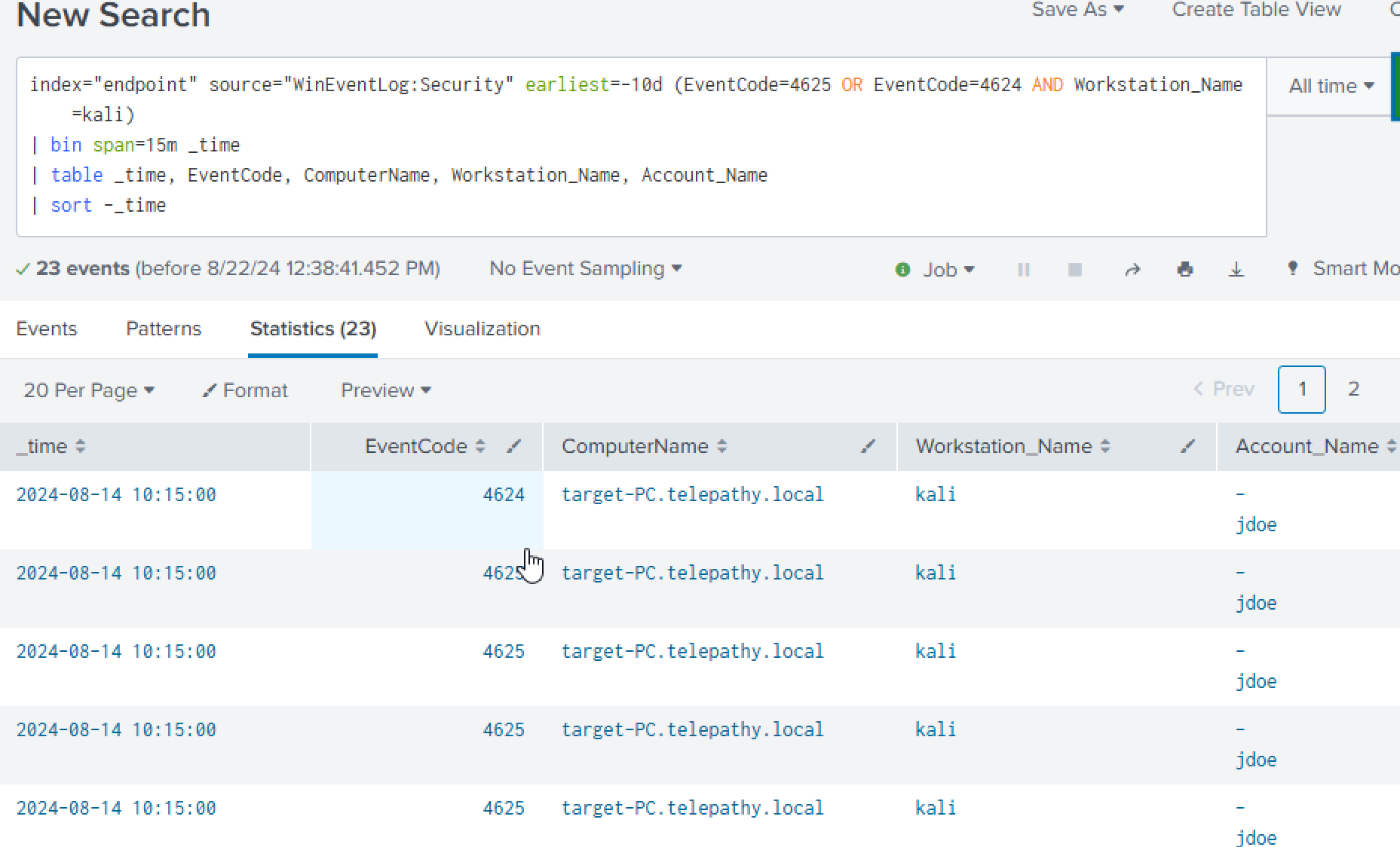
We can see what user by adding an additional field to the table: Account_Name.
1
Account_Name
It looks like the successful brute-force attempt was against the user ‘jdoe’.
Kerberoast
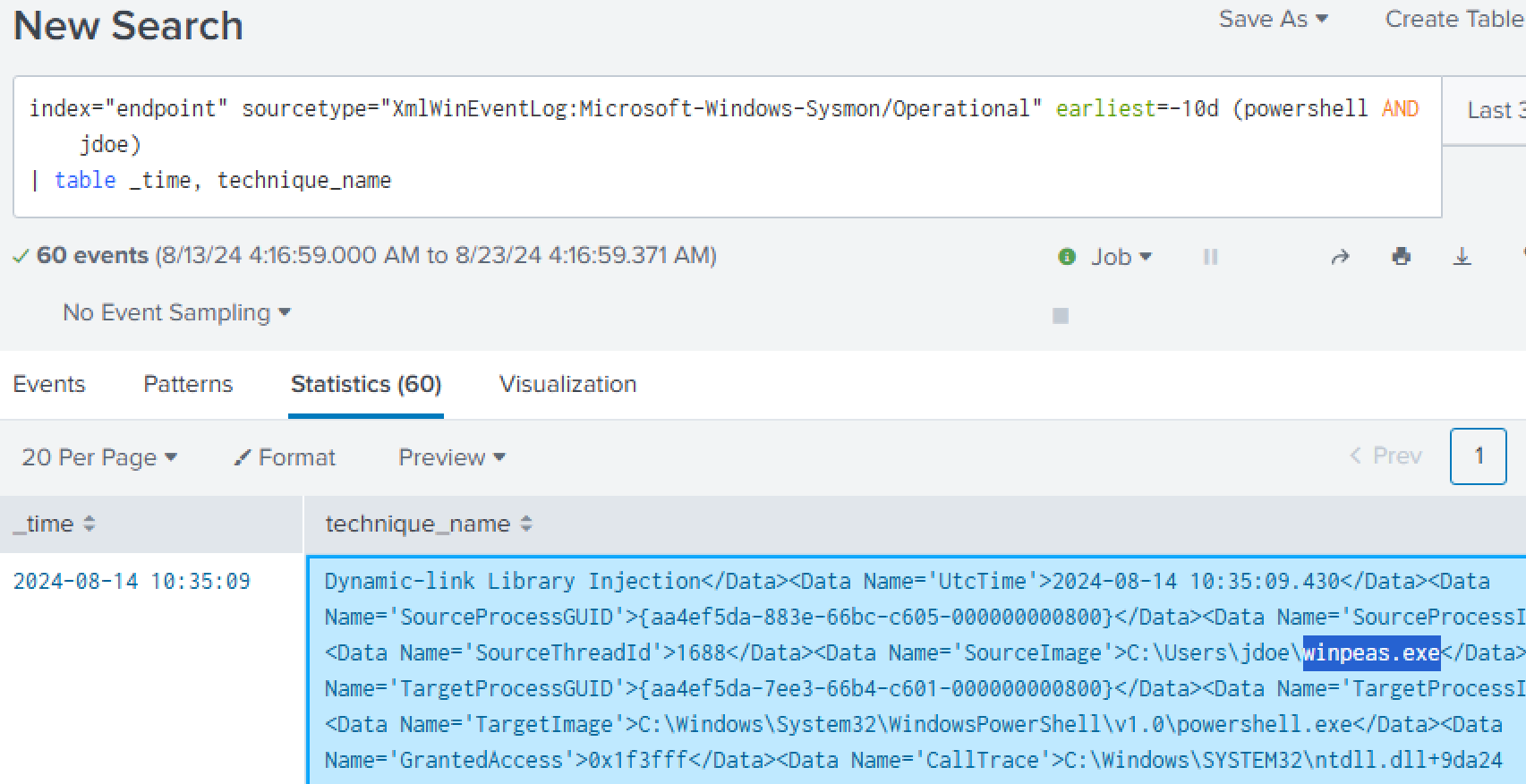
We will attempt to see what powershell commands the attacker used on the system.
This time using the Sysmon source, we can see that the attacker ran ‘winpeas.exe’. We can be sure that this is very likely the attacker trying to find avenues for privilege escalation on the target-PC.
No that we know that the attacker has access to the ‘jdoe’ account, one of the attacks that he could attempt to perform is kerberoasting.
A popular method to perform this attack is by using a well known binary called ‘rubeus.exe’. It can be discovered by seeing if ‘rubeus.exe’ was used.
Unfortunately it looks like rubeus was run on the machine. Indicating that there was likely Kerberoasting or ASReproasting attempt.
Analysis
From the information gathered, we can deduce that the system was attacked.
The attacker used a Kali Linux machine as the attacking machine.
Performed a brute-force login attempt to our computer named ‘target-PC’.
The attacker tried and was successfully logged on as user ‘jdoe’.
The attacker performed system enumeration via ‘winpeas.exe’ script.
The attacker then likely performed a Kerberoast or ASReproasting attack using ‘jdoe’s account and ‘rubeus.exe’.
Final Thoughts
Without the penetration test report, it could be somewhat difficult for us to find out how the attacker got a hold of the usernames. It would take additional investigation to realize that there was sensitive information within file residing within the FTP server.
Since this was just a simulation, turning off Windows Defender would likely not happen in the real world. Tools like Rubeus would easily be flagged and restricted without administrative privileges. More stealthier approaches would need to be followed in order to by pass that.
A truly malicious attacker, such as an APT (advanced persistent threat), would likely take greater measures to hide their tracks. Network scans might be done over a much longer period and only target specified ports, making it near impossible to distinguish from real traffic. Multiple attacker machine might be utilized to further obfuscate malicious behavior.
For these reasons, to be a good defender, it is pertinent to have a deep understanding of an attackers mindset and the tools they have at their disposal. Likewise, sophisticated threat actors will have deep knowledge of what tools defender have at their disposal and act accordingly not to be caught.